2-ASKA Overview-2 20241031
Written by: Paul Lowndes <[email protected]>
Table of Contents
Diagram 1a through 1f: ASKA Architecture Overview
Diagram 2a and 2b: IES Lifecycle Management within ASKA Hub
Diagram 3a and 3b: Communication Flow within the Multi-Channel Network
Diagram 4: HESE-DAR Detailed Data Flow
Diagram 5: ASKA Zone Interaction via SIZCF
Diagram 6a through 6c: AESDS AI Engine
Diagram 7: Chiplet Integration Lifecycle
Diagram 8: Decentralized Governance Process (Voting)
Diagram 9: Automated Evolutionary Software Development System (AESDS) Lifecycle
Diagram 10: Adaptive Multi-Channel Network - The Quantum Highway
Diagram 11: Dynamic Trust Management System (DTMS) in Action
Diagram 12: Data Enclave - The Sanctuary
Diagram 13a through 13d: Hub - The Command Center
Diagram 14: Control / Data Planes
Diagram 15: Detailed Integration
Diagram 16a through 16f: Automated Software and Trust Systems Integration
Deep Dive: Automated Software and Trust Systems Integration (Diagram 16a - 16f)
Diagram 16b: AESDS with IAMA Module (Patent 16, Claim 9)
Diagram 16c: STN Externals (Patent 27)
Diagram 16d: STN Internals (Patent 28)
Diagram 16e: DTG Internals (Patent 28)
Diagram 16f: External Integrations
Diagram 1 (a-f): ASKA Architecture Overview:
This series of diagrams provides a layered view of ASKA, starting with a high-level overview and progressively zooming in on specific components:
Diagram 2 (a-b): IES Lifecycle Management:
Illustrates how the ASKA Hub's Orchestrator manages the lifecycle of IES instances, including provisioning, deployment (with secure boot), scaling, termination, and integration with AESDS, MSM, and the Policy Engine.
Diagram 3 (a-b): Multi-Channel Network Communication:
Shows how IES instances communicate through the Multi-Channel Network. Highlights capability-aware NICs, secure channels with different trust levels, the out-of-band firewall, and the Channel Manager's dynamic routing based on DTMS trust policies and MSM threat intelligence.
Diagram 4: HESE-DAR Data Flow:
Details the secure access, encryption, and decryption process within HESE-DAR. Shows the flow of data requests from applications through the IOMMU, access control checks, key management, the crypto engine, secure storage, and integration with MSM and DTMS.
Diagram 5: SIZCF Zone Interaction:
Illustrates how ASKA zones securely collaborate via SIZCF. Shows zone discovery, trust assessment using DTMS, secure communication channel establishment, data sanitization and exchange, and distributed ledger synchronization.
Diagram 6 (a-c): AESDS AI Engine:
Visualizes the AI engine within AESDS, responsible for code generation and refinement. Shows the knowledge base, dynamic input streams (performance metrics, user feedback, threat intelligence), ASKA integration, the IES sandbox environment, and code deployment.
Diagram 7: Chiplet Integration Lifecycle:
Details the process of integrating chiplets into an IES, including insertion, authentication, resource allocation, workload assignment, operation, and removal, managed by the Chiplet Orchestration Module.
Diagram 8: Decentralized Governance (Voting):
Illustrates a secure voting scenario, demonstrating ASKA's decentralized governance. Shows voter authentication, vote casting, secure tallying on the DLT, audit trail generation using 3D microstructures, and verification by auditors.
Diagram 9: AESDS Lifecycle:
Visualizes the continuous loop of software development within AESDS: AI-driven code generation, testing in IES sandboxes, validation, decentralized governance approval, secure deployment, monitoring, feedback collection, and integration with the 3D Microstructure system for auditing.
Diagram 10: Adaptive Multi-Channel Network:
Visualizes the Multi-Channel Network as a "Quantum Highway" with different trust levels (lanes). Shows dynamic rerouting by the Channel Manager based on DTMS and MSM input, firewall checkpoints, and quantum-resistant gateways for external communication.
Diagram 11: DTMS in Action:
Illustrates the dynamic trust evaluation process within DTMS. Shows an IES instance requesting access to a protected resource, with the DTMS considering trust level, monitoring data, threat intelligence, and policies to make a consensus-based access decision.
Diagram 12: Data Enclave:
Visualizes the secure data enclave, emphasizing layered security and privacy-preserving analysis. Shows data ingestion, validation, MPC, differential privacy, homomorphic encryption, sanitized output, and integration with DTMS and the decentralized ledger for auditing.
Diagram 13 (a-d): ASKA Hub:
Depicts the Hub as a command center, showing operators monitoring real-time information (IES status, network traffic, security alerts, resource utilization). Details the Hub's internal modules, their connections to external components, and operator interaction.
Diagram 14: Control/Data Planes:
Illustrates the separation of control and data planes within ASKA, showing how different components participate in each plane and how they coordinate. Includes the Secure UI Plane and the Decentralized Ledger for auditing.
Diagram 15: Detailed Integration:
Provides a comprehensive integration view, showing the internal workings of an IES (including child IES and zones), inter-IES communication mechanisms, the ASKA Hub components, the multi-channel network, external systems/zones, and data services.
