1-ASKA Overview-1 20241031
Written by: Paul Lowndes <[email protected]>
Table of Contents
Diagram 1: Detailed Description
Diagram 3: User Interface Data Flow
Description for Diagram 3: User Interface Data Flows
Diagram 4: Dynamic Trust Gateway (DTG) Architecture
Description for Diagram 4: Dynamic Trust Gateway (DTG) Architecture
Diagram 5: ASKA Detailed Overview
Description for Diagram 5: ASKA Detailed Overview
Diagram 6: Security Monitoring and Response
Description for Diagram 6: Security Monitoring and Response
Diagram 7: Key Management and Recovery
Description for Diagram 7: Key Management and Recovery
Diagram 8: Zone Management and Inter-Zone Communication
Description for Diagram 8: Zone Management and Inter-Zone Communication
Diagram 9: Data Flow and Security Processes
Description for Diagram 9: Data Flow and Security Processes
Diagram 10: Bootstrapping and Attestation
Description for Diagram 10: Bootstrapping and Attestation
Diagrams 11a and 11b: Security Meshes
Description for Diagrams 11a and 11b: Security Meshes
Current Data Flow (with Feedback Loop):
Review of the Security Mesh hierarchy
Diagram 11c: Security Mesh Integration
Description for Diagram 11c: Security Mesh Integration
Diagram 12a: Configuration Management and Deployment
Description for Diagram 12a: Configuration Management and Deployment
Diagram 12b: Configuration Management Module (CMM) Internals
Description for Diagram 12b: Configuration Management Module (CMM) Internals
Diagram 13: Error Handling and Logging
Description for Diagram 13: Error Handling and Logging
Description for Diagram 14a: Onboard AI Agent
Diagram 14b: Onboard AI Agent Update Process
Description for Diagram 14b: Onboard AI Agent Update Process
Diagram 14c: Onboard AI Agent Security System Integration
Description for Diagram 14c: Onboard AI Agent Security System Integration
Description for Diagram 15: BCI Integration
Diagram 16a: Remote UI Session
Description for Diagram 16a: Remote UI Session
Diagram 16b: Remote UI Integration
Description for Diagram 16b: Remote UI Integration
Building Trust from the Ruins of Broken Promises.
ASKA (Adaptive Secure Kernel Architecture) is a hardware-rooted secure computing architecture designed for high-assurance operation in complex environments, particularly relevant for the age of AGI. It addresses vulnerabilities in current architectures by employing modularity, hardware-enforced isolation, dynamic adaptability, and decentralized governance. This overview details its core components, referencing the described patent innovations.
1. Core Components and Technologies:
2. Key Relationships and Interactions:
The components of ASKA interact closely to provide comprehensive security. AESDS updates the STN, DTG, and core components. DTMS provides trust levels and access control policies to various components. STN and DTG interact for secure data handling. The ASKA Hub orchestrates and manages all components. The decentralized ledger provides a tamper-proof audit trail. MDATS correlates digital logs with physical microstructures. MSM monitors system-wide security. HESE-DAR provides secure data storage. SHVS manages secure collaboration. SIZCF facilitates inter-zone collaboration. The Resource Manager and Capability Manager dynamically allocate resources and capabilities based on DTMS trust levels and TRCs. The Policy Engine enforces policies throughout the system. AI engines provide predictive analysis and automation. Quantum-resistant communication secures network channels. ZKEE enables secure private computation. The Secure UI Kernel provides secure user interaction. The Chiplet Architecture enables dynamic hardware integration. Secure Boot verifies system integrity.
3. Supporting Technologies:
ASKA relies on a number of supporting technologies, including Secure Boot (P1), Data Diodes (P2), Multi-Factor Authentication (P23), Secure UI Kernel (P11), Chiplet Architecture (P12), Decentralized Ledger (P13, P15), MDATS (P17), Secure Hyper-Virtualization (P18), Federated Learning (P19), Secure Data Enclaves (P20), and SIZCF (P22). SCION routing (P2, P3, P5, P16, P28) underpins secure communication and update distribution.
The following patents underpin ASKA's innovative capabilities:
Patent 1: Modular Isolated Execution Stacks with Hierarchical Zones, Decentralized Trust Management, and Capability-Based Inter-Component Communication - Creates isolated execution environments (IES) with hierarchical zones for granular security. Uses mini-TRCs for localized trust and capability-based communication for secure inter-IES data sharing. Supports dynamic partitioning for flexible resource allocation.
Patent 2: Secure Inter-IES Communication System with Dynamically Reconfigurable Capabilities, Declarative Policies, and Adaptive Security - Establishes secure communication between IES instances using data diodes for unidirectional data flow and capability-augmented PCFS for bidirectional communication. Employs a hierarchical security mesh and declarative policies for adaptive security.
Patent 3: Adaptive Multi-Channel Network with Declarative Policy Enforcement and Capability-Aware Forwarding - Creates a secure and adaptable network with physically segregated channels, managed by a Channel Manager. Uses declarative policies and capability-aware forwarding for fine-grained access control and dynamic traffic management. Integrates legacy systems securely.
Patent 4: Dynamic Trust Management System (DTMS) with Decentralized Zone Management and TRC-Based Trust - Establishes and manages trust relationships between IES instances and across zones using TRCs. Employs dynamic trust metrics, decentralized zone management, and distributed consensus for secure and adaptable trust.
Patent 5: Quantum-Resistant Secure Communication with Path-Aware Key Distribution, Dynamic QKD Endpoint Discovery, and SIBRA Bandwidth Reservation - Implements quantum-resistant communication using QKD, DKM, and PQC. Features path-aware key distribution, dynamic QKD endpoint discovery, and SIBRA bandwidth reservation for secure and resilient communication.
Patent 6: Zero-Knowledge Execution Environment with Decentralized Verification and Zone-Based Trust - Enables private computation on encrypted data within a Zero-Knowledge Execution Environment (ZKEE). Uses zero-knowledge proofs and decentralized verification for secure and verifiable computation.
Patent 7: Hardware-Enforced Anomaly Detection, Isolation, and Self-Healing with Secure SCMP Reporting, Zonal Response Policies, and Timing Side-Channel Detection - Provides hardware-enforced anomaly detection, isolation, and self-healing capabilities. Uses secure reporting, zonal response policies, and timing side-channel detection for proactive security.
Patent 8: Hardware-Based Memory Protection with Capability-Based Access Control and Dynamic Obfuscation - Secures memory through dynamic obfuscation, hardware-enforced segmentation, and real-time verification. Employs capability-based access control and an ORAM-like design for enhanced protection against various attacks.
Patent 9: Secure Resource Borrowing and Granular I/O Management with TRC-Based Policies, Multipath Communication, and Hardware-Enforced Isolation - Enables secure resource borrowing between IES instances and granular I/O management for shared peripherals. Uses TRC-based policies, multipath communication, and hardware isolation for secure resource access.
Patent 10: AI-Powered Predictive Resource Allocation and Adaptive Scaling for IES with Multipath Optimization, Declarative Policies, and Secure Sharing - Implements AI-powered predictive resource allocation and adaptive scaling for IES instances. Uses multipath optimization, declarative policies, and secure sharing for efficient resource management.
Patent 11: Secure UI Kernel with Zonal Isolation, Hardware-Enforced Control-Flow Integrity, and Declarative Policy-Based Rendering - Creates a secure UI kernel with hardware and zonal isolation. Employs hardware-enforced CFI, declarative policies, and secure communication for a protected user interface environment.
Patent 12: Secure and Adaptive Chiplet Architecture with Dynamic Resource Allocation, Capability-Based Access Control, and Hardware-Enforced Isolation - Defines a secure and adaptive chiplet architecture for integrating specialized hardware components. Employs dynamic resource allocation, capability-based access control, and hardware isolation for secure and flexible system design.
Patent 13: Secure and Transparent Zonal Governance System with AI-Driven Authentication, Decentralized Ledger, and Secure Boot Integration - Establishes a secure zonal governance system with AI-driven authentication. Uses a decentralized ledger, secure boot integration, and privacy-preserving techniques for secure and transparent governance.
Patent 14: 3D-Printed Microstructure Audit Trail for Citizen Voting System - Creates a tamper-evident audit trail using 3D-printed microstructures. Each microstructure has unique identifiers linked to digital records, ensuring verifiable and auditable processes.
Patent 15: AI-Powered Governance Auditing and Transparency with TRC Monitoring and Automated Conflict Resolution - Implements AI-powered governance auditing and transparency. Monitors TRCs, resolves conflicts, simulates policy changes, and uses a decentralized ledger for accountability and transparency.
Patent 16: Automated Evolutionary Software Development with Secure, Zoned Deployment, TRC-Based Verification, and Adaptive AI-Driven Security - Creates an automated evolutionary software development system (AESDS) for ASKA. Employs secure deployment, TRC-based verification, adaptive AI-driven security, and isomorphic architecture monitoring for secure and evolving software.
Patent 17: Multi-Dimensional Audit Trail System for ASKA with AI-Driven Microstructure Analysis and Software Provenance Tracking - Develops a multi-dimensional audit trail system (MDATS) using digital logs and physical microstructures. Employs AI-driven analysis, software provenance tracking, and real-time anomaly reporting for comprehensive auditing.
Patent 18: Secure and Adaptive Hyper-Virtualization System for Collaborative Workloads with Decentralized Policy Management, Real-time Security Monitoring, and Privacy-Preserving Data Sharing - Creates a secure hyper-virtualization system (SHVS) for collaborative workloads. Employs decentralized policy management, real-time monitoring, and privacy-preserving data sharing for secure collaboration.
Patent 19: Privacy-Preserving Federated Learning System using Secure Multi-Party Computation across Isolated Execution Stacks - Enables privacy-preserving federated learning using secure multi-party computation (MPC) across isolated IES instances. Supports dynamic orchestration, adaptive privacy techniques, and scalable collaboration for secure and private machine learning.
Patent 20: Secure Data Enclave System with Privacy-Preserving Collaborative Data Analytics - Creates a secure data enclave system within IES instances. Supports privacy-preserving data sharing, collaborative data analytics, and dynamic configuration for secure data analysis.
Patent 21: Blockchain-Enabled Self-Evolving Software System with 3D-Printed Microstructure Provenance Tracking and AI-Driven Security - Develops a blockchain-enabled self-evolving software system integrated with AESDS. Employs blockchain and 3D microstructure provenance tracking for secure and verifiable software evolution.
Patent 22: Secure Inter-Zone Collaboration Framework with Privacy-Preserving Data Exchange and Distributed Ledger Synchronization - Establishes a secure inter-zone collaboration framework (SIZCF) for secure communication and data sharing between zones. Employs privacy-preserving data exchange and distributed ledger synchronization for secure and consistent collaboration.
Patent 23: Adaptive Context-Aware MFA with Biometric and Behavioral Analysis - Implements adaptive context-aware multi-factor authentication (MFA) using biometric and behavioral analysis. Supports out-of-band token verification and decentralized ledger logging for secure authentication.
Patent 24: Hardware-Enforced Secure Encrypted Enclave for Data at Rest (HESE-DAR) with Dynamic Resource Allocation and Decentralized Governance Integration - Creates a hardware-enforced secure encrypted enclave (HESE-DAR) for data at rest protection. Employs dynamic resource allocation, granular access control, and decentralized governance integration for secure data storage.
Patent 25: Dynamically Reconfigurable Capability-Based Inter-IES Communication for ASKA - Implements dynamically reconfigurable capability-based communication between IES instances. Uses real-time reconfiguration based on trust levels, workload demands, and policies for adaptive security and resource management.
Patent 26: Capability-Enhanced Packet-Carried Forwarding State for Secure Inter-Component Communication in Multi-Kernel Systems - Enhances PCFS with capabilities for secure inter-component communication. Integrates capabilities into hop fields, providing fine-grained access control and dynamic capability reconfiguration at the data plane level.
Patent 27: Sovereign Trust Network for Secure Key Management and Authentication with Multi-Level Control and Recovery System - Creates a Sovereign Trust Network (STN) with isolated data and control planes for secure key management and authentication. Employs multi-level control and a key recovery system for enhanced security and resilience.
Patent 28: System and Method for Adaptive Secure Inter-Zone Communication Across Authenticated and Sovereign Trust Networks - Develops a Dynamic Trust Gateway (DTG) for secure communication between Authenticated and Sovereign Trust Networks. Employs dynamic channel provisioning, multi-path capability aggregation, and adaptive security for secure inter-zone communication.
Patent 29: Quantum-Entangled One-Time Pad Module for Secure Computing Architectures - Develops a Quantum-Entangled One-Time Pad (QE-OTP) module for secure communication within ASKA. Leverages quantum entanglement for key distribution, dynamic key generation, and fragmented key management within a HESE-DAR. Includes an Isomorphic Legacy System Integration module for backward compatibility.
Patent 30: Spatiotemporal Digest for Raster Content Verification - Introduces a system for verifying the authenticity and integrity of raster content (audio, images, video) using a spatiotemporal digest ("spatiotemporal metadata digest"). Captures environmental data during content creation and generates a non-invertible digest, providing a link to physical reality.
Patent 31: ASKA System with Integrated Spatiotemporal Raster Content Verification - Integrates the spatiotemporal digest verification system into ASKA. Operates within a HESE-DAR under DTMS control, binding the spatiotemporal digest to the content and recording it on the decentralized ledger. Supports legacy system integration.
Patent 32: Decentralized Privacy Blurring Standard with ASKA Integration - Creates a decentralized privacy blurring system for raster content. Uses an opt-in blockchain ledger managed by ASKA's DTMS to store anonymized biometric templates. AI agents on capture devices perform blurring based on these templates and spatiotemporal context.