Diagram 16 (a-f): Automated Software and Trust Systems Integration:
This series provides a deep dive into how AESDS integrates with the STN and DTG:
graph LR
subgraph "ASKA Zone (Patents 17, 18)"
direction LR
subgraph "ASKA Hub (Patents 1, 4, 16, 22)"
Hub["ASKA Hub"] -->|"Orchestration & Mgmt"| IES_Clusters
Hub -->|"Security Mgmt"| MSM
Hub ---->|"Trust Mgmt"| DTMS
Hub ---->|"Collaboration"| SHVS
subgraph "Hub Internals (Patent 1, 4, 8, 10, 16, 17, 22)"
Orchestrator["Orchestrator<br>(IES Lifecycle)"] --> Resource_Alloc["Resource Allocator"]
Policy_Engine["Policy Engine"] --> DTMS_Config["DTMS Config"]
MSM_Int["MSM Interface"] --> Log_Aggregator["Log Aggregator"]
AuthN["AuthN"] & AuthZ["AuthZ"] --> MFA["MFA (P23)"]
SIZCF_Int["SIZCF Interface"] --> Zone_Mgmt["Zone Manager"]
end
end
subgraph "Modular IES Clusters (Patents 1, 2, 7, 8, 9, 10, 12)"
IES_Clusters["IES Clusters"] -->|"Secure Comm (P2, 3, 5)"| Multi_Channel_Network
IES_Clusters -->|"Resource Borrowing (P9)"| Resource_Borrowing
IES_Clusters -->|"AI Resource Alloc (P10)"| AI_Resource_Alloc
IES_Clusters -->|"Dynamic Partitioning (P1)"| Dynamic_Partitioning
IES_Clusters -->|"Anomaly Detection (P7)"| Anomaly_Detection
subgraph "IES Instance (Patents 1, 2, 7, 8, 9, 10, 12, 24)"
IES["IES"] --> Secure_Kernel["Secure Kernel"]
Secure_Kernel --> MMU["MMU"]
MMU --> Memory["Physically Segmented Memory"]
Secure_Kernel --> OS["Secure OS"]
OS --> App["Application"]
App -.-|"Data Access"| HESE_DAR["HESE-DAR (P24)"]
IES --> HW_Noise_Gen["Hardware Noise Generator"]
IES -.-> Chiplet_Fabric["Chiplet Fabric (P12)"]
end
subgraph "Local Security Mesh (P2)"
Local_MSM["Local MSM"] --> Anomaly_Detector["Anomaly Detector"]
end
end
subgraph "Multi-Channel Network (Patents 3, 5)"
Multi_Channel_Network -->|"Quantum-Resistant Encryption (P5)"| QR_Comm_GW
Multi_Channel_Network ---->|"Firewall (P3)"| Firewall
end
subgraph "DTMS (Patents 4, 16)"
DTMS -->|"Trust Evaluation"| Trust_DB
end
subgraph "SHVS (Patents 17, 18)"
SHVS -->|"Collaboration Contexts"| Collab_Mgmt["Collaboration Management"]
end
subgraph "External Systems/Zones (P22)"
External["External Systems"]
SIZCF["SIZCF"] -->|"Secure Communication"| QR_Comm_GW
SIZCF -.- External
end
subgraph "Decentralized Ledger (P13, 15, 17)"
Ledger["Decentralized Ledger"]
Hub -.- Ledger
IES_Clusters -.- Ledger
end
subgraph "AESDS (Patent 16)"
AESDS -->|"Software Updates"| IES_Clusters
end
subgraph "3D Microstructure (P14, 17)"
Microstructure["3D Microstructure"] -.- Ledger
Microstructure -.- AESDS
end
subgraph "Secure Data Enclaves (P20)"
SDE["Secure Data Enclaves"] -.- IES_Clusters
SDE -.- SHVS
end
subgraph "Federated Learning (P19)"
FL["Federated Learning"] -.- IES_Clusters
FL -.- SDE
end
%% Key connections between groups
Hub --- IES_Clusters
Hub --- MSM
IES_Clusters --- MSM
IES_Clusters --- Multi_Channel_Network
Multi_Channel_Network --- SIZCF
Hub --- SIZCF
DTMS --- IES_Clusters
DTMS --- SHVS
SHVS --- SIZCF
end
%% Node styling
style Hub fill:#f9f,stroke:#333
style IES_Clusters fill:#ccf,stroke:#888
style MSM fill:#ccf,stroke:#888
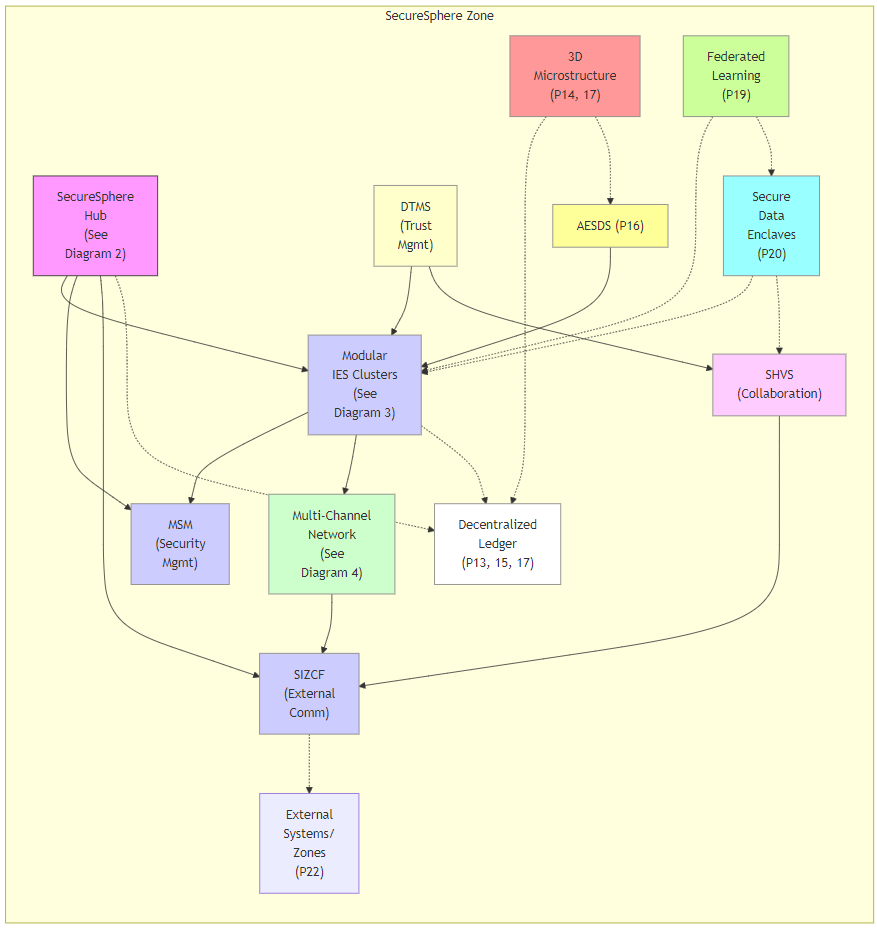
graph TD
subgraph "ASKA Zone"
direction TB
Hub["ASKA<br>Hub<br>(See<br>Diagram 2)"]
IES["Modular<br>IES Clusters<br>(See<br>Diagram 3)"]
MSM["MSM<br>(Security<br>Mgmt)"]
Network["Multi-Channel<br>Network<br>(See<br>Diagram 4)"]
DTMS["DTMS<br>(Trust<br>Mgmt)"]
SHVS["SHVS<br>(Collaboration)"]