Patent 33: Decentralized, Hierarchical Bootstrapping and Attestation with Dynamic Trust Integration and Tamper-Evident Audit Trail - Establishes a secure boot and attestation process leveraging a hierarchical trust model, from a Hardware Root of Trust to individual IES zones. Dynamically integrates trust assessments with DTMS and uses a tamper-evident audit trail.
Patent 34a: Quantum-Entangled Auxiliary Memory System for Out-of-Band Integrity Verification - Introduces a Quantum-Entangled Auxiliary Memory (EAM) system for out-of-band integrity verification. Uses quantum entangled storage elements linked to primary storage and a Quantum Entanglement Distribution Network. Employs cryptographic digests and quantum measurement for verification.
Patent 34b: Spatiotemporal Auxiliary Memory System for Out-of-Band Integrity Verification - Presents a Spatiotemporal Auxiliary Memory System (SAMS) for out-of-band integrity verification. Captures spatiotemporal metadata during data writes and generates spatiotemporal metadata digests for verification, linking data integrity to its physical creation context.
Patent 34c: Passively Radiative, Spatiotemporal Auxiliary Memory System for Out-of-Band Integrity Verification - Develops a passively radiative version of the spatiotemporal auxiliary memory system (PR-SAMS). Uses a Passively Radiative Sensor Array for capturing environmental metadata, reducing power consumption while maintaining strong integrity verification.
graph
ASKA:::bkg
DataResources:::block
ASKAHub:::block
IESClusterx:::block
DataResources:::block
NetworkCommunication:::block
SovereignTrustNetwork:::block
SecurityMonitoring:::block
Audit:::block
MediaHandling:::bkg_strong
subgraph ASKA["ASKA Instance"]
subgraph Audit[" "]
DLT["Decentralized<br>Ledger<br>(P13, P15)"]:::audit
MDATS["MDATS<br>(P17)"]:::audit --> DLT
Microstructure@{shape: flag, label: "3D<br>Microstructure<br>Audit<br>(P14, P17)" } --> MDATS
Microstructure:::medium_level
DLT --> Hub2Hub(("Hub")):::high_level
end
subgraph DataResources["Data & Resources"]
HESE_DAR --> SecureStorage
QEAMS["QEAMS<br>(P34a)"]:::low_level -.-> HESE_DAR
SAMS["SAMS<br>(P34b)"]:::low_level -.-> HESE_DAR
PRSAMS["PR-SAMS<br>(P34c)"]:::low_level -.-> HESE_DAR
end
subgraph ASKAHub["Hub"]
Hub(("Hub")):::high_level
Hub --> AESDS["AESDS<br>(P16)<br>IAMA<br>(P16)"]:::medium_level
Hub --> DTMS(((" <br>Dynamic<br>Trust<br> (DTMS) <Br> "))):::medium_level
Hub --> ChannelMgr["Channel<br>Mgr<br>(P3)"]:::medium_level
Hub --> CapMgr["Capability<br>Mgr<br>(P25)"]:::medium_level
Hub --> PolicyEngine["Policy<br>Engine"]:::medium_level
Hub --> ResourceMgr["Resource<br>Mgr<br>(P9,<br>P10)"]:::medium_level
Hub --> DTG["DTG<br>(P28)"]:::medium_level
Hub --> SIZCF["SIZCF<br>(P22)"]:::medium_level
Hub --> UIIntegration["UI<br>Integration"]:::medium_level
Hub --> MediaHandling["Media<br>Handling<br>(P30,<br>P31,<br>P32)"]
Hub --> SecureBoot["Secure Boot (P1, P13, P33)"]:::low_level
Hub --> AnomalyDetector["Anomaly<br>Detector<br>(P7)"]:::low_level
Hub --> GovernanceAI["Governance<br>AI<br>(P15)"]:::medium_level
end
subgraph IESClusterx["IES Cluster (P1)"]
IESCluster[["IES<br>Cluster<br>(P1)"]]:::cluster_level
%% IES1["IES<br>1"]:::medium_level --> IESCluster
%% IES2["IES<br>2"]:::medium_level --> IESCluster
%% IESn["IES<br>n"]:::medium_level --> IESCluster
IESInstances[["IES Instances<br>1..n"]] --> IESCluster
ZKEEInstances["ZKEE<br>Instances<br>(P6)"] --> IESCluster
SecureUI["Secure UI Kernel (P11)"]:::ui --> IESCluster
IESCluster --> SecureChannel["Secure<br>Channels<br>(P3)"]:::network
IESCluster --> ZKEE["ZKEE<br>(P6)"]:::medium_level
IESCluster -.-> HESE_DAR(["HESE-DAR<br>(P24)"]):::data
IESCluster --> LocalMSM["Local<br>MSM<br>(P2)"]:::low_level
ResourceMgr --> IESCluster
CapMgr --> IESCluster
end
subgraph NetworkCommunication["Network & Communication"]
SecureChannel --> Firewall["Firewall (P3)"]:::network
Firewall --> ExternalSystems["External<br>Systems"]:::external
subgraph SovereignTrustNetwork["STN"]
STN["Soverign<br>Trust<br>Network<br>(P27)"] --> SecureStorage[("Secure<br>Storage")]:::data
end
PolicyEngine --> DTG
DTG --> STN
DTG --> ATN["ATN<br>(P3)"]:::medium_level
AESDS --> STN
AESDS --> DTG
ChannelMgr --> SecureChannel
ChannelMgr --> Firewall
SIZCF --> ExternalSystems
IAMA["IAMA<br>(P16)"]:::low_level --> STN
end
subgraph SecurityMonitoring[" "]
LocalMSM --> MSM["Security<br>Monitoring<br>&<br>Response<br>(MSM) (P2)"]:::low_level
MSM --> DTMS
AnomalyDetector --> DTMS
end
GovernanceAI --> DTMS
DTMS --> STN
DTMS --> DTG
DTMS --> CapMgr
DTMS --> PolicyEngine
DTMS --> ResourceMgr
PolicyEngine --> CapMgr
UIIntegration --> SecureUI
subgraph MediaHandling["Media"]
MediaRouter{"Media<br>Router"}:::medium_level
SpatiotemporalDigest{{"Spatiotemporal<br>Digest<br>(P30,<br>P31)"}}:::medium_level --> MediaRouter
PrivacyBlurring{{"Privacy<br>Blurring<br>(P32)"}}:::medium_level --> MediaRouter
%% MediaRouter --> MediaHandling
PadFeeder["Pad<br>Feeder"]:::medium_level --> QEOTP
QEOTP["QE-OTP<br>(P29)"]:::medium_level --> SecureChannel
end
end
classDef bkg fill:#fafaf7,stroke:#ccc,stroke-width:10px
classDef block fill:#fafaf7,stroke:#988990,stroke-width:2px
classDef bkg_strong fill:#def
classDef high_level fill:#fda,stroke:#333,stroke-width:4px,font-size:1.25em
classDef cluster_level fill:#b9d3fc,stroke:#333,stroke-width:4px,font-size:1.15em
classDef medium_level fill:#b9d3fc,stroke:#333,stroke-width:2px
classDef low_level fill:#aaf,stroke:#333,stroke-width:2px
classDef data fill:#afa,stroke:#333,stroke-width:2px
classDef ui fill:#ffa,stroke:#333,stroke-width:2px
classDef audit fill:#ccf,stroke:#333,stroke-width:2px
classDef network fill:#eec,stroke:#333,stroke-width:2px
classDef external fill:#d8d8d8,stroke:#333,stroke-width:2px
linkStyle default stroke:#039,stroke-width:7px
linkStyle 32,38 stroke:#07F,stroke-width:11px
linkStyle 42,43,44,45,46,47,48,49 stroke:#f0f,stroke-width:7px
linkStyle 20,21,22,23,24,25,26,27,28 stroke:#000,stroke-width:7px
linkStyle 7,8,9,10,11,12,13,14,15,16,17,18,19 stroke:#3d2,stroke-width:8px
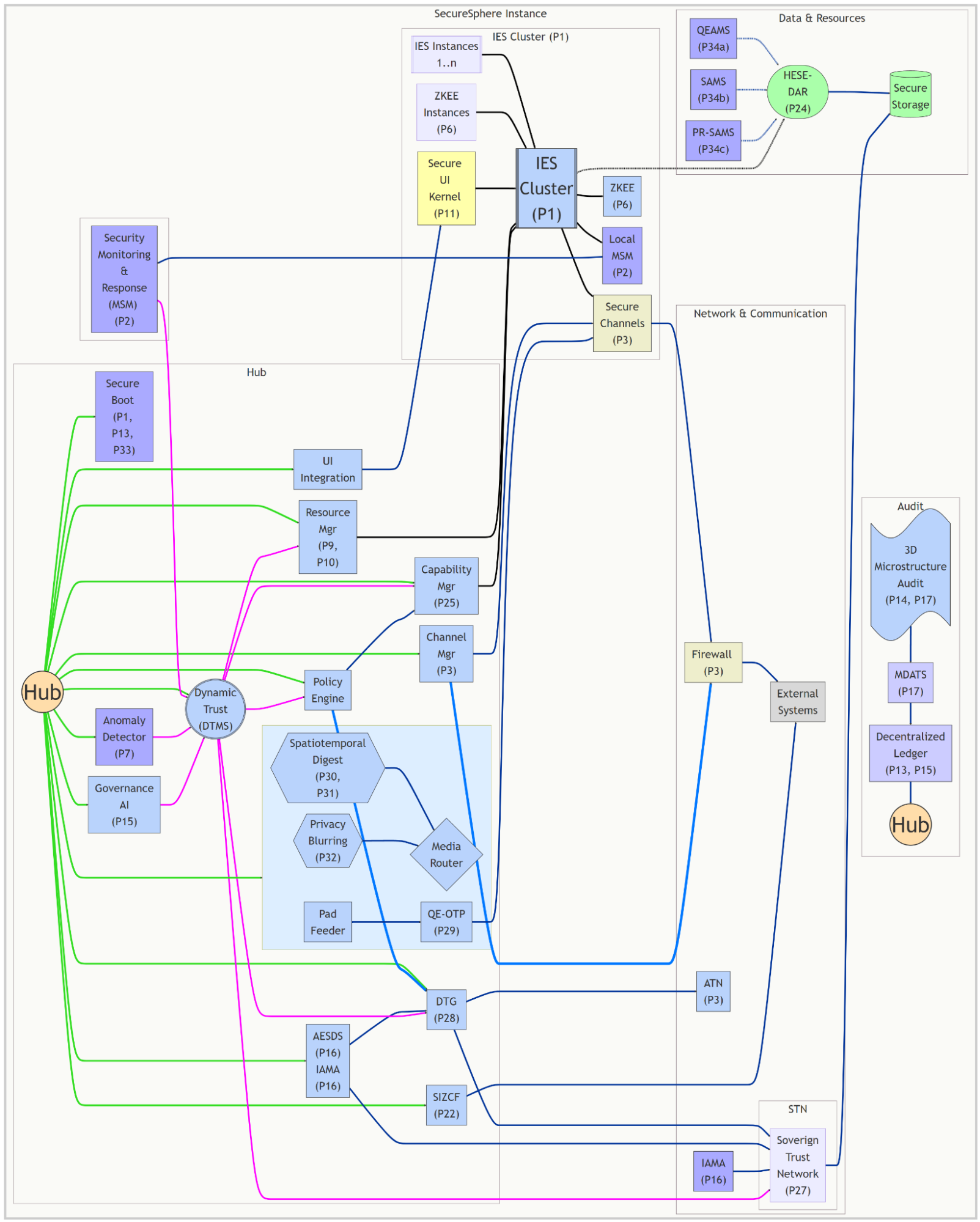
ASKA (Adaptive Secure Kernel Architecture) is a multi-layered, hardware-rooted secure computing architecture designed for high-assurance operation in complex environments, especially those involving advanced general intelligence (AGI). Its core innovation is a defense-in-depth strategy combining hardware isolation, dynamic trust management, AI-driven security, and decentralized governance.
At the heart of ASKA is the ASKA Hub, a central orchestration and management component. The Hub houses critical modules including: the AI-driven AESDS (Automated Evolutionary Software Development System – P16) and IAMA (Isomorphic Architecture Monitoring and Adaptation – P16) for continuous software evolution and proactive patching of legacy systems; the DTMS (Dynamic Trust Management System – P4) for dynamic trust assessment and access control based on observed behavior, security posture, and declared attributes; the Channel Manager (P3) for managing the Multi-Channel Network; the Capability Manager (P25) for dynamic, fine-grained access control; the Policy Engine for enforcing security policies; the Resource Manager (P9, P10) for AI-powered resource allocation and predictive scaling; the DTG (Dynamic Trust Gateway – P28) mediating communication between the ATN (Authenticated Trust Network – P3) and the highly isolated STN (Sovereign Trust Network – P27); the SIZCF (Secure Inter-Zone Collaboration Framework – P22) for secure inter-zone communication; the UI Integration module; a Media Handling subsystem (P30, P31, P32) for spatiotemporal digest verification, privacy blurring, and secure media routing; the Secure Boot process (P1, P13, P33); the Anomaly Detector (P7); and the Governance AI (P15) for auditing and conflict resolution. All significant events are logged to the Decentralized Ledger (DLT – P13, P15) and correlated with a 3D Microstructure Audit Trail (P14, P17) via MDATS (Multi-Dimensional Audit Trail System – P17), ensuring tamper-evident, multi-dimensional auditing.