SIZCF["SIZCF<br>(External<br>Comm)"]
External["External<br>Systems/<br>Zones<br>(P22)"]
Ledger["Decentralized<br>Ledger<br>(P13, 15, 17)"]
AESDS["AESDS (P16)"]
Microstructure["3D<br>Microstructure<br>(P14, 17)"]
SDE["Secure<br>Data<br>Enclaves<br>(P20)"]
FL["Federated<br>Learning<br>(P19)"]
Hub --- IES
Hub --- MSM
IES --- MSM
IES --- Network
Network --- SIZCF
Hub --- SIZCF
DTMS --- IES
DTMS --- SHVS
SHVS --- SIZCF
Hub -.- Ledger
IES -.- Ledger
AESDS --> IES
Microstructure -.- Ledger
Microstructure -.- AESDS
SDE -.- IES
SDE -.- SHVS
FL -.- IES
FL -.- SDE
SIZCF -.- External
end
style Hub fill:#f9f,stroke:#333,stroke-width:1px
style IES fill:#ccf,stroke:#888,stroke-width:1px
style MSM fill:#ccf,stroke:#888,stroke-width:1px
style Network fill:#cfc,stroke:#888,stroke-width:1px
style DTMS fill:#ffc,stroke:#888,stroke-width:1px
style SHVS fill:#fcf,stroke:#888,stroke-width:1px
style SIZCF fill:#ccf,stroke:#888,stroke-width:1px
style Ledger fill:#fff,stroke:#888,stroke-width:1px
style AESDS fill:#ff9,stroke:#888,stroke-width:1px
style Microstructure fill:#f99,stroke:#888,stroke-width:1px
style SDE fill:#9ff,stroke:#888,stroke-width:1px
style FL fill:#cf9,stroke:#888,stroke-width:1px
graph LR
subgraph "ASKA Hub"
Hub["ASKA Hub"] -->|"Orchestration & Mgmt"| IES_Clusters["IES Clusters"]
Hub -->|"Security Mgmt"| MSM["MSM"]
Hub ---->|"Trust Mgmt"| DTMS["DTMS"]
Hub ---->|"Collaboration"| SHVS["SHVS"]
subgraph "Hub Internals (Patent 1, 4, 8, 10, 16, 17, 22)"
Orchestrator["Orchestrator<br>(IES Lifecycle)"] --> Resource_Alloc["Resource Allocator"]
Policy_Engine["Policy Engine"] --> DTMS_Config["DTMS Config"]
MSM_Int["MSM Interface"] --> Log_Aggregator["Log Aggregator"]
AuthN["AuthN"] & AuthZ["AuthZ"] --> MFA["MFA (P23)"]
SIZCF_Int["SIZCF Interface"] --> Zone_Mgmt["Zone Manager"]
end
end
style Hub fill:#f9f,stroke:#333
graph LR
subgraph "Modular IES Clusters"
IES_Clusters["IES Clusters"] -->|"Secure Comm (P2, 3, 5)"| Multi_Channel_Network["Multi-Channel Network"]
IES_Clusters -->|"Resource Borrowing (P9)"| Resource_Borrowing
IES_Clusters -->|"AI Resource Alloc (P10)"| AI_Resource_Alloc
IES_Clusters -->|"Dynamic Partitioning (P1)"| Dynamic_Partitioning
IES_Clusters -->|"Anomaly Detection (P7)"| Anomaly_Detection
subgraph "IES Instance (Patents 1, 2, 7, 8, 9, 10, 12, 24)"
IES["IES"] --> Secure_Kernel["Secure Kernel"]
Secure_Kernel --> MMU["MMU"]
MMU --> Memory["Physically Segmented Memory"]
Secure_Kernel --> OS["Secure OS"]
OS --> App["Application"]
App -.-|"Data Access"| HESE_DAR["HESE-DAR (P24)"]
IES --> HW_Noise_Gen["Hardware Noise Generator"]
IES -.-> Chiplet_Fabric["Chiplet Fabric (P12)"]
end
subgraph "Local Security Mesh (P2)"
Local_MSM["Local MSM"] --> Anomaly_Detector["Anomaly Detector"]
end
end
style IES_Clusters fill:#ccf,stroke:#888
graph LR
subgraph "Multi-Channel Network"
Multi_Channel_Network -->|"Quantum-Resistant Encryption (P5)"| QR_Comm_GW["QR Comm GW"]
Multi_Channel_Network ---->|"Firewall (P3)"| Firewall
end
Diagram 1a through 1e Description: ASKA Architecture Overview
This diagram provides a comprehensive, high-level overview of the ASKA architecture, incorporating details from all 24 patents. It's designed for technical audiences, offering a clear understanding of the system's components, their functions, and interactions to achieve robust security. The hierarchical structure and grouping enhance readability and comprehension.
ASKA Zone (Patents 17, 18): This top-level subgraph encapsulates a single ASKA deployment or zone. Patent 17 (MDATS) contributes to the zone's audit capabilities, while Patent 18 (SHVS) introduces the concept of hierarchical zones for scalable and controlled collaboration.
Key Connections and Relationships:
The connections between components illustrate the flow of data, control signals, and dependencies. For example, the Hub manages the IES clusters, the IES clusters communicate through the Multi-Channel Network, and the DTMS informs security decisions across multiple components. The Decentralized Ledger, AESDS, and 3D Microstructure System provide overarching security, software update, and audit capabilities, respectively. Secure Data Enclaves and Federated Learning are integrated for secure data processing and analysis across the IES instances.
Diagram 1f: Full Integration
graph LR
subgraph "ASKA Instance"
direction LR
subgraph "ASKA Hub"
direction LR
AESDS["AESDS (AI-Driven Software Updates)"] --> STN["STN (Sovereign Trust Network)"]
AESDS --> DTG["DTG (Dynamic Trust Gateway)"]
AESDS --> IESCluster
IAMA["IAMA (Legacy System Monitoring)"] --> STN
DTMS["DTMS (Dynamic Trust Management)"] --> STN
DTMS --> DTG
DTMS --> IESCluster
PolicyEngine[Policy Engine] --> All
ResourceMgr[Resource Manager] --> IESCluster
ChannelMgr[Channel Manager] --> MultiChannelNetwork
UIIntegration[Secure UI Integration] --> SecureUI[Secure UI Kernel]
GovernanceAI[Governance AI] --> DTMS
MicrostructureInterface[3D Microstructure Interface] --> DLT
subgraph Key Management System
KeyGen[Key Generation] --> KeyStorage["Secure Key Storage (HESE-DAR)"]
KeyStorage --> IESCluster
%%KeyUsage[Key Usage Monitoring] --> Key Management System
Revocation[Key Revocation] --> KeyStorage
end
end
subgraph "IES Cluster (P1)"
direction LR
IES1[IES Instance 1] --> Apps1[Applications]
IES2[IES Instance 2] --> Apps2[Applications]
IESn[IES Instance N] --> Appsn[Applications]
IES1 -.- HESE_DAR["HESE-DAR (Data at Rest Encryption)"]
IES2 -.- HESE_DAR
IESn -.- HESE_DAR
IES1 -.- ZKEE["ZKEE (Secure Computation)"]
IES2 -.- ZKEE
IESn -.- ZKEE
IES1 --> LocalMSM1[Local MSM]
IES2 --> LocalMSM2[Local MSM]
IESn --> LocalMSMn[Local MSM]
LocalMSM1 --> MSM["Master Security Mesh (MSM)"]
LocalMSM2 --> MSM
LocalMSMn --> MSM
subgraph "Chiplet Fabric (P12)"
Chiplet1[Chiplet 1]
Chiplet2[Chiplet 2]
Chipletn[Chiplet N]
end
IES1 -.- Chiplet1
IES2 -.- Chiplet2
IESn -.- Chipletn
end
SecureUI --> IESCluster
subgraph "Multi-Channel Network (P3)"
direction LR
ATN["Authenticated Trust Network (ATN)"] --> DTG
DTG --> STN
Firewall --> ExternalSystems[External Systems/Zones]
QuantumComm["Quantum-Resistant Gateway (P5)"] --> ExternalSystems
SIZCF["SIZCF (Inter-Zone Collaboration)"] --> ExternalSystems
subgraph Channels
Channel1[Secure Channel 1]
Channel2[Secure Channel 2]
ChannelN[Secure Channel N]
end
DTG --> Channels
Channels --> Firewall
end
%%DLT["Decentralized Ledger (DLT)"] --> ASKA Hub
MDATS["MDATS (Multi-Dimensional Audit Trail)"] --> DLT
IESCluster --> MultiChannelNetwork
STN --> External_HighTrust[External High-Trust Environments]
%%MSM --> ASKA Hub
end
LegacySystems[Legacy Systems] --> IAMA
%%External_HighTrust --> Key Management System
style DLT fill:#f9f,stroke:#333,stroke-width:2px
style STN fill:#ccf,stroke:#333,stroke-width:2px
style HESE_DAR fill:#ccf,stroke:#333,stroke-width:2px
Description for Diagram 1f: Full Integration
graph TD
subgraph "ASKA Hub"
Orchestrator["Orchestrator<br>(IES Lifecycle Management)"] --> |Request| Resource_Allocator["Resource Allocator (P10)"]
Resource_Allocator -- "Resource Allocation" --> IES_Provisioning["IES Provisioning"]
IES_Provisioning --> |New IES Request| DTMS["DTMS (P4)"]
DTMS -- "Trust Establishment" --> IES_Deployment["IES Deployment<br>(Secure Boot - P1)"]
IES_Deployment --> IES_Pool["IES Pool (Active Instances)"]
IES_Pool --> |Scaling Request| Orchestrator
IES_Pool --> |Termination Request| Orchestrator
Orchestrator --> |Decommission| IES_Termination["IES Termination"]
IES_Termination --> Resource_Allocator
AESDS["AESDS (P16)"] -.-> |Software Provisioning| IES_Deployment
MSM["MSM (P2)"] -.-> |Security Monitoring| IES_Pool
Policy_Engine["Policy Engine (P4,16)"] --> |Policies| IES_Provisioning
Policy_Engine --> |Policies| IES_Deployment
end
subgraph "IES Instance Details"
IES["New IES Instance"]
subgraph "Hardware"
CPU["CPU"]
Memory["Memory"]
IO["I/O"]
Network["Network"]
end
subgraph "Software"
Kernel["Secure Kernel (P1)"]
OS["Secure OS (P1)"]
Apps["Applications"]
Kernel --> OS --> Apps
end
end
IES_Deployment --> IES
style Orchestrator fill:#ccf,stroke:#888,stroke-width:2px
graph TD
subgraph "ASKA Hub"
Orchestrator["Orchestrator<br>(IES Lifecycle Management)"] --> |Request| Resource_Allocator["Resource Allocator (P10)"]
Resource_Allocator -- "Resource Allocation" --> IES_Provisioning["IES Provisioning"]
IES_Provisioning --> |New IES Request| DTMS["DTMS (P4)"]