The IES Cluster (Isolated Execution Stacks – P1) forms the foundation for ASKA’s strong isolation. Multiple independent IES instances, each with dedicated hardware resources (CPU, memory, I/O, network), run applications and processes in complete isolation. IES instances can be dynamically partitioned into smaller child-IES instances (P1) for granular control and adaptive scaling (P10). Secure communication within and between IES instances is facilitated by Secure Channels (P3), with capability-aware forwarding (P26) ensuring fine-grained access control. IES instances utilize ZKEE (Zero-Knowledge Execution Environment – P6) for private computation and the HESE-DAR (Hardware-Enforced Secure Encrypted Enclave for Data at Rest – P24) for secure data storage. Local security monitoring is handled by Local MSMs (Local Security Meshes – P2), reporting to the MSM (Master Security Mesh – P2) for overall system-wide monitoring and analysis. The Secure UI Kernel (P11) provides a trusted user interface, isolated from the underlying system.
ASKA's network infrastructure includes the ATN for internal authenticated communication, the STN for highly sensitive data, and the DTG mediating between them. The Firewall (P3) protects against unauthorized external access. External communication and inter-zone collaboration are facilitated by the SIZCF (P22), leveraging the Multi-Channel Network (P3) and potentially quantum-resistant communication (P5). The IAMA module (P16) proactively identifies and mitigates vulnerabilities in connected legacy systems.
The Resource Manager (P9, P10) dynamically allocates resources based on trust levels (DTMS), security policies (Policy Engine), and workload demands, using multipath optimization for efficiency and resilience. Secure data storage is provided by HESE-DAR (P24), employing post-quantum cryptography (P5). Out-of-band data integrity verification is provided by diverse auxiliary memory systems: QEAMS (Quantum-Entangled Auxiliary Memory System – P34a), SAMS (Spatiotemporal Auxiliary Memory System – P34b), and PR-SAMS (Passively Radiative Spatiotemporal Auxiliary Memory System – P34c). The Media Handling subsystem (P30, P31, P32) uses a Media Router, Spatiotemporal Digest generation and verification, and Decentralized Privacy Blurring to manage media data securely and privately. The entire system is underpinned by decentralized governance (P13, P15), with all actions logged on the DLT and the MDATS (P17) for transparency and accountability, further enhanced by the 3D Microstructure Audit Trail (P14, P17). The QE-OTP (Quantum-Entangled One-Time Pad – P29) provides an additional layer of security for sensitive communications.
1. ASKA Hub: The Hub isn't merely a central point; it's the system's brain, orchestrating complex interactions for robust, adaptive security.
2. IES Cluster (P1): The IES Cluster is the foundation of ASKA's isolation, where applications and processes run in their own secure worlds.
3. Network & Communication: This subsystem ensures data moves securely and efficiently within and beyond ASKA.
4. Security Monitoring & Response (MSM - P2): This subsystem is ASKA's immune system, constantly vigilant and responsive to threats.
5. Data & Resources: This area focuses on securely managing data and allocating resources efficiently.
6. UI & External Systems: This subsystem manages the delicate balance between user interaction, external collaboration, and system security.
7. Media Handling: This subsystem provides specialized and secure processing for media data.
4. Security Monitoring & Response (MSM - P2): This continuously monitors system activity and triggers automated responses to security threats.
5. Data & Resources: This layer manages data securely and allocates resources dynamically.
6. UI & External Systems: This subsystem handles secure user interaction and controlled external communication.
7. Media Handling: This subsystem provides specialized, secure mechanisms for handling media data.
graph
subgraph UserInterface["User Interface"]
User["User<br>(P11, P23)"] --> SecureUI["Secure UI Kernel<br>(P11)"]
SecureUI --> UI_Monitor["UI Monitor (P37)"]
UI_Monitor --> InputSanitizer["Input Sanitizer (P11, P37)"]
MFA["MFA (P23)"] --> SecureUI
end
subgraph ASKACore["ASKA Core"]
InputSanitizer -- Authenticated & Sanitized Input --> IESCluster["IES Cluster (P1)"]
IESCluster --> AppLayer["Application<br>Layer"]
AppLayer --> IES1["IES<br>1"]
AppLayer --> IES2["IES<br>2"]
AppLayer --> IESn["IES<br>n"]
IES1 --> App1["App<br>1"]
IES2 --> App2["App<br>2"]
IESn --> Appn["App<br>n"]
IESCluster --> DTMS["DTMS (P4)"]
DTMS --> PolicyEngine["Policy Engine (P4)"]
DTMS --> CapMgr["Capability Mgr (P25)"]
DTMS --> ResourceMgr["Resource Mgr (P9, P10)"]
App1 -.-> CapMgr
App2 -.-> CapMgr
Appn -.-> CapMgr
App1 --> ResourceMgr
App2 --> ResourceMgr
Appn --> ResourceMgr
subgraph MediaHandling["Media Handling"]
ResourceMgr --> MediaRouter["Media Router"]
MediaRouter --> SpatiotemporalDigest["Spatiotemporal Digest (P30, P31)"]
MediaRouter --> PrivacyBlurring["Privacy Blurring (P32)"]
end
subgraph SecureCommunications["Secure Communications"]
IESCluster
end
subgraph SecurityMonitoringResponse["App Instances"]
IES1
IES2
IESn
end
subgraph AuditingGovernance["Auditing & Governance"]
UI_Monitor --> DLT["Decentralized Ledger<br>(P13, P15, P17, P37)"]
end
end
classDef high_level fill:#f9f,stroke:#333,stroke-width:4px
classDef medium_level fill:#ccf,stroke:#333,stroke-width:2px
classDef low_level fill:#aaf,stroke:#333,stroke-width:2px
classDef data fill:#afa,stroke:#333,stroke-width:2px
classDef ui fill:#ffa,stroke:#333,stroke-width:2px
classDef audit fill:#ccf,stroke:#333,stroke-width:2px
classDef network fill:#eec,stroke:#333,stroke-width:2px
classDef external fill:#d8d8d8,stroke:#333,stroke-width:2px
linkStyle default stroke:#ccc,stroke-width:2px
This diagram depicts the ASKA architecture, illustrating the interplay between user interaction, application execution, core system services, data management, network communication, and security monitoring/auditing.
I. User Interaction Layer:
User interaction is strictly confined to the Secure UI Kernel, ensuring a secure and controlled interface. This component, detailed in Patent 11, leverages hardware and zonal isolation, CFI (Control-Flow Integrity) to prevent code injection, and declarative policies for managing user access and privileges. Communication with the underlying system is unidirectional, preventing unauthorized feedback channels and enhancing protection against reverse engineering attacks.
II. Application Layer:
Applications run within isolated execution environments, specifically IES (Isolated Execution Stacks) instances (Patent 1). Each IES offers full-stack hardware isolation (CPU, memory, I/O, network), minimizing the blast radius of potential security compromises and preventing lateral movement. ASKA allows for dynamic partitioning of IES instances into smaller, isolated child-IES instances to optimize resource usage and further enhance security. The Secure UI Kernel interacts with these IES instances concurrently, managing and controlling access based on user permissions and trust levels.
III. ASKA Core:
The core system manages trust and resource allocation, centered around the DTMS (Dynamic Trust Management System) (Patent 4). The DTMS uses TRCs (Trust Root Configurations) (Patent 1) stored on the decentralized ledger to manage trust relationships, dynamically adjusting trust levels based on real-time data from security monitoring (Local MSMs, Anomaly Detector), performance metrics, and system health. This dynamic adaptation influences access control, resource allocation (via the Resource Manager), and software updates (via AESDS).
The DTMS directly interacts with:
IV. Data & Resource Management:
Applications interact with the Resource Manager for resource allocation. The HESE-DAR (Hardware-Enforced Secure Encrypted Enclave for Data at Rest) (Patent 24) is used for encrypting data at rest, employing hardware-level encryption and anti-tamper mechanisms for securing sensitive data.
V. Media Handling:
This section showcases the newly integrated media processing capabilities.
VI. Network & Communication:
IES instances communicate via Secure Channels (Patent 3) which are managed by the Channel Manager. These channels provide secure communication pathways, potentially using quantum-resistant communication (Patent 5), and enforce fine-grained access control using capability-aware forwarding (Patent 2, 26). The DTG (Dynamic Trust Gateway) (Patent 28) mediates communication between the ATN (Authenticated Trust Network) and STN (Sovereign Trust Network), dynamically provisioning secure channels based on real-time conditions and trust levels.
VII. External Systems:
ASKA interacts with external systems through the ATN (for authenticated communication) and the STN (for highly sensitive data). The SIZCF (Secure Inter-Zone Collaboration Framework) (Patent 22) facilitates secure collaboration and data exchange between different ASKA zones.
VIII. Monitoring & Auditing:
ASKA employs a hierarchical security monitoring system:
graph
subgraph "Authenticated Trust Network (ATN)"
ATN([ATN])
end
subgraph "Dynamic Trust Gateway (DTG)"
DTG([DTG])
DTG --> Channel_Provisioner[Channel<br>Provisioner];
DTG --> Capability_Aggregator[Capability<br>Aggregator];
DTG --> Security_Monitor[Security<br>Monitor];
DTG --> Audit_Logger[Audit<br>Logger];
style DTG fill:#ccf,stroke:#333,stroke-width:1px
end
subgraph "Sovereign Trust Network (STN)"
STN([STN])
STN --> Secure_Channel1((Secure<br>Channel<br>1));
STN --> Secure_Channel2((Secure<br>Channel<br>2));
STN --> Secure_ChannelN((Secure<br>Channel<br>N));
style STN fill:#ccf,stroke:#333,stroke-width:1px
end
ATN --> DTG;
DTG --> STN;
Channel_Provisioner --> Secure_Channel1;
Channel_Provisioner --> Secure_Channel2;
Channel_Provisioner --> Secure_ChannelN;
Secure_Channel1 --> Capability_Aggregator;
Secure_Channel2 --> Capability_Aggregator;
Secure_ChannelN --> Capability_Aggregator;
Capability_Aggregator --> STN;
Security_Monitor --> Audit_Logger;
Security_Monitor --> Channel_Provisioner;
Audit_Logger --> DLT((Decentralized<br>Ledger));
style Audit_Logger fill:#aaf,stroke:#333,stroke-width:1px
style DLT fill:#aaf,stroke:#333,stroke-width:1px
classDef high_level fill:#f9f,stroke:#333,stroke-width:2px
classDef medium_level fill:#ccf,stroke:#333,stroke-width:1px
classDef low_level fill:#aaf,stroke:#333,stroke-width:1px
This diagram details the architecture of the Dynamic Trust Gateway (DTG) (P28), a critical component of ASKA responsible for mediating communication between the Authenticated Trust Network (ATN) (P3) and the Sovereign Trust Network (STN) (P27). The DTG's design emphasizes dynamic adaptability, multi-layered security, and decentralized governance to ensure secure and controlled data flow between these distinct trust domains. The design incorporates several novel features to improve resilience and transparency over traditional gateway architectures.
I. Authenticated Trust Network (ATN):
The ATN represents the ASKA's internal network with authenticated communication (P3). It provides secure pathways for communication between authorized entities within the ASKA environment, but with a lower security posture than the STN. Each communication path within the ATN leverages a dedicated firewall instance, preventing cross-channel interference.
II. Dynamic Trust Gateway (DTG):
The DTG sits at the interface between the ATN and STN, providing dynamic and secure communication mediation. The DTG's architecture consists of the following key modules:
III. Sovereign Trust Network (STN):
The STN (P27) represents the high-security network, designed for sensitive data and cryptographic keys. It uses dedicated secure channels to maintain its isolation and prevent data leakage. This is enhanced by its isolated data plane and minimal control plane coupling, preventing common attack vectors.
Relationships and Interactions:
The diagram illustrates the data flow and control mechanisms within the DTG:
This architecture provides a highly secure and adaptable gateway solution for managing communication between networks with varying security requirements. The use of dynamic channel provisioning, multi-path aggregation, deep packet inspection, and comprehensive auditing creates a resilient system capable of responding to changing threat landscapes and maintaining data integrity and confidentiality. Decentralized governance ensures transparency and accountability.
graph LR
subgraph ASKA
subgraph IES["IES (P1)"]
direction LR
IESCore[Core] --> ChildIES1[Child IES]
IESCore --> ChildIES2[Child IES]
ChildIES1 <--> ChildIES2(("CE-PCFS (P26)"))
ChildIES1 -.-> HESE-DAR["HESE-DAR (P24)"]
ChildIES2 -.-> HESE-DAR
ChildIES1 <--> ZKEE["ZKEE (P6)"]
ChildIES2 <--> ZKEE
ResMgr["Resource Mgr (P9, P10)"] <--> ChildIES1
ResMgr <--> ChildIES2
SecMon["Security Monitor (P7)"] --> ChildIES1
SecMon --> ChildIES2
style IES fill:#f9f,stroke:#333,stroke-width:2px
end
Hub[ASKA Hub] --> IES
Hub --> DTMS["DTMS (P4)"]
Hub --> AESDS["AESDS (P16)"]
Hub --> DTG["DTG (P28)"]
Hub -.-> SIZCF["SIZCF (P22)"]
Hub -.-> SHVS["SHVS (P18)"]
DTMS -.-> IES
DTMS -.-> DTG
DTMS -.-> STN["STN (P27)"]
DTMS <--> DZMS["DZMS (P4)"]
AESDS --> DTG
AESDS --> IES
AESDS --> STN
IAMA["IAMA (P16)"] --> STN
DTG <--> STN
DTG <--> ATN["ATN (P3)"]
style Hub fill:#ccf,stroke:#333,stroke-width:2px
end
subgraph External Systems/Legacy
Legacy[Legacy System] --> IAMA
Ext1[External System/Zone] <--> SIZCF
Ext2[External High-Trust] <--> STN
end
subgraph Supporting Technologies
DLT["Decentralized Ledger (P13, P15)"] -.-> Hub
DLT -.-> DTMS
DLT -.-> AESDS
DLT -.-> SIZCF
MDATS["MDATS (P17)"] -.-> Hub
MDATS -.-> IES
MDATS -.-> DTG
MSM["MSM (P2)"] -.-> IES
MSM -.-> DTG
MSM -.-> STN
MultiChannel["Multi-Channel Network (P3)"] -.-> ATN
MultiChannel -.-> DTG
Quantum["Quantum-Resistant Comm (P5)"] -.-> DTG
Quantum -.-> STN
SecureUI["Secure UI Kernel (P11)"] -.-> IES
Chiplets["Chiplet Arch (P12)"] -.-> IES
Chiplets -.-> HESE-DAR
FedLearn["Federated Learning (P19)"] -.-> IES
SDE["Secure Data Enclaves (P20)"] -.-> IES
MFA["Adaptive MFA (P23)"] -.-> Hub
MFA -.-> STN
CapMgr["Capability Mgr (P25)"] -.-> IES
CapMgr -.-> DTG
style DLT fill:#ffc,stroke:#333,stroke-width:2px
end
linkStyle 0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20 stroke:#000,stroke-width:1.5px;
linkStyle 21,22,23 stroke:#f00,stroke-width:1.5px;
This patent describes ASKA, a novel system architecture for establishing and maintaining secure communication and collaboration amongst multiple isolated execution environments (IEEs) while integrating with legacy systems and external entities. ASKA employs a multi-layered, dynamically adaptable approach based on hardware-enforced isolation, decentralized trust management, and AI-driven security. This architecture incorporates several innovative features, including a modular Isolated Execution Stack (IES), a Dynamic Trust Management System (DTMS), an Automated Evolutionary Software Development System (AESDS), and a Sovereign Trust Network (STN), all interacting through a central ASKA Hub.
1. System Architecture Overview:
2. Key Innovative Features:
graph LR
subgraph "ASKA Security Monitoring"
A[ASKA<br>Hub] --> B(Master<br>Security<br>Mesh);
B --> C(Security<br>Policy<br>Engine);
C --> D(DTMS);
D --> E(Access<br>Control);
B --> F(Anomaly<br>Detection<br>Engine);
F --> G(Alerting<br>System);
G --> A;
F --> H(Response<br>System);
H --> I(Isolator);
H --> J(Self-Healer);
H --> K(Resource<br>Manager);
I --> SecureOS;
J --> SecureOS;
K --> SecureOS;
style B fill:#ccf,stroke:#333,stroke-width:2px
style F fill:#ccf,stroke:#333,stroke-width:2px
style G fill:#ccf,stroke:#333,stroke-width:2px
style H fill:#ccf,stroke:#333,stroke-width:2px
style I fill:#ccf,stroke:#333,stroke-width:2px
style J fill:#ccf,stroke:#333,stroke-width:2px
style K fill:#ccf,stroke:#333,stroke-width:2px
subgraph "Local Security Meshes (Patent 2)"
L[Local<br>MSM 1] --> B;
M[Local<br>MSM 2] --> B;
N[...<br>Local<br>MSM n] --> B;
style L fill:#bbf,stroke:#333,stroke-width:2px
style M fill:#bbf,stroke:#333,stroke-width:2px
style N fill:#bbf,stroke:#333,stroke-width:2px
end
subgraph "Data Sources"
O[IES<br>Instances] --> L;
P[Network<br>Channels] --> B;
Q[HESE#8209;DAR] --> B;
R[Secure<br>UI<br>Kernel] --> B;
style O fill:#aaf,stroke:#333,stroke-width:2px
style P fill:#aaf,stroke:#333,stroke-width:2px
style Q fill:#aaf,stroke:#333,stroke-width:2px
style R fill:#aaf,stroke:#333,stroke-width:2px
end
subgraph "Audit Trail (Patent 17)"
G --> S[MDATS];
H --> S;
S --> DLT;
style S fill:#ddf,stroke:#333,stroke-width:2px
end
subgraph "Decentralized Ledger (Patent 15)"
DLT[Decentralized<br>Ledger];
end
end
linkStyle default stroke:#555,stroke-width:1px
classDef secure fill:#ccf,stroke:#333,stroke-width:2px
classDef mesh fill:#bbf,stroke:#333,stroke-width:2px
classDef data fill:#aaf,stroke:#333,stroke-width:2px
classDef audit fill:#ddf,stroke:#333,stroke-width:2px
Legend:
Description:
This diagram illustrates the multi-layered security monitoring and response system within ASKA, highlighting its dynamic, adaptive, and decentralized nature. The system is designed to detect and respond to a wide range of threats, from internal anomalies to external attacks, leveraging advanced techniques for real-time threat assessment and automated remediation.
I. Distributed Security Monitoring:
The system employs a hierarchical monitoring architecture:
II. Threat Assessment and Policy Enforcement:
The MSM provides data to the Security Policy Engine (C), which defines security policies based on risk profiles and real-time context. These policies incorporate trust levels from the Dynamic Trust Management System (DTMS - P4) and are dynamically updated based on threat intelligence, system status, and user interaction patterns. The Security Policy Engine directly impacts the DTMS (D), influencing trust assessments which in turn govern access control. The DTMS provides real-time trust assessments for access control decisions.
III. Anomaly Detection and Response:
IV. Auditing and Logging:
The MDATS (S) plays a critical role in maintaining a detailed, tamper-evident audit trail of all security events. MDATS collects data from the Alerting System, Response System, and other security modules. This multi-dimensional audit trail (P17) combines digital logs with physical 3D microstructures (P14), ensuring verifiability and providing comprehensive provenance tracking. All audit trail information is logged on the Decentralized Ledger (DLT - P13, P15) for permanent storage and auditable access.
Data Sources:
The system gathers data from diverse sources, including IES instances (O), Network Channels (P), HESE-DAR (Q), and the Secure UI Kernel (R), providing a holistic view of system security.
This design offers a robust, responsive, and adaptive security system, effectively mitigating a wide spectrum of threats. The hierarchical monitoring structure, decentralized governance, automated response system, and comprehensive auditing contribute to the overall security and reliability of the ASKA architecture. The system's capacity for dynamic adaptation is crucial for responding to the ever-evolving threat landscape.
graph
subgraph "ASKA Key Management & Recovery"
A[ASKA Hub] --> B(Key Management System);
B --> C(Key Generation);
C --> D(Secure Key Storage);
D --> E[IES Instances];
B --> F(Key Usage Monitoring);
F --> B;
B --> G(Key Revocation);
G --> D;
style B fill:#ccf,stroke:#333,stroke-width:2px
style D fill:#ccf,stroke:#333,stroke-width:2px
style G fill:#ccf,stroke:#333,stroke-width:2px
class B,D,G key
subgraph "Sovereign Trust Network (STN) (Patent 27)"
H[STN Key Manager] --> D;
I[STN Authentication Manager] --> H;
H --> J(Key Recovery Controller);
J --> K(Synchronization Nodes);
K --> L[External High-Trust Environments];
style H fill:#bbf,stroke:#333,stroke-width:2px
style J fill:#bbf,stroke:#333,stroke-width:2px
style K fill:#bbf,stroke:#333,stroke-width:2px
class H,J,K stn
end
subgraph "Dynamic Trust Gateway (DTG) (Patent 28)"
M[DTG Capability Manager] --> B;
M --> N(Dynamic Channel Provisioning);
N --> O[ATN/STN Communication];
style M fill:#aaf,stroke:#333,stroke-width:2px
style N fill:#aaf,stroke:#333,stroke-width:2px
class M,N dtg
end
subgraph "Hardware Enclaves"
P["HESE-DAR (Patent 24)"] --> D;
style P fill:#ddf,stroke:#333,stroke-width:2px
end
subgraph "Audit Trail (Patent 17)"
F --> Q[MDATS];
G --> Q;
Q --> R[Decentralized Ledger];
style Q fill:#ccf,stroke:#333,stroke-width:2px
class Q audit
end
end
linkStyle default stroke:#555,stroke-width:1px
classDef key fill:#ccf,stroke:#333,stroke-width:2px
classDef stn fill:#bbf,stroke:#333,stroke-width:2px
classDef dtg fill:#aaf,stroke:#333,stroke-width:2px
classDef enclave fill:#ddf,stroke:#333,stroke-width:2px
classDef audit fill:#ccf,stroke:#333,stroke-width:2px
Legend:
Description:
This diagram details the architecture of ASKA's key management and recovery system, emphasizing its design for high security, resilience, and robust auditability. The system incorporates several novel features to address the challenges of managing cryptographic keys in a complex, distributed, and potentially hostile environment.
I. Centralized Key Management:
The ASKA Hub (A) orchestrates key management via the Key Management System (B). This system is responsible for:
II. Sovereign Trust Network (STN) Key Management (Patent 27):
The STN (P27) maintains a dedicated key management subsystem, further enhancing security and resilience:
III. Dynamic Trust Gateway (DTG) Key Integration (Patent 28):
The DTG (P28) leverages ASKA's key management system for secure communication between ATN and STN:
IV. Hardware Enclaves and Secure Storage:
The HESE-DAR (P24) plays a critical role in providing high-assurance secure storage for keys, integrating with the Key Management System for secure key retrieval and storage.
V. Auditing and Logging:
The Multi-Dimensional Audit Trail System (MDATS - P17) meticulously logs all key management and recovery events. This includes key generation, usage, revocation, and recovery attempts. This detailed audit trail is stored on the Decentralized Ledger (R - P13, P15), ensuring transparency and tamper-evidence. The MDATS uses techniques (P14) to integrate physical tamper-evident audit trails (3D microstructures) alongside the digital audit trails for increased assurance.
This architecture provides a robust and secure solution for managing cryptographic keys in a highly secure environment. The multi-layered approach, use of hardware security mechanisms (P24), and integration with ASKA's core security components contribute to high assurance and resilience. Decentralized governance and the comprehensive audit trail ensure transparency and accountability in all key operations. The key recovery system ensures high data availability in the face of various threats.
graph LR
subgraph "ASKA Zone Management & Inter#8209;Zone Communication"
A[ASKA Global Control Plane] --> B(Zone Creation & Management);
B --> C(Zone Hierarchy);
C --> D{Zones};
B --> E(TRC Management);
E --> C;
E --> F[Decentralized Ledger];
style B fill:#ccf,stroke:#333,stroke-width:2px
style E fill:#ccf,stroke:#333,stroke-width:2px
class B,E management
subgraph Zones
D --> G[ASKA Hub];
G --> H(IES Clusters);
G --> I(Local Security Mesh);
H --> J[Secure Communication Agent];
J --> K[Multi-Channel Network];
K --> L[Other Zones];
style G fill:#bbf,stroke:#333,stroke-width:2px
style H fill:#bbf,stroke:#333,stroke-width:2px
style J fill:#bbf,stroke:#333,stroke-width:2px
style K fill:#bbf,stroke:#333,stroke-width:2px
class G,H,J,K zone
end
subgraph "Inter#8209;Zone Communication (Patent 22)"
L --> M[SIZCF];
M --> N[External Systems];
style M fill:#aaf,stroke:#333,stroke-width:2px
class M interzone
end
subgraph "Auditing & Governance (Patent 17)"
E --> O[MDATS];
O --> F;
style O fill:#ddf,stroke:#333,stroke-width:2px
class O audit
end
end
linkStyle default stroke:#555,stroke-width:1px
classDef management fill:#ccf,stroke:#333,stroke-width:2px
classDef zone fill:#bbf,stroke:#333,stroke-width:2px
classDef interzone fill:#aaf,stroke:#333,stroke-width:2px
classDef audit fill:#ddf,stroke:#333,stroke-width:2px
This diagram illustrates ASKA's zone management and inter-zone communication. While the SIZCF diagram shows inter-zone collaboration, this more comprehensive diagram shows the overall zone architecture, including zone creation, management, trust relationships between zones, and the various communication pathways, including the role of the ASKA Hubs and the Decentralized Ledger.
Legend:
Description:
This diagram illustrates ASKA's zone management and inter-zone communication framework (P22), a crucial aspect of its architecture that enables secure and controlled collaboration between multiple, independent security domains. This system combines a hierarchical zone structure with dynamic trust management and secure communication protocols to facilitate cooperation while maintaining strong isolation between zones.
I. ASKA Global Control Plane:
The ASKA Global Control Plane (A) acts as the central authority for managing the overall zone structure and configuration. This is not a single point of failure, instead its functions are implemented using replicated, distributed components secured with cryptographic mechanisms. It interacts with the system's zone creation and management processes.
II. Zone Creation and Management (B):
The Zone Creation & Management (B) module is responsible for creating and managing ASKA zones. This module uses a dynamic policy language to define parameters such as security policies, resource allocation, and allowed inter-zone communication. These policies incorporate trust levels (P4) and are persistent in the decentralized ledger (P13, P15). The module interacts with the TRC Management module for trust definition and propagation.
III. Zone Hierarchy (C):
ASKA zones are organized into a flexible hierarchy (C) reflecting the organization's structure and security needs. This allows for granular control over trust relationships and inter-zone communication. Trust and policy inheritance occur from parent to child zones, simplifying management and consistency.
IV. Zones (D):
Each zone (D) functions as an independent ASKA deployment, containing its own:
V. Inter-Zone Communication (Patent 22):
Secure inter-zone communication is facilitated by the Secure Inter-Zone Collaboration Framework (SIZCF) (M). The SIZCF utilizes secure communication channels (P3, P5) and privacy-preserving protocols (P20, P22) for secure data exchange. Communication between zones is dynamically managed, guided by trust levels (P4), policies (P13, P15), and real-time threat assessments (P2). The SIZCF provides access to external systems while maintaining a robust security boundary.