DTMS -- "Trust Establishment" --> IES_Deployment["IES Deployment<br>(Secure Boot - P1)"]
IES_Deployment --> IES_Pool["IES Pool (Active Instances)"]
IES_Pool --> |Scaling Request| Orchestrator
IES_Pool --> |Termination Request| Orchestrator
Orchestrator --> |Decommission| IES_Termination["IES Termination"]
IES_Termination --> Resource_Allocator
AESDS["AESDS (P16)"] -.-> |Software Provisioning| IES_Deployment
MSM["MSM (P2)"] -.-> |Security Monitoring| IES_Pool
Policy_Engine["Policy Engine (P4,16)"] --> |Policies| IES_Provisioning
Policy_Engine --> |Policies| IES_Deployment
end
style Orchestrator fill:#ccf,stroke:#888,stroke-width:2px
graph
subgraph "IES Instance Details"
IES["New IES Instance (Deployed from Hub)"]
subgraph "Hardware"
CPU["CPU"]
Memory["Memory"]
IO["I/O"]
Network["Network"]
end
subgraph "Software"
Kernel["Secure Kernel (P1)"]
OS["Secure OS (P1)"]
Apps["Applications"]
Kernel --> OS --> Apps
end
end
Diagram 2a and 2b Description: IES Lifecycle Management within ASKA Hub
This diagram details the lifecycle of an IES instance within the ASKA Hub, focusing on the Orchestrator's role and its interaction with other components. The process is visualized as a flow, starting with the initial request and ending with termination.
Components and Interactions:
Key Features Highlighted:
graph TD
subgraph "ASKA Zone"
direction LR
subgraph "IES Cluster (Patent 1)"
IES1["IES 1"] --> NIC1["NIC 1<br>(Capability-Aware)"]
IES2["IES 2"] --> NIC2["NIC 2<br>(Capability-Aware)"]
IESN["... IES N"] --> NICN["NIC N<br>(Capability-Aware)"]
end
subgraph "Multi-Channel Network (Patent 3)"
NIC1 --> |Hop Field/Capability Verification| Channel1["Secure Channel 1<br>(e.g., High Trust)"]
NIC2 --> |Hop Field/Capability Verification| Channel1
NIC1 --> |Hop Field/Capability Verification| Channel2["Secure Channel 2<br>(e.g., Medium Trust)"]
NIC2 --> |Hop Field/Capability Verification| Channel2
NICN --> |Hop Field/Capability Verification| Channel3["Secure Channel 3<br>(e.g., Legacy/External)"]
Channel1 --> Firewall["Out-of-Band Firewall<br>(Policy Enforcement)"]
Channel2 --> Firewall
Channel3 --> Firewall
Firewall --> |Policy Enforcement, Routing|Channel_Manager["Channel Manager<br>(Dynamic Routing & Access Control)"]
Channel_Manager --> Channel1
Channel_Manager --> Channel2
Channel_Manager --> Channel3
end
subgraph "External Connections"
External["External Systems/Zones<br>(QR Gateway - P5, SIZCF - P22)"]
Legacy["Legacy Systems"]
Channel1 --> External
Channel2 --> External
Channel3 --> Legacy
end
subgraph "ASKA Hub"
direction LR
Hub["ASKA<br>Hub"] --> DTMS["DTMS<br>(P4)"]
Hub --> MSM["MSM<br>(P2)"]
DTMS --> |Trust<br>Policies|Channel_Manager
MSM --> |Threat<br>Intelligence|Channel_Manager
end
IES_Cluster --- |Inter-IES Communication P2| Multi_Channel_Network
end
style Channel_Manager fill:#ccf,stroke:#888
style Firewall fill:#aaf,stroke:#666
graph TD
subgraph "ASKA Zone"
subgraph "IES Cluster (Patent 1)"
IES1["IES 1"] --> NIC1["NIC 1<br>(Capability-Aware)"]
IES2["IES 2"] --> NIC2["NIC 2<br>(Capability-Aware)"]
IESN["... IES N"] --> NICN["NIC N<br>(Capability-Aware)"]
end
subgraph "Multi Channel Network (Patent 3)"
NIC1 --> |Hop Field/Capability Verification| Channel1["Secure Channel 1<br>(e.g., High Trust)"]
NIC2 --> |Hop Field/Capability Verification| Channel1
NIC1 --> |Hop Field/Capability Verification| Channel2["Secure Channel 2<br>(e.g., Medium Trust)"]
NIC2 --> |Hop Field/Capability Verification| Channel2
NICN --> |Hop Field/Capability Verification| Channel3["Secure Channel 3<br>(e.g., Legacy/External)"]
Channel1 --> Firewall["Out-of-Band Firewall<br>(Policy Enforcement)"]
Channel2 --> Firewall
Channel3 --> Firewall
Firewall --> |Policy Enforcement, Routing|Channel_Manager["Channel Manager<br>(Dynamic Routing & Access Control)"]
Channel_Manager --> Channel1
Channel_Manager --> Channel2
Channel_Manager --> Channel3
end
subgraph "External Connections"
External["External Systems/Zones<br>(QR Gateway - P5, SIZCF - P22)"]
Legacy["Legacy Systems"]
Channel1 --> External
Channel2 --> External
Channel3 --> Legacy
end
end
style Channel_Manager fill:#ccf,stroke:#888
style Firewall fill:#aaf,stroke:#666
graph TD
subgraph "ASKA Zone"
subgraph "Multi Channel Network (Patent 3)"
Channel_Manager["Channel Manager<br>(Dynamic Routing & Access Control)"]
end
subgraph "ASKA Hub"
direction LR
Hub["ASKA<br>Hub"] --> DTMS["DTMS<br>(P4)"]
Hub --> MSM["MSM<br>(P2)"]
DTMS --> |Trust<br>Policies|Channel_Manager
MSM --> |Threat<br>Intelligence|Channel_Manager
end
subgraph "IES Cluster (Patent 1)"
IES["IES Cluster"]
end
IES --- |Inter-IES Communication P2| Multi_Channel_Network
end
style Channel_Manager fill:#ccf,stroke:#888
Diagram 3a and 3b Description: Communication Flow within the Multi-Channel Network
This diagram illustrates the flow of secure communication within ASKA's Multi-Channel Network, highlighting the roles of different components and the integration of several key patents.
Components and Interactions:
Key Features Highlighted:
graph TD
subgraph "IES Instance (Patent 1)"
Application["Application"] --> |Data Request Read/Write| IOMMU["IOMMU (P9) <br> (Request Routing)"]
IOMMU -- Secure Channel (P2,3) --> HESE_DAR_Controller
end
subgraph "HESE-DAR (Patent 24)"
direction LR
HESE_DAR_Controller["HESE-DAR Controller"] --> |Access Request| Access_Control["Access Control (P4, 13)"]
Access_Control -- Authorized --> Key_Manager["Key Manager (P5)"]
Access_Control -- Unauthorized --> Application["Access Denied"]
Key_Manager --> |Decryption Key| Crypto_Engine["Crypto Engine (P5, P7)"]
HESE_DAR_Controller --> |Data Request| Crypto_Engine
Crypto_Engine --> |Plaintext Data| HESE_DAR_Controller
Crypto_Engine --> |Encrypted Data| Secure_Storage["Secure Storage (Encrypted)"]
Secure_Storage --> |Encrypted Data| Crypto_Engine
Key_Manager -.- |Key Generation/Audit| Microstructure_Gen["3D Microstructure Generator (P14, 17)"]
Microstructure_Gen --> Microstructure["3D Microstructure"]
MSM["MSM (P2)"] -.-> |Security Monitoring|HESE_DAR_Controller
DTMS["DTMS (P4)"]-.-> |Trust Policies|Access_Control
end
HESE_DAR_Controller -- Secure Channel (P2,3) --> IOMMU
IOMMU --> |Data Read/Write| Application
style HESE_DAR_Controller fill:#ccf,stroke:#888,stroke-width:2px
style Access_Control fill:#aaf,stroke:#666
style Key_Manager fill:#aaf,stroke:#666
style Crypto_Engine fill:#aaf,stroke:#666
Diagram 4 Description: HESE-DAR Detailed Data Flow
This diagram provides a detailed view of the data flow within and around the HESE-DAR (Hardware-Enforced Secure Encrypted Enclave for Data at Rest), illustrating how data is securely accessed, encrypted, decrypted, and protected.
Components and Interactions:
Key Features and Benefits:
graph TD
subgraph "ASKA Zone A"
IES_A["IES Instance A"] --> Hub_A["ASKA Hub A"]
Hub_A --> Ledger_A["Decentralized Ledger A"]
Hub_A --> |Collaboration Request| SIZCF_A["SIZCF Interface A"]
end
subgraph "ASKA Zone B"
IES_B["IES Instance B"] --> Hub_B["ASKA Hub B"]
Hub_B --> Ledger_B["Decentralized Ledger B"]
Hub_B --> |Collaboration Request| SIZCF_B["SIZCF Interface B"]
end
subgraph "SIZCF (Patent 22)"
SIZCF_A -- "Zone Discovery & Authentication (P18, P4)" --> SIZCF_B
SIZCF_A --> Trust_Assessment["Trust Assessment (P4)"]
SIZCF_B --> Trust_Assessment
Trust_Assessment -- "Trust Established" --> Secure_Channel["Secure Communication Channel (P3, P5)"]
subgraph "Data Exchange & Synchronization"
Secure_Channel --> Data_Sanitization["Data Sanitization & Transformation (P20)"]
Data_Sanitization --> Data_Exchange["Secure Data Exchange (P20)"]
Data_Exchange --> Ledger_Sync["Distributed Ledger Synchronization"]
Ledger_Sync --> Ledger_A
Ledger_Sync --> Ledger_B
end
end
subgraph "External Systems/Zones"
External["External System/Zone"]
SIZCF -.- External
end
style Secure_Channel fill:#ccf,stroke:#888
style Data_Sanitization fill:#aaf,stroke:#666
style Data_Exchange fill:#aaf,stroke:#666
style Ledger_Sync fill:#aaf,stroke:#666
Diagram 5 Description: ASKA Zone Interaction via SIZCF
This diagram illustrates how ASKA Zones interact and collaborate securely using the Secure Inter-Zone Collaboration Framework (SIZCF), as described in Patent 22. It focuses on the key steps involved in establishing a secure collaboration context between zones.