VI. Auditing and Governance (Patent 17):
All zone management and inter-zone communication activities are logged on the Decentralized Ledger (F) (P13, P15) using the Multi-Dimensional Audit Trail System (MDATS - O) (P17). MDATS tracks all critical events, including zone creation/modification, TRC updates, trust relationships, and inter-zone data exchange. This data can be analyzed by the Governance AI component for identification of anomalies and proactive security enhancements.
This architecture enables secure and flexible collaboration across multiple ASKA zones, preserving the integrity and confidentiality of data while allowing for a managed expansion of the system. The decentralized governance model enhances transparency, accountability, and resilience against attacks. Dynamic adaptation based on trust and security assessments ensure continuous optimization of the system's security posture. The integration with the MDATS and decentralized ledger ensures a comprehensive and tamper-evident audit trail of all zone management and inter-zone communication activities.
graph LR
subgraph ASKA Zone Internal Data Flow & Security
A[ASKA Hub] --> B(IES<br>Clusters);
B --> C(Applications);
C --> D[Secure Data Enclaves];
D --> E[Federated<br>Learning];
B --> F(Local<br>Security<br>Meshes);
F --> G(Master<br>Security<br>Mesh);
G --> H(Anomaly<br>Detection);
H --> I(Response<br>System);
I --> B;
G --> A;
style A fill:#ccf,stroke:#333,stroke-width:2px
style G fill:#ccf,stroke:#333,stroke-width:2px
class A,G hub
subgraph "Data Services"
D --> J(Data<br>Input/Output);
J --> K[Multi#8209;Channel<br>Network];
K --> L[Other<br>Zones<br>/<br>External<br>Systems];
style D fill:#bbf,stroke:#333,stroke-width:2px
style E fill:#bbf,stroke:#333,stroke-width:2px
style J fill:#bbf,stroke:#333,stroke-width:2px
style K fill:#bbf,stroke:#333,stroke-width:2px
class D,E,J,K data
end
subgraph "ASKA Hub"
A --> M(DTMS);
M --> B;
A --> N(AESDS);
N --> B;
A --> O(Policy<br>Engine);
O --> G;
style M fill:#aaf,stroke:#333,stroke-width:2px
style N fill:#aaf,stroke:#333,stroke-width:2px
style O fill:#aaf,stroke:#333,stroke-width:2px
class M,N,O hubservices
end
subgraph "Decentralized Ledger"
P[Decentralized<br>Ledger] -.-> A;
P -.-> D;
P -.-> E;
P -.-> G;
style P fill:#ddf,stroke:#333,stroke-width:2px
class P ledger
end
end
linkStyle default stroke:#555,stroke-width:1px
classDef hub fill:#ccf,stroke:#333,stroke-width:2px
classDef data fill:#bbf,stroke:#333,stroke-width:2px
classDef hubservices fill:#aaf,stroke:#333,stroke-width:2px
classDef ledger fill:#ddf,stroke:#333,stroke-width:2px
Legend:
Description:
This diagram provides an in-depth view of the internal data flow and security processes within a single ASKA zone. It illustrates how data is securely processed, transferred, and monitored within the zone, emphasizing the interactions between the Hub, IES clusters, security modules, data services, and the Decentralized Ledger. The layered and integrated security architecture demonstrates ASKA's ability to maintain robust data protection and system integrity.
I. ASKA Hub (A):
The ASKA Hub acts as the central orchestrator and management point within the zone. It coordinates activities of the IES clusters, manages security policies, and oversees communication with other zones and external systems. The Hub incorporates essential security modules and services:
II. Isolated Execution Stacks (IES) Clusters (B):
IES Clusters provide secure and isolated execution environments for applications. Each IES (P1) has dedicated hardware resources (CPU, memory, I/O, network), minimizing the impact of compromises.
III. Secure Data Services:
ASKA zones host various data services within IES instances, including:
IV. Data Flow and Communication:
Data within the ASKA zone is transferred through secure channels managed by the Multi-Channel Network (K). The MCN (P3) utilizes physically segregated channels with dedicated firewalls, preventing cross-channel interference and ensuring the isolation of data flows. The MCN leverages capability-aware forwarding (P2, P26) for fine-grained access control and dynamic traffic management. Quantum-resistant communication (P5) using techniques like QKD, DKM, and PQC further secure these channels against sophisticated attacks.
Data Services interact with the MCN for secure data transfer both within the zone and with other zones or external systems (L), ensuring that sensitive information is protected during transit.
V. Security Monitoring and Response:
VI. Decentralized Ledger (P):
The Decentralized Ledger (P13, P15) serves as a tamper-proof repository for audit trails, security policies, zone configuration, and other critical data. Its distributed nature ensures high availability, integrity, and transparency. The Decentralized Ledger integrates with the MDATS (P17) to record events and activities from all ASKA components within the zone, including the Hub, IES clusters, data services, and the security monitoring system.
Interactions and Integration:
This diagram illustrates the flow of data and control information within the ASKA zone:
This layered and integrated approach creates a robust and dynamic security architecture within the ASKA zone. The combination of hardware-enforced isolation (P1, P24), advanced threat detection (P7), automated response mechanisms (P7), and secure communication (P2, P3, P5, P26) ensures a high level of data protection, system integrity, and resilience against sophisticated threats. Decentralized governance and the comprehensive audit trail provide transparency, accountability, and trust in the system's operation.
graph TD
subgraph "ASKA Bootstrapping & Attestation"
A[Power On] --> B(Hardware Root of Trust);
B --> C{Secure Boot ROM};
C --> D(Bootloader Verification);
D -- Verified --> E(Secure OS Loading);
D -- Tampered --> F[Halt/Alert];
E --> G(IES Initialization);
G --> H(Mini-TRC Verification);
H -- Verified --> I(DTMS Integration);
H -- Tampered --> F;
I --> J(Application Loading);
J --> K(Attestation Service);
K --> L(Attestation Report);
L --> M[Decentralized Ledger];
style C fill:#ccf,stroke:#333,stroke-width:2px
style G fill:#ccf,stroke:#333,stroke-width:2px
style K fill:#ccf,stroke:#333,stroke-width:2px
class C,G,K secure
subgraph "Trust Root Configuration (TRC)"
N[TRC] --> C;
N --> H;
style N fill:#bbf,stroke:#333,stroke-width:2px
class N trc
end
subgraph "Dynamic Trust Management System (DTMS)"
D --> O[DTMS];
O --> I;
style O fill:#aaf,stroke:#333,stroke-width:2px
class O dtms
end
end
linkStyle default stroke:#555,stroke-width:1px
classDef secure fill:#ccf,stroke:#333,stroke-width:2px
classDef trc fill:#bbf,stroke:#333,stroke-width:2px
classDef dtms fill:#aaf,stroke:#333,stroke-width:2px
The diagram represents a high-level visualization of the ASKA bootstrapping and attestation process. This dedicated diagram illustrates secure boot’s steps, from initial power-on to establishing a trusted execution environment within an IES, and the integration with the DTMS, TRCs, and the Decentralized Ledger.
Legend:
Description:
This diagram provides a comprehensive illustration of the ASKA bootstrapping and attestation process, showcasing the system's multi-layered approach to building a chain of trust from the initial power-on to the execution of applications. This process ensures the integrity and authenticity of all components, establishing a secure foundation for all subsequent operations within the ASKA environment.
I. Secure Boot Sequence:
II. IES Initialization and Integration:
III. Application Loading and Attestation:
IV. Trust Root Configuration (TRC):
The TRC (N) plays a crucial role throughout the process. It contains the root keys and security policies used for verifying the Secure Boot ROM, bootloader, and mini-TRCs. The TRC itself is stored securely, potentially using HESE-DAR (P24) or a similar tamper-evident mechanism.
V. Dynamic Trust Management System (DTMS):
The DTMS (O) dynamically assesses the trust level of each component based on its provenance, security posture, and observed behavior. It integrates with the bootstrapping process by validating the bootloader and influencing the trust level assigned to IES instances. The DTMS uses distributed consensus (P13) and blockchain technology (P15) to ensure the integrity and consistency of trust assessments.
VI. Interactions and Security Mechanisms:
The diagram highlights the sequential steps involved in bootstrapping and attestation, demonstrating the system's commitment to establishing a chain of trust from the ground up. The system utilizes a combination of hardware security (HRT, Secure Boot ROM), cryptographic verification (digital signatures, hashing), tamper detection (halt/alert), secure communication channels (P2, P3, P5, P26), and dynamic trust management to ensure the integrity and authenticity of the entire boot process and the resulting execution environment. The decentralized ledger provides a tamper-evident record for auditing and transparency. This multi-layered approach creates a robust and secure foundation for the ASKA system, mitigating a wide range of potential threats, including sophisticated attacks targeting the boot process.
Diagram 11a: Overview
graph LR
subgraph "ASKA Security Mesh"
IES[IES Instance]:::ies -- Data Plane (Passive/Read-Only) --> RAMSSD[RAM/SSD]:::data
LSM[LSM]:::lsm -- Data Plane (Passive/Read-Only) --> RAMSSD
Watcher[Watcher Mesh]:::watcher -- One-Way Control Plane --> LSM
Watcher -- Data Plane (Passive/Read-Only) --> RAMSSD
Watcher -- Bidirectional Control Plane --> AI[AI Hub]:::ai
MSM[MSM]:::msm -- One-Way Control Plane --> LSM
Watcher -- One-Way Control Plane --> MSM
End
classDef ies fill:#ccf,stroke:#333,stroke-width:1px
classDef lsm fill:#aaf,stroke:#333,stroke-width:1px
classDef watcher fill:#ddf,stroke:#333,stroke-width:1px
classDef msm fill:#f9f,stroke:#333,stroke-width:2px
classDef ai fill:#afa,stroke:#333,stroke-width:1px
classDef data fill:#ddd,stroke:#333,stroke-width:1px
Diagram 11b: Expanded
graph LR
subgraph RAM/SSD Banks
direction LR
RAM1[RAM<br>Bank<br>1]
SSD1[SSD<br>Bank<br>1]
RAM2[RAM<br>Bank<br>2]
SSD2[SSD<br>Bank<br>2]
end
subgraph IES Instance 1
direction LR
IES1[IES 1] -- Data Plane<br>(Read-Only) --> RAM1
IES1 -- Data Plane<br>(R/O) --> SSD1
end
subgraph IES Instance 2
direction LR
IES2[IES 2] -- Data Plane<br>(R/O) --> RAM2
IES2 -- Data Plane<br>(R/O) --> SSD2
end
subgraph LSM 1
direction LR
LSM1[LSM 1] -- Data Plane<br>(R/O) --> RAM1
LSM1 -- Data Plane<br>(R/O) --> SSD1
end
subgraph LSM 2
direction LR
LSM2[LSM 2] -- Data Plane<br>(R/O) --> RAM2
LSM2 -- Data Plane<br>(R/O) --> SSD2
end
subgraph LSM Watcher Mesh 1
LW1[LSM<br>Watcher<br>1] -- One-Way<br>Control Plane --> LSM1
LW1 -- Data Plane<br>(R/O) --> RAM1
LW1 -- Data Plane<br>(R/O) --> SSD1
end
subgraph LSM Watcher Mesh 2
LW2[LSM<br>Watcher<br>2] -- One-Way<br>Control Plane --> LSM2
LW2 -- Data Plane<br>(R/O) --> RAM2
LW2 -- Data Plane<br>(R/O) --> SSD2
end
subgraph MSM Watcher Mesh
MW[MSM<br>Watcher] -- One-Way<br>Control Plane --> MSM
end
subgraph "AI Cyber<br>Intelligence Hub"
AI[AI Hub]
end
subgraph MSM
MSM[Master Security Mesh]
end
MW -- Bidirectional<br>Control Plane --> AI
LW1 -- Bidirectional<br>Control Plane --> AI
LW2 -- Bidirectional<br>Control Plane --> AI
MSM -- One-Way<br>Control Plane --> LSM1
MSM -- One-Way<br>Control Plane --> LSM2
LW1 -- One-Way<br>Control Plane --> MSM
LW2 -- One-Way<br>Control Plane --> MSM
IES1 -- Monitored<br>by<br>LSM --> LSM1
IES2 -- Monitored<br>by<br>LSM --> LSM2
I. Core Components and their Interactions:
II. ASKA's Enhanced Security Posture:
The architecture elucidates ASKA's security posture in several ways:
III. Integration with Existing ASKA Features:
The security elements integrate seamlessly with ASKA as follows:
Goal: Eliminate step 4, preventing the AI Hub from directly instructing the LSM.
Proposals for Eliminating the Feedback Loop:
Proposal 1: AI Hub to ASKA Hub Enforcement:
Proposal 2: Decentralized Enforcement with Consensus:
graph
subgraph "Proposal 2: Decentralized Enforcement with Consensus"
subgraph IES Instance 1
LSM1[LSM 1] -- Passive Data Plane --> RAMSSD[RAM/SSD]
IES1[IES 1] -- Data Plane --> RAMSSD
Watcher1[Watcher 1] -- Unidirectional Control Plane --> LSM1
Watcher1 -- Passive Data Plane --> RAMSSD
end
subgraph IES Instance 2
LSM2[LSM 2] -- Passive Data Plane --> RAMSSD
IES2[IES 2] -- Data Plane --> RAMSSD
Watcher2[Watcher 2] -- Unidirectional Control Plane --> LSM2
Watcher2 -- Passive Data Plane --> RAMSSD
end
AIHub[AI Hub] -.-> Consensus["Consensus Engine (P13)"]
Watcher1 -.-> Consensus
Watcher2 -.-> Consensus
Consensus --> LSM1
Consensus --> LSM2
DTMS["DTMS (P4)"] -.-> Consensus
Consensus --> DLT["Decentralized Ledger (P13,P15)"]
style Consensus fill:#f9f,stroke:#333,stroke-width:2px
end
classDef ies fill:#ccf,stroke:#333,stroke-width:1px
classDef lsm fill:#aaf,stroke:#333,stroke-width:1px
classDef watcher fill:#ddf,stroke:#333,stroke-width:1px
classDef ai fill:#afa,stroke:#333,stroke-width:1px
classDef data fill:#ddd,stroke:#333,stroke-width:1px
This diagram illustrates the decentralized enforcement mechanism. Notice the absence of a direct connection between the AI Hub and the LSMs. Instead:
LSMs and Watchers: Each IES instance has an LSM and a Watcher Mesh, functioning as described previously. They connect to shared RAM/SSD resources.
Consensus Engine: The central component is the Consensus Engine (P13). The AI Hub, along with all other Watcher Meshes, sends its analysis and recommended actions to the Consensus Engine. The DTMS (for trust context) also provides input to the Consensus Engine.
Decentralized Enforcement: The Consensus Engine, using a distributed consensus protocol, reaches an agreement on the appropriate action. The dotted lines from the Consensus Engine back to the LSMs represent the enforcement commands. Critically, these commands are issued only after consensus is reached. This decentralized approach enhances security because no single entity (even a compromised AI Hub) can dictate actions. All consensus decisions are logged to the DLT.
Proposal 3: Hybrid Approach (Staged Enforcement):
graph LR
subgraph "Proposal 3: Hybrid Approach (Staged Enforcement)"
subgraph IES Instance 1
LSM1[LSM 1] -- Passive Data Plane --> RAMSSD[RAM/SSD]
IES1[IES 1] -- Data Plane --> RAMSSD
Watcher1[Watcher 1] -- Unidirectional Control Plane --> LSM1
Watcher1 -- Passive Data Plane --> RAMSSD
end
AIHub[AI Hub] --> Watcher1 -- Limited Actions --> LSM1
AIHub -.-> ASKAHub[ASKA Hub]
ASKAHub -- Policy Decisions --> PolicyEngine["Policy Engine (P4)"]
PolicyEngine -- Critical Actions --> LSM1
DTMS["DTMS (P4)"] -.-> PolicyEngine
DTMS -.-> AIHub
style ASKAHub fill:#ccf,stroke:#333,stroke-width:2px
style PolicyEngine fill:#ccf,stroke:#333,stroke-width:1px
end
classDef ies fill:#ccf,stroke:#333,stroke-width:1px
classDef lsm fill:#aaf,stroke:#333,stroke-width:1px
classDef watcher fill:#ddf,stroke:#333,stroke-width:1px
classDef ai fill:#afa,stroke:#333,stroke-width:1px
classDef data fill:#ddd,stroke:#333,stroke-width:1px
This diagram illustrates the hybrid approach.
Limited Actions: The AI Hub can directly instruct the Watcher Mesh, but only for a pre-defined set of "limited actions" that are considered low-risk. These actions might include increasing monitoring frequency, collecting more detailed logs, or performing specific, non-disruptive checks within the IES.
Critical Actions: For critical actions (isolation, termination), the AI Hub must communicate with the ASKA Hub. The Hub's Policy Engine evaluates the AI Hub's recommendation, considering existing policies and DTMS trust levels. If approved, the Hub issues the critical action command to the LSM.
DTMS Integration: The DTMS provides trust information both to the AI Hub (for its initial assessment) and the Policy Engine (for final authorization).
This hybrid approach balances the need for rapid response to less critical threats with the importance of strict control over high-impact actions.
Key Differences Visualized:
Proposal 2 features the Consensus Engine as the central decision-making component, with no direct AI Hub to LSM connection.
Proposal 3 shows the AI Hub capable of limited direct action through the Watcher Mesh, while critical actions still route through the ASKA Hub and Policy Engine.
Comparison and Selection:
Feature | Proposal 1 | Proposal 2 | Proposal 3 |
Security | High | Highest | Medium-High |
Speed | Low | Lowest | Medium |
Complexity | Medium | High | High |
Resilience | Medium | Highest | Medium-High |
Strongest Proposal: Proposal 2 (Decentralized Enforcement with Consensus) offers the highest security and resilience due to its decentralized nature and lack of a single point of failure. While it introduces complexity and potential latency, these trade-offs are acceptable for critical security functions. The consensus mechanism ensures that no single compromised component can dictate actions, significantly enhancing the overall security posture.
However, the complexity of implementing a robust and efficient distributed consensus mechanism should not be underestimated. Careful consideration must be given to the specific consensus protocol, network communication overhead, and potential scenarios where consensus might not be reached. A hybrid approach (Proposal 3) could be considered as a stepping stone towards full decentralization, allowing for faster response to less critical threats while the consensus mechanism is being developed and refined.
I. Core Principles Re-evaluation:
II. Data Plane Deep Dive - Reconsidering Passivity:
III. Anomaly Detection Re-evaluation:
IV. Control Plane Optimization:
V. Simpler Alternatives (trade-off considerations):
VI. Formal Verification Considerations (Throughout):
I. Deep Dive into Passive Data Plane:
II. Enhanced Anomaly Detection:
III. Streamlined Control Plane Communications:
IV. Enhanced AI Hub Architecture (Addressing Centralization):
V. Simplifying the Architecture:
VI. Formal Verification Strategy:
graph LR
subgraph ASKA["ASKA Instance"]
Hub((ASKA Hub)):::high_level
subgraph "Security Mesh"
subgraph "Security Mesh Instance"
SM_Instance{{"Security<br>Mesh<br>Instance"}}
end
IES_Mesh((IES<br>Instance)):::ies -- Data<br>Plane<br>(Read<Br>Only) --> RAMSSD[RAM/SSD]:::data
LSM_Mesh[LSM]:::lsm -- Data<br>Plane<br>(Read<br>Only) --> RAMSSD
Watcher_Mesh[Watcher Mesh]:::watcher -- One#8209;Way<br>Control<br>Plane --> LSM_Mesh
Watcher_Mesh -- Data<br>Plane<br>(Read<br>Only) --> RAMSSD
Watcher_Mesh -- Bidirectional<br>Control<br>Plane --> AI[AI Hub]:::ai
MSM[MSM]:::msm -- One#8209;Way<br>Control<br>Plane --> LSM_Mesh
Watcher_Mesh -- One#8209;Way<br>Contro<br>Plane --> MSM
end
IESCluster((("IES<br>Cluster"))):::medium_level
Network["Network<br>&<br>Communication"]:::network
DataResources["Data<br>&<br>Resources"]:::data
UIExternal["UI<br>&<br>External<br>Systems"]:::ui
AuditingGovernance["Auditing<br>&<br>Governance"]:::audit
Hub --> IESCluster
Hub --> Network
Hub --> DataResources
Hub --> UIExternal
Hub --> AuditingGovernance
Hub --> MSM
Hub --> AI
IESCluster -- Secure<br>Channel --> Network
IESCluster -- Resource<br>Access --> DataResources
IESCluster -- UI<br>Interactions --> UIExternal
IESCluster -- Audit<br>Trails --> AuditingGovernance
IESCluster -->|IES<br>Membership| SM_Instance
IES_Mesh -->|IES<br>Membership| SM_Instance
end
classDef high_level fill:#f9f,stroke:#333,stroke-width:2px
classDef medium_level fill:#ccf,stroke:#333,stroke-width:1px
classDef low_level fill:#aaf,stroke:#333,stroke-width:1px
classDef data fill:#afa,stroke:#333,stroke-width:1px
classDef ui fill:#ffa,stroke:#333,stroke-width:1px
classDef audit fill:#ccf,stroke:#333,stroke-width:1px
classDef network fill:#eec,stroke:#333,stroke-width:1px
classDef external fill:#d8d8d8,stroke:#333,stroke-width:1px
classDef ies fill:#ccf,stroke:#333,stroke-width:1px
classDef lsm fill:#aaf,stroke:#333,stroke-width:1px
classDef watcher fill:#ddf,stroke:#333,stroke-width:1px
classDef msm fill:#f9f,stroke:#333,stroke-width:2px
classDef ai fill:#afa,stroke:#333,stroke-width:1px
This diagram illustrates the integration of the Security Mesh within the broader ASKA architecture. The Security Mesh provides a crucial layer of defense, offering comprehensive, real-time, and compromise-resilient monitoring of system activity. This description details the components, interactions, and security benefits of this integration.
I. ASKA Hub:
The ASKA Hub is the central orchestration and management point for the entire system. It facilitates communication and coordination between all other components, including the Security Mesh. The Hub's responsibilities include:
II. Security Mesh:
The Security Mesh is a hierarchical, out-of-band monitoring system designed for comprehensive and compromise-resilient security.
III. Integration with ASKA Components:
Security Advantages of Security Mesh Integration:
graph LR
subgraph "Configuration Management Module (CMM)"
DLT["Decentralized Ledger (P13, P15)"] --> CMM
CMM --> DA[Deployment Agent]
DTMS["DTMS (P4)"] --> CMM
MSM["MSM (P2)"] --> CMM
AESDS["AESDS (P16)"] <--> CMM
IAMA["IAMA (P16)"] --> CMM
GovAI["Governance AI (P15)"] --> CMM
User["User Input (P11)"] --> CMM
end
DA --> AESDS
Policy["Policy Engine (P4)"] --> DA
DTMS --> DA
subgraph "Zone A"
IES_A["IES Cluster (P1)"]
end
subgraph "Zone B"
IES_B["IES Cluster (P1)"]
end
DA --> IES_A
DA --> IES_B
IES_A --> DLT
IES_B --> DLT
External[External Systems / Legacy] --> IAMA --> CMM
This diagram details the internal components and connections of the ASKA Configuration Management Module (CMM), highlighting its role in validating, generating, and deploying configurations while integrating with other key ASKA components.
Components:
graph TD
subgraph "Configuration Management Module (CMM)"
subgraph "Policy & TRC Validation"
DLT["Decentralized Ledger (P13, P15)"] --> TRC_Val["TRC Validator (P1, P4)"]
PolicyIn[Policy Input] --> PolicyVal["Policy Validator (P4)"]
TRC_Val --> Merge
PolicyVal --> Merge
Merge --> ConflictRes["Conflict Resolver (P13, P15)"]
ConflictRes --> ValidatedConfig
end
subgraph "Configuration Generation & Versioning"
ValidatedConfig --> ConfigGen[Configuration Generator]
User["User Input (P11)"] --> ConfigGen
Template[Configuration Templates] --> ConfigGen
ConfigGen --> Versioning[Version Control]
Versioning --> ConfigStore["Configuration Store (P24)"]
ConfigStore --> DA[Deployment Agent]
end
subgraph "Simulation & Analysis"
ValidatedConfig --> Sim[Policy Simulator]
Sim --> Analysis["Impact Analysis (AI - P10, P16)"]
Analysis --> SimResults["Simulation Results (P11)"]
SimResults --> User
end
subgraph "ASKA Integration"
DTMS["DTMS (P4)"] --> PolicyVal
DTMS --> ConflictRes
DTMS --> DA
MSM["MSM (P2)"] --> Analysis
AESDS["AESDS (P16)"] <--> ConfigGen
IAMA["IAMA (P16)"] --> ConfigGen
end
subgraph Governance AI Feedback
GovAI["Governance AI (P15)"] --> Analysis
GovAI --> ConflictRes
end
end
The diagram details the architecture and operational flow of the CMM within the ASKA secure computing environment. The CMM is responsible for the secure and efficient management of configurations, encompassing validation, generation, simulation, and deployment. It achieves this through a combination of policy and TRC validation, configuration generation and versioning, impact simulation and analysis, and deep integration with other ASKA security modules.
Component Summary:
Detailed Process and ASKA Integration
The CMM process begins with the retrieval of TRCs and the input of new policies. The TRC Validator (leveraging Patent 1 and 4) ensures the integrity of retrieved TRCs, while the Policy Validator (P4) checks the validity of incoming policies. These validated components are merged, and any conflicts are resolved by the Conflict Resolver, which consults the DTMS (P4) for trust information and the Governance AI (P15) for higher-level policy directives. The Conflict Resolver uses either pre-defined rules, consensus mechanisms, or a combination of approaches depending on the nature of the conflict and the specific policies involved. Resolution details are logged on the DLT for transparency.
The resulting Validated Config is then used by the Configuration Generator to create the necessary configuration artifacts. This process may involve user input (P11) and leverage predefined Configuration Templates. Critically, the Configuration Generator integrates with AESDS (P16) allowing for automated generation of optimized code and configuration files, further enhancing security by incorporating best practices and mitigating potential vulnerabilities. The IAMA module (P16) feeds information about legacy systems to the Configuration Generator, enabling it to create configurations that are both secure and backward-compatible.
Before deployment, the validated configuration can be fed into the Policy Simulator, which, combined with the Impact Analysis module (using AI – P10, P16), provides insights into the potential effects of the changes. This process integrates with the MSM (P2) for real-time security context and the Governance AI (P15) for alignment with strategic objectives. Simulation Results are presented to the user via the Secure UI (P11) for review and approval. This feedback loop allows administrators to fine-tune configurations before they are deployed, minimizing risks and optimizing for desired outcomes.
The finalized configuration is then stored in the Configuration Store, secured by HESE-DAR (P24). The Deployment Agent (DA) retrieves the configuration from this secure store and orchestrates its deployment to target components (IES clusters, network elements, etc.), leveraging DTMS (P4) for authorization and secure communication channels. The entire process, including configuration changes, deployments, simulations, and resolutions, is logged on the Decentralized Ledger (DLT - P13, P15), creating a comprehensive audit trail secured by MDATS (P17).