Components and Interactions:
Key Features Highlighted:
graph TD
subgraph "AESDS AI Engine - The Genesis Forge (Patent 16)"
direction LR
subgraph "Nebula of Knowledge (Knowledge Base)"
KB((("Best Practices"))) --> |Continuous Learning|AI_Engine
Libraries((("Libraries"))) --> KB
Design_Patterns((("Design Patterns"))) --> KB
Compliance((("Compliance & Regulations"))) --> KB
Threat_Models((("Threat Models"))) --> KB
end
subgraph "AI Engine Core"
AI_Engine["AI Engine<br>(Code Generation & Refinement)"] --> |Candidate Software<br>OS & User Apps| Code_Generator["Code Generator"]
AI_Engine --> |Automated Testing &<br>Validation Requests| Sandbox_Controller
end
subgraph "Dynamic Input Streams"
Performance_Metrics["Performance Metrics<br>(Resource Usage, Execution Time)"] --> |Optimization & Adaptation| AI_Engine
User_Feedback["User Feedback<br>(Usability, Feature Requests)"] --> |Feature Enhancement &<br>Personalization| AI_Engine
Threat_Intel["Threat Intelligence<br>(Vulnerabilities, Attack Patterns)"] --> |Security Hardening &<br>Proactive Defense| AI_Engine
end
subgraph "ASKA Integration (Subtle Energy Fields)"
MSM["MSM (P2)"] -.-> |Security Monitoring & Analysis| AI_Engine
DTMS["DTMS (P4)"] -.-> |Trust Policies & Access Control| AI_Engine
HESE_DAR["HESE-DAR (P24)"] -.-> |Secure Storage & Data Protection| AI_Engine
end
subgraph "IES Sandbox Environment"
Sandbox_Controller["Sandbox Controller<br>(IES Management)"] --> |Deploy & Manage| IES_Sandbox["IES Sandbox<br>(Isolated Testing Environment - P1)"]
IES_Sandbox --> |Test Results| AI_Engine
end
subgraph "Code Crystallization & Deployment (Quantum Entanglement)"
Code_Generator --> |Validated Code| Software_Repository["Secure Software Repository"]
Software_Repository -- |Quantum Entanglement| --> IES_Deployment["IES Deployment (P1)"] & User_App_Deployment["User App Deployment"]
end
end
style AI_Engine fill:#ccf,stroke:#888,stroke-width:2px
linkStyle 1,2,3,4,5,12,13 stroke:#f9f,stroke-width:2px,color:#333
graph TD
subgraph "AESDS AI Engine#8209;The Genesis Forge (Patent 16)"
direction LR
subgraph "Nebula of Knowledge (Knowledge Base)"
KB((("Best<br>Practices"))) --> |Continuous<br>Learning|AI_Engine
Libraries((("Libraries"))) --> KB
Design_Patterns((("Design<br>Patterns"))) --> KB
Compliance((("Compliance<br>&<br>Regulations"))) --> KB
Threat_Models((("Threat Models"))) --> KB
end
subgraph "AI Engine Core"
AI_Engine["AI Engine<br>(Code Generation<br>& Refinement)"] --> |Candidate Software<br>OS & User Apps| Code_Generator["Code<br>Generator"]
AI_Engine --> |Automated Testing &<br>Validation Requests| Sandbox_Controller["Sandbox<br>Controller"]
end
end
style AI_Engine fill:#ccf,stroke:#888,stroke-width:2px
linkStyle 1,2,3,4,5 stroke:#f9f,stroke-width:2px,color:#333
graph
subgraph "AESDS AI Engine#8209;The Genesis Forge (Patent 16)"
AI_Engine["AI Engine"]
subgraph "Dynamic Input Streams"
Performance_Metrics["Performance Metrics<br>(Resource Usage, Execution Time)"] --> |Optimization & Adaptation| AI_Engine
User_Feedback["User Feedback<br>(Usability, Feature Requests)"] --> |Feature Enhancement &<br>Personalization| AI_Engine
Threat_Intel["Threat Intelligence<br>(Vulnerabilities, Attack Patterns)"] --> |Security Hardening &<br>Proactive Defense| AI_Engine
end
subgraph "ASKA Integration"
MSM["MSM (P2)"] -.-> |Security Monitoring & Analysis| AI_Engine
DTMS["DTMS (P4)"] -.-> |Trust Policies & Access Control| AI_Engine
HESE_DAR["HESE-DAR (P24)"] -.-> |Secure Storage & Data Protection| AI_Engine
end
end
style AI_Engine fill:#ccf,stroke:#888,stroke-width:2px
linkStyle 0,1,2 stroke:#f9f,stroke-width:2px,color:#333
graph
subgraph "AESDS AI Engine#8209;The Genesis Forge (Patent 16)"
AI_Engine["AI Engine"]
Code_Generator["Code Generator"]
subgraph "IES Sandbox Environment"
Sandbox_Controller["Sandbox Controller<br>(IES Management)"] --> |Deploy & Manage| IES_Sandbox["IES Sandbox<br>(Isolated Testing Environment - P1)"]
IES_Sandbox --> |Test Results| AI_Engine
end
subgraph "Code Crystallization & Deployment"
Code_Generator --> |Validated Code| Software_Repository["Secure Software Repository"]
Software_Repository -- Code Provenance Assurance --> IES_Deployment["IES Deployment (P1)"] & User_App_Deployment["User App Deployment"]
end
end
style AI_Engine fill:#ccf,stroke:#888,stroke-width:2px
linkStyle 2,3 stroke:#f9f,stroke-width:2px,color:#333
Diagram 6a through 6c Description: AESDS AI Engine - The Genesis Forge (Patent 16)
This diagram visualizes the AI Engine within the Automated Evolutionary Software Development System (AESDS), focusing on its role in generating and refining software for both OS components and user applications at a global scale
Components and Interactions:
Diagram 6 AESDS AI Engine SUB-DIAGRAMS TODO:
graph TD
subgraph "IES Instance (Patent 1)"
IES["IES Instance"]
SCI["Secure Chiplet Interface (P12)"]
IES --> SCI
end
subgraph "Chiplet Lifecycle (Patent 12)"
direction LR
Insertion["Chiplet Insertion"] --> Authentication["Authentication<br>(Cryptographic Verification)"]
Authentication -- Verified --> Resource_Allocation["Resource Allocation<br>(Dynamic)"]
Resource_Allocation --> Workload_Assignment["Workload Assignment<br>(Task Distribution)"]
Workload_Assignment --> Operation["Chiplet Operation<br>(Within IES)"]
Operation --> Removal["Chiplet Removal<br>(Secure Disconnection)"]
subgraph "Chiplet Orchestration Module (P12)"
COM["Chiplet Orchestration Module"]
COM --> Resource_Allocation
COM --> Workload_Assignment
COM --> Removal
end
Chiplet["Chiplet"] --> Insertion
Removal --> Chiplet_Pool["Chiplet Pool"]
end
SCI ----> Chiplet
SCI ----> COM
Operation ----> IES
style COM fill:#ccf,stroke:#888
style SCI fill:#aaf,stroke:#666
Diagram 7: Chiplet Integration Lifecycle
This diagram details the lifecycle of a chiplet within the ASKA architecture, from insertion and authentication to resource allocation, workload assignment, and eventual removal. The diagram aims to clearly and accurately represent the process, highlighting the security and efficiency of the Modular Chiplet Architecture (Patent 12).