Security Considerations:
This architecture tightly integrates with ASKA's security infrastructure:
graph LR
subgraph "ASKA Hub"
subgraph "Configuration Management (CMM)"
DLT["Decentralized Ledger (P13, P15)"] --> CMM
CMM --> DA[Deployment Agent]
end
DA --> AESDS["AESDS (P16)"]
Policy["Policy Engine (P4)"] --> DA
DTMS["DTMS (P4)"] --> DA --> IES_Clusters
end
subgraph "IES Clusters (P1)"
IES1[IES 1] --> Local_Err1["Local Error Module (P7)"]
IES2[IES 2] --> Local_Err2["Local Error Module (P7)"]
IESn[IES n] --> Local_Errn["Local Error Module (P7)"]
subgraph IES 1
App1["Application 1"] --> Local_Log1[Local Error Log] --> Local_Err1
Kernel1[Secure Kernel] --> Local_Log1
end
subgraph IES 2
App2["Application 2"] --> Local_Log2[Local Error Log] --> Local_Err2
Kernel2[Secure Kernel] --> Local_Log2
end
subgraph IES n
Appn["Application n"] --> Local_Logn[Local Error Log] --> Local_Errn
Kerneln[Secure Kernel] --> Local_Logn
end
Local_Err1 --> ErrAgg
Local_Err2 --> ErrAgg
Local_Errn --> ErrAgg
end
subgraph "Out#8209;of#8209;Band Error Module (P35)"
ErrAgg[Error Aggregator] --> Redactor["Secure Log Redactor (P16, P17)"]
Redactor --> LevelA[Security Level A Output]
Redactor --> LevelB[Security Level B Output]
Redactor --> LegacyOut[Legacy System Output]
DTMS --> Redactor
MSM["MSM (P2)"] --> ErrAgg
end
subgraph "Multi#8209;Channel Network (P3)"
LevelA --> ChannelA[Secure Channel A]
LevelB --> ChannelB[Secure Channel B]
LegacyOut --> ChannelL[Legacy Channel]
ChannelA --> SIEM[SIEM Integration]
ChannelB --> SIEM
ChannelL --> SIEM_Legacy[Legacy SIEM]
subgraph "Dedicated Unswitched Network Paths"
ChannelA --> SIEM
ChannelB --> SIEM
ChannelC["Secure Channel C <br> (for future use)"] --> SIEM
ChannelD["Secure Channel D <br> (for future use)"] --> SIEM
end
end
subgraph "External Systems / Legacy"
IAMA["IAMA (P16)"] --> CMM
External[External Systems] --> SIZCF["SIZCF (P22)"]
end
External --> STN["STN (P27)"] --> DTG["DTG (P28)"] --> ATN["ATN (P3)"] --> IES_Clusters
DLT --> STN
DLT --> CMM
DLT --> ErrAgg
HESE_DAR["HESE-DAR (P24)"] --> IES_Clusters
HESE_DAR --> STN
HESE_DAR --> CMM
AESDS <--> CMM
SecureUI["Secure UI Kernel (P11)"] --> IES_Clusters
graph
%% Defining color-coded classes
classDef hub fill:#FFEBE5,stroke:#FF6B4A,stroke-width:2px,color:#5A1B00;
classDef agent fill:#E5F4FF,stroke:#409EFF,stroke-width:2px,color:#003152;
classDef integration fill:#E5FFEB,stroke:#34D399,stroke-width:2px,color:#00663C;
classDef monitoring fill:#FFF5E5,stroke:#FFA740,stroke-width:2px,color:#553000;
classDef optional fill:#F0E5FF,stroke:#A855F7,stroke-width:2px,color:#3C0061;
classDef user fill:#FFF0F0,stroke:#FF5252,stroke-width:2px,color:#5A0000;
subgraph "ASKA Hub"
AggHub((Aggregation & Processing Hub)):::hub --> SecureUI(["Secure<br>UI<br>Kernel<br>(P11)"]):::hub
DTMS["DTMS<br>(P4)"]:::hub --> AggHub
MSM{{"MSM<br>(P2)"}}:::hub --> AggHub
Policy{"Policy<br>Engine<br>(P4)"}:::hub --> AggHub
end
subgraph "AI Agent IES (P1)"
subgraph "LLM Engine"
ModelStore{{"Model<br>Storage<br>(HESE-DAR - P24)"}}:::agent --> InferenceEngine(["Inference Engine (P12)"]):::agent
Tokenizer((Tokenizer)):::agent --> InferenceEngine
Context{{"Context<br>Management"}}:::agent --> InferenceEngine
end
subgraph "ASKA Integrations"
DTMSint{{"DTMS<br>Integration<br>(P4, P25)"}}:::integration <--> DTMS
MSM --> MSMint(["MSM<br>Integration<br>(P2)"]):::integration
AESDS{{"AESDS<br>(P16)"}}:::integration --> AESDSint(["AESDS<br>Integration<br>(P16)"]):::integration
DLTint{{"DLT<br>Integration<br>(P13, P15, P3)"}}:::integration <--> DLT((Decentralized<br>Ledger)):::integration
RMint(["Resource<br>Mgr<br>Integration<br>(P9, P10)"]):::integration <--> RM((Resource<br>Manager)):::integration
SIZCFint(["SIZCF<br>Integration<br>(P22)"]):::integration <--> SIZCF{{"SIZCF"}}:::integration
IAMAint{{"IAMA<br>Integration<br>(P16)"}}:::integration <--> IAMA((IAMA)):::integration
end
subgraph "UI Monitoring Module"
UI_Kernel(("Secure UI Kernel<br>(P11)")):::monitoring -- Data Diode (P2) --> UI_Monitor{{"UI<br>Monitor"}}:::monitoring
UI_Monitor --> Sanitizer((Sanitizer/<br>Filter)):::monitoring --> LLMEngineIn["LLM<br>Inference<br>Parser"]
end
LLMEngineIn --> InferenceEngine
InferenceEngine --> AgentAPI(("Agent API<br>(P2, P25)")):::agent
AgentAPI --> AggHub
subgraph "Optional Components (Future)"
FLint{{"Federated<br>Learning<br>Integration<br>(P19)"}}:::optional
ExtInt((External<br>System<br>Integration)):::optional
end
end
User(((User))):::user --> SecureUI
SecureUI -.-> UI_Kernel
class AggHub,SecureUI,DTMS,MSM,Policy hub
class ModelStore,InferenceEngine,Tokenizer,Context,LLMEngineIn,AgentAPI agent
class DTMSint,MSMint,AESDS,AESDSint,DLTint,RMint,SIZCFint,IAMAint integration
class UI_Kernel,UI_Monitor,Sanitizer monitoring
class FLint,ExtInt optional
class User user
Component and Connection Details:
flowchart TD
subgraph "AI Agent IES (P1)"
subgraph "ASKA Hub(Not in AI Agent)"
AESDS(("AESDS<br>(P16)")) --> UpdateMgr((("Update<br>Manager")))
Policy{{"Policy Engine<br>(P4)"}} --> UpdateMgr
UpdateMgr --> MCN[/"Multi-Channel<br>Network<br>(P3, P5)"/]
DTMS(("DTMS<br>(P4)")) --> UpdateMgr
MSM(["MSM<br>(P2)"]) --> |Monitoring| LLM_Engine
UpdateMgr -.- DLT{{"Decentralized Ledger<br>(P13, P15)"}}
RM["Resource Manager<br>(P10)"] --> UpdateMgr
end
subgraph "LLM Engine"
UpdatePkg{{"Update Package<br>(Signed & Verified)"}} --> Installer((Installer))
HESE_DAR["HESE-DAR<br>(P24)"] --> |Secure Storage| ModelStore[(Model<br>Storage)]
ModelStore --> InferenceEngine(("Inference Engine<br>(P12)"))
Tokenizer[/Tokenizer/] --> InferenceEngine
Context["Context<br>Management"] --> InferenceEngine
Installer --> ModelStore
Installer --> Rollback(("Rollback<br>Mechanism"))
Rollback --> ModelStore
IAMA{{"IAMA<br>(P16)"}} --> Sandbox(("Sandbox<br>(P1)"))
Sandbox --> Validation{{"Validation Results"}} --> Installer
end
LLM_Engine --> AgentAPI(("Agent API<br>(P2, P25)"))
AgentAPI --> |Results/Actions| AggHub["Aggregation &<br>Processing Hub"]
AggHub --> SecureUI(("Secure UI Kernel<br>(P11)"))
User(["User"]) --> SecureUI
Integrations{{"ASKA Integrations<br>(P2, P3, P4, P13, P15)"}} <--> DTMS
Integrations -.- MSM
Integrations -.- AESDS
end
MCN ----> UpdatePkg
UpdateMgr ----> IAMA
%% Define styles
classDef mainNode fill:#FFDAC1,stroke:#FF9AA2,stroke-width:2,color:#333;
classDef policyNode fill:#B5EAD7,stroke:#70C1B3,stroke-width:2,color:#333;
classDef networkNode fill:#FFB7B2,stroke:#F08080,stroke-width:2,color:#333;
classDef engineNode fill:#F3E9F0,stroke:#FF7171,stroke-width:2,color:#333;
classDef storageNode fill:#FFDAC1,stroke:#FF9AA2,stroke-width:2,color:#333;
classDef processNode fill:#D7DEEA,stroke:#A2C2F4,stroke-width:2,color:#333;
%% Apply styles to specific nodes
class AESDS,UpdateMgr,UpdatePkg,AggHub,Sandbox,Sandbox storageNode;
class Policy,DLT,RM,AgentAPI,IAMA,Validation,SecureUI,Integrations policyNode;
class MCN,MSM,LLM_Engine,DTMS networkNode;
class InferenceEngine,Installer,Rollback engineNode;
class ModelStore,HESE_DAR storageNode;
class User,Tokenizer,Context processNode;
Components and Connections:
graph TD
subgraph "ASKA Security System"
subgraph "Master Security Mesh (MSM #8209; P2)"
MSM --> ThreatIntelFeed(["Threat<br>Intelligence<br>Feed"])
MSM --> NetworkMon(("Network<br>Monitor<br>(P3)"))
MSM --> SystemMon{{"System<br>Monitor<br>(P7,<br>P8)"}}
MSM --> LocalMSMs[["Local<br>Security<br>Meshes<br>(P2)"]]
ThreatIntelFeed --> AnomalyDetection(("Anomaly<br>Detection<br>Engine<br>(P7)"))
AnomalyDetection --> MSM
NetworkMon --> MSM
SystemMon --> MSM
LocalMSMs --> MSM
AnomalyDetection --> AlertSystem(("Alert<br>System<br>(P7)"))
end
subgraph "Onboard AI Agent (Security Module)"
subgraph "Threat Analysis Hunting"
ThreatIntelFeed --> AI_ThreatIntel([AI<br>Threat<br>Intelligence])
AI_ThreatIntel --> ProactiveHunting((Proactive<br>Threat<br>Hunting))
ProactiveHunting --> ThreatReports{{Threat<br>Reports}}
MSM --> AI_ThreatIntel
AnomalyDetection --> AI_AnomalyAnalysis([AI<br>Anomaly<br>Analysis])
AI_AnomalyAnalysis --> ThreatReports
end
subgraph "Alert Prioritization & Response"
AlertSystem --> AI_AlertPrioritization([AI<br>Alert<br>Prioritization])
AI_AlertPrioritization --> PrioritizedAlerts{{Prioritized<br>Alerts}}
AI_AlertPrioritization --> AutomatedResponse(("Automated<br>Response<br>(P7)"))
AutomatedResponse --> ResponseSystem{{"Response<br>System<br>(P7)"}}
end
UI_Kernel(["Secure<br>UI<br>Kernel<br>(P11)"]) -- "Data<br>Diode<br>(P2)" --> UI_Monitor((UI<br>Monitor))
UI_Monitor --> AI_AlertPrioritization
UI_Monitor --> AI_AnomalyAnalysis
subgraph "Detailed Reporting Analysis"
ThreatReports --> DetailedAnalysis{{Detailed<br>Threat<br>Analysis}}
DetailedAnalysis --> RemediationRecommendations([Remediation<br>Recommendations])
end
subgraph "ASKA Integration"
DTMS(["DTMS<br>(P4)"]) --> AI_AlertPrioritization
DTMS --> AI_ThreatIntel
DLT(("Decentralized<br>Ledger<br>(P13,<br>P15)")) --> AI_ThreatIntel
DLT --- AI_AlertPrioritization
DLT --- DetailedAnalysis
AgentAPI([Agent<br>API]) --> ResponseSystem
ConsensusEngine(("Consensus<br>Engine<br>(P13)")) --> SecurityActions{{Security<br>Actions}}
AI_AnomalyAnalysis --> ConsensusEngine
AI_AlertPrioritization --> ConsensusEngine
AI_ThreatIntel --> ConsensusEngine
end
end
ResponseSystem --> MSM
SecurityActions --> ResponseSystem
RemediationRecommendations --> SecurityPersonnel([Security<br>Personnel])
PrioritizedAlerts --> SecurityPersonnel
SecurityReports([Security<br>Reports]) --> SecurityPersonnel
ThreatReports --> SecurityReports
DetailedAnalysis --> SecurityReports
end
style MSM fill:#ffcccb,stroke:#e63946,stroke-width:2px
style ThreatIntelFeed fill:#a8dadc,stroke:#457b9d,stroke-width:2px
style NetworkMon fill:#ffd60a,stroke:#f1faee,stroke-width:2px
style SystemMon fill:#b0f9b6,stroke:#264653,stroke-width:2px
style LocalMSMs fill:#f1faee,stroke:#1d3557,stroke-width:2px
style AnomalyDetection fill:#e9c46a,stroke:#f4a261,stroke-width:2px
style AlertSystem fill:#b0f9b6,stroke:#264653,stroke-width:2px
style AI_ThreatIntel fill:#ffd60a,stroke:#f1faee,stroke-width:2px
style ProactiveHunting fill:#a8dadc,stroke:#457b9d,stroke-width:2px
style ThreatReports fill:#ffcccb,stroke:#e63946,stroke-width:2px
style AI_AnomalyAnalysis fill:#b0f9b6,stroke:#264653,stroke-width:2px
style AI_AlertPrioritization fill:#e9c46a,stroke:#f4a261,stroke-width:2px
style PrioritizedAlerts fill:#ffd60a,stroke:#f1faee,stroke-width:2px
style AutomatedResponse fill:#f1faee,stroke:#1d3557,stroke-width:2px
style ResponseSystem fill:#b0f9b6,stroke:#264653,stroke-width:2px
style DTMS fill:#a8dadc,stroke:#457b9d,stroke-width:2px
style DLT fill:#ffcccb,stroke:#e63946,stroke-width:2px
style AgentAPI fill:#ffd60a,stroke:#f1faee,stroke-width:2px
style ConsensusEngine fill:#b0f9b6,stroke:#264653,stroke-width:2px
style SecurityActions fill:#e9c46a,stroke:#f4a261,stroke-width:2px
style SecurityPersonnel fill:#f1faee,stroke:#1d3557,stroke-width:2px
linkStyle 0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18 stroke:#555,stroke-width:2px
This diagram illustrates the integrated operation of ASKA's security system, highlighting the collaborative relationship between the Master Security Mesh (MSM) and the Onboard AI Agent. It emphasizes how these two subsystems work together, leveraging a consensus-driven approach, to provide comprehensive and robust security within ASKA.
1. Master Security Mesh (MSM - P2): The MSM acts as the central nervous system for ASKA's security, collecting and correlating data from various sources:
The data from these sources feeds into the Anomaly Detection Engine (P7), which analyzes it for anomalies and potential threats. The Anomaly Detection Engine then triggers the Alert System (P7) to generate alerts for security incidents.
2. Onboard AI Agent (Security Module): This intelligent agent enhances the security system by providing advanced analysis, proactive threat hunting, and context-aware alert prioritization. It's crucial to understand that this agent is not part of the MSM but works in conjunction with it.
3. Consensus-Driven Security:
The diagram highlights the consensus-driven nature of the security system:
4. Human Oversight: Ultimately, Security Personnel receive Prioritized Alerts, Security Reports, and Remediation Recommendations, providing human oversight of the AI-driven security process.
Consensus-Driven AI Security:
The Consensus Engine uses a distributed consensus algorithm (similar to those used in blockchain - P13, P15) to reach an agreement on the appropriate security actions. This consensus-driven approach prevents any single AI component from making potentially disruptive security decisions unilaterally. It also increases resilience against manipulation or compromise of individual AI modules.
How the Consensus Mechanism Works:
Example Scenario:
The Network Monitor detects unusual network traffic patterns. The Anomaly Detection Engine flags this as a potential DDoS attack. Simultaneously, the UI Monitor observes the user attempting to access a restricted resource. The AI Agent correlates these events and proposes blocking the user's access and implementing rate-limiting on the affected network interface. The Consensus Engine receives this proposal and other inputs from the Threat Intelligence module. If a consensus is reached, the Response System takes the appropriate actions, while a detailed report is generated for security personnel.
This enhanced design integrates a robust consensus mechanism into the AI-driven security system, leveraging insights from multiple sources (UI, system internals, threat intelligence) and preventing any single AI component from making critical security decisions autonomously. The use of a distributed consensus algorithm adds resilience and transparency to the system, further strengthening ASKA's comprehensive security posture.
graph LR
subgraph "ASKA Hub (P4)"
DTMS(("DTMS<br>(P4)")) --> ASKA
end
subgraph "ASKA"
subgraph "ASKA Environment"
subgraph "Secure Data Enclaves (P20)"
AI_Model(("AI<br>Model<br>(P20)")) --> SecureDataEnclaves["Data<br>Enclaves"]
Federated_Learning(("Federated<br>Learning<br>(P19)")) --> SecureDataEnclaves
end
subgraph "Secure Kernel (P1)"
subgraph "Hardware Isolation (IES - P1)"
BCI_Hardware(("BCI<br>Hardware<br>(P1)")) --> IES
end
SecureKernel["Kernel"] --> SecureDataEnclaves
SecureKernel --> Encryption(("Encryption<br>(P2)"))
subgraph "Trusted Execution Environment (TEE)"
AI_Agent(("AI<br>Agent<br>(P16, P20)")) --> TEE
end
subgraph "Data Storage (P24)"
HESE_DAR(("HESE-DAR<br>(P24)")) --> SecureDataEnclaves
HESE_DAR --> Access_Control["Access<br>Control<br>(P2, P25)"]
end
end
subgraph "Network Channels"
subgraph "Secure Channels (P3, P5)"
subgraph "Secure Cloud"
Cloud_Service(("Cloud<br>Service")) --> SecureChannels["Secure<br>Channels>"]
end
SecureChannels --> SecureKernel
end
end
end
subgraph "Security Mechanisms"
Encryption(("Encryption<br>(P2)")) --> ASKAEnvironment["ASKA<br>Environment"]
Data_Diodes(("Data Diodes<br>(P2)")) --> ASKAEnvironment
TEE((TEE)) --> ASKAEnvironment
Non_Switchable_Channels(("Non-Switchable<br>Channels<br>(P3, P5)")) --> ASKAEnvironment
end
end
subgraph "User Interface"
UI_Kernel(("UI<br>Kernel<br>(P11)")) --> Data_Diode["Data<br>Diode"]
Data_Diode --> SecureKernel
UI_Kernel --> UI_Monitor((UI<br>Monitor))
UI_Monitor --> PrioritizedAlerts((Prioritized<br>Alerts))
subgraph "User"
UserX((User<br>Action))
UserX --> UI_Monitor
UserX --> PrioritizedAlerts
end
subgraph "BCI Input"
BCI_Input((BCI<br>Input)) --> UI_Monitor
end
end
PrioritizedAlerts --> AI_AlertPrioritization((AI<br>Alert<br>Prioritization))
AI_AlertPrioritization --> SecureKernel
UI_Monitor --> AI_AnomalyAnalysis((AI<br>Anomaly<br>Analysis))
AI_AnomalyAnalysis --> SecureKernel
UI_Monitor --> AI_ThreatIntel((AI<br>Threat<br>Intelligence))
AI_ThreatIntel --> SecureKernel
%% Define styles
classDef pastelNode fill:#D1E8E4,stroke:#A8D8D0,stroke-width:2
classDef pastelEdge stroke:#345774,stroke-width:1
%% Apply styles to nodes and edges
class DTMS,AI_Model,Federated_Learning,BCI_Hardware,SecureKernel,Encryption,AI_Agent,HESE_DAR,Access_Control,UI_Kernel,UI_Monitor,PrioritizedAlerts,UserX,BCI_Input,AI_AlertPrioritization,AI_AnomalyAnalysis,AI_ThreatIntel pastelNode;
class DTMS,AI_Model,Federated_Learning,BCI_Hardware,SecureKernel,Encryption,AI_Agent,HESE_DAR,Access_Control,UI_Kernel,UI_Monitor,PrioritizedAlerts,UserX,BCI_Input,AI_AlertPrioritization,AI_AnomalyAnalysis,AI_ThreatIntel pastelEdge;
Explanation:
Key Points:
graph
subgraph "Client"
ClientApp[ASKA<br>Remote Client] --> SecureChannel["Secure Communication<br>(P2, P3, P5)"]
end
subgraph "ASKA Hub"
direction LR
Auth["Authentication<br>(MFA - P23)"] --> SessionMgr[Session Manager]
SessionMgr --> CapMgr["Capability Manager<br>(P25)"]
DTMS["DTMS (P4)"] --> SessionMgr
SessionMgr --> UI_Session_IES[Remote UI Session IES]
SessionMgr --> AuditLog["Audit Log<br>(P13, P15, P17)"]
AuditLog --> DLT["Decentralized Ledger"]
end
subgraph "Remote UI Session IES (P1)"
direction LR
UI_Session_IES --> SecureUI["Secure UI Kernel (P11)"]
SecureUI --> InputSanitizer["Input<br>Sanitizer<br>(P11)"]
InputSanitizer --> RenderingEngine["Rendering Engine"]
RenderingEngine --> SecureChannel
UI_Session_IES --> SessionMonitor["Session Monitor<br>(P2, P7)"]
SessionMonitor --> MSM["MSM (P2)"]
end
SecureChannel --> ClientApp
MSM --> SessionMgr
style Client fill:#ccf,stroke:#333,stroke-width:2px
This diagram shows the architecture of the Secure Remote UI Session system. The client establishes a secure connection to the ASKA Hub, which manages authentication, authorization, and session parameters. The Hub then creates a dedicated IES instance to host the session, which is monitored for anomalies. The UI rendering and data transfer are securely managed, with input sanitization to prevent attacks.
graph LR
subgraph ASKA Hub
direction LR
SessionMgr[Session Manager] --> DTMS["DTMS (P4)"]
SessionMgr --> CapMgr["Capability Manager (P25)"]
SessionMgr --> AuditLog["Audit Log (P13, P15, P17)"]
AuditLog --> DLT["Decentralized Ledger"]
SessionMgr --> MSM["MSM (P2)"]
SessionMgr --> PolicyEngine["Policy Engine (P4)"]
SessionMgr --> OnboardAI["Onboard AI Agent (if available)"]
end
subgraph "Remote UI Session IES (P1)"
UI_Session_IES[Remote UI Session IES] --> MSM
UI_Session_IES --> DTMS
UI_Session_IES --> InputSanitizer["Input Sanitizer (P11)"]
end
This diagram highlights the integration points of the Secure Remote UI Session system within ASKA. The Session Manager interacts with key ASKA components for authentication (MFA), authorization (Capabilities), auditing (Decentralized Ledger and MDATS), security monitoring (MSM), and policy enforcement (Policy Engine). The Onboard AI Agent, if present, further enhances security with real-time threat detection and response. The Remote UI Session IES receives policy updates and trust level information from the DTMS and passes session-related information (for monitoring and analysis) to the MSM. Input sanitization within the Remote UI Session IES prevents injection attacks.
Abbreviation | Full Name | Short Description |
AESDS | Automated Evolutionary Software Development System | AI-driven system for software evolution and secure deployment. |
DTMS | Dynamic Trust Management System | Manages trust relationships and access control based on dynamic metrics. |
IAMA | Isomorphic Architecture Monitoring & Adaptation | Monitors legacy systems and generates proactive security patches. |
STN | Sovereign Trust Network | Isolated data plane for secure communication. |
DTG | Dynamic Trust Gateway | Mediates communication between ATN and STN. |
ATN | Authenticated Trust Network | Network with authenticated communication. |
HESE-DAR | Hardware-Enforced Secure Encrypted Enclave for Data at Rest | Hardware-based encryption for data at rest. |
IES | Isolated Execution Stack | Hardware-isolated execution environment. |
ZKEE | Zero-Knowledge Execution Environment | Allows computations on encrypted data without revealing underlying information. |
MSM | Hierarchical Security Mesh | Multi-layered security monitoring system. |
Hub | ASKA Hub | Central control and management component. |
CapMgr | Capability Manager | Manages capabilities for inter-IES communication. |
PolicyEngine | Policy Engine | Enforces security policies. |
ResourceMgr | Resource Manager | Manages resource allocation. |
ChannelMgr | Channel Manager | Manages the multi-channel network. |
Secure_Channel | Secure Channels | Secure communication channels. |
External_Systems | External Systems | Systems outside of the ASKA environment. |
Firewall | Firewall | Network firewall. |
SecureUI | Secure UI Kernel | Secure and isolated user interface. |
DLT | Decentralized Ledger | Distributed ledger for secure record-keeping. |
MDATS | Multi-Dimensional Audit Trail System | Combines digital and physical audit trails. |
UI_Integration | UI Integration Module | Facilitates communication between ASKA Hub and Secure UI. |
SIZCF | Secure Inter-Zone Collaboration Framework | Enables secure collaboration between different zones. |
AnomalyDetector | Anomaly Detector | Detects anomalies in system behavior. |
LocalMSM | Local Security Mesh | Local security monitoring within an IES. |
SecureStorage | Secure Storage | Secure storage for encrypted data. |
GovernanceAI | Governance AI | AI-driven component for governance auditing and transparency. |
QEAMS | Quantum-Entangled Auxiliary Memory System | Provides out-of-band integrity verification for data using quantum entanglement. |
SAMS | Spatiotemporal Auxiliary Memory System | Provides out-of-band integrity verification using spatiotemporal metadata. |
PR-SAMS | Passively Radiative Spatiotemporal Auxiliary Memory System | A low-power version of SAMS using passive radiative sensing. |
QE-OTP | Quantum Entangled One Time Pad | A one time pad using quantum key exchange. |
SHVS | Secure Hyper-Virtualization System | Enables secure and isolated execution environments within ASKA, supporting collaborative workloads. |
CE-PCFS | Capability-Enhanced Packet-Carried Forwarding State | Provides fine-grained access control for communication between IES instances within ASKA. |
SIBRA | Secure Inter-Broker Routing Algorithm | Ensures quality of service (QoS) for secure communication paths, particularly for bandwidth-intensive applications. |
MPC | Secure Multi-Party Computation | Enables privacy-preserving collaborative machine learning across multiple ASKA instances. |
CFI | Control-Flow Integrity | Protects the Secure UI Kernel against code injection attacks. |
DPI | Deep Packet Inspection | Examines data packets to enforce security policies and detect malicious activity within the DTG. |