Stages:
Diagram 7 Description:
This diagram visually represents the chiplet lifecycle within a ASKA IES instance, highlighting the key interactions and security considerations of Patent 12.
graph TD
subgraph "Voting Terminal (Patents 11, 13)"
direction LR
Voter["Voter"] --> Authentication["Authentication<br>(Hardware Token, Biometrics,<br>3D Microstructure (P14))"]
Authentication -- Authenticated --> Secure_UI["Secure UI (P11) <br> Vote Casting"]
Secure_UI --> Encrypted_Vote["Encrypted Vote (P5)"]
end
subgraph "ASKA Zone (Patents 13, 15)"
Encrypted_Vote --> |Secure Channel P3| DLT["Decentralized Ledger (P13, P15)<br>Secure Tallying<br>(Distributed Consensus)"]
DLT --> Vote_Record["Vote Record"]
DLT -.- Microstructure_Gen["Microstructure Generator (P14)"]
Microstructure_Gen --> Microstructures["3D Microstructures<br>(Audit Trail)"]
end
subgraph "Auditing & Verification (Patents 14, 15, 17)"
Auditor["Auditor"] --> Vote_Record
Auditor --> Microstructures
Vote_Record & Microstructures --> Verification["Verification & Analysis<br>(MDATS - P17)"]
Verification --> Audit_Report["Audit Report"]
end
style DLT fill:#ccf,stroke:#888
style Microstructure_Gen fill:#aaf,stroke:#666
Diagram 8: Decentralized Governance Process (Voting)
This diagram illustrates the decentralized governance process within ASKA, focusing on a citizen voting scenario. The diagram emphazies the security, transparency, and auditability of the system, highlighting the integration of Patents 13, 14, 15, and elements of 5 and 11.
Process Stages:
Diagram Description:
This diagram illustrates the secure and transparent decentralized governance process in ASKA, focusing on a voting scenario. It highlights the key components and interactions, emphasizing security and auditability.
graph TD
subgraph "AESDS Lifecycle (Patent 16)"
AI_Engine["AI Engine<br>(Code Generation)"] --> Testing["Testing<br>(IES Sandbox - P1)"]
Testing -- Test Results --> Validation["Validation<br>(Security, Performance)"]
Validation -- Validated --> Governance["Governance<br>(Decentralized - P13, P15)"]
Governance -- Approved --> Deployment["Deployment<br>(Secure Distribution)"]
Deployment --> Monitoring["Monitoring<br>(Performance, Security - P2)"]
Monitoring --> Feedback["Feedback Collection<br>(User, System)"]
Feedback --> AI_Engine
subgraph "AI Engine Details"
KB["Knowledge Base"] --> AI_Engine
Threat_Intel["Threat Intelligence"] --> AI_Engine
end
subgraph "Deployment Details"
Deployment --> IES["IES Instances (P1)"]
Deployment --> User_Apps["User Applications"]
end
subgraph "Audit Trail (P14, P17)"
Microstructure["3D Microstructure"]
Governance --> Microstructure
Deployment --> Microstructure
end
style AI_Engine fill:#ccf,stroke:#888
style Testing fill:#aaf,stroke:#666
style Validation fill:#aaf,stroke:#666
style Governance fill:#aaf,stroke:#666
style Deployment fill:#aaf,stroke:#666
style Monitoring fill:#aaf,stroke:#666
end
Diagram 9 Description: Automated Evolutionary Software Development System (AESDS) Lifecycle
This diagram visualizes the lifecycle of software development within the Automated Evolutionary Software Development System (AESDS) as described in Patent 16. The diagram presents the process as a continuous loop, highlighting the AI-driven nature of each stage and the integration with key ASKA components.
Components and Interactions:
Key Features Highlighted:
graph TD
subgraph "ASKA Zone"
direction LR
subgraph "IES Cluster (Patent 1)"
IES1["IES 1"] --> NIC1["NIC 1<br>(Capability-Aware)"]
IES2["IES 2"] --> NIC2["NIC 2<br>(Capability-Aware)"]
IESN["... IES N"] --> NICN["NIC N<br>(Capability-Aware)"]
end
subgraph "Multi-Channel Network (Patent 3) - The Quantum Highway"
NIC1 --> |Hop Field/Capability<br>Verification P2/P25| Channel1["Secure Channel 1<br>(High Trust)"]
NIC2 --> |Hop Field/Capability<br>Verification P2/P25|Channel1
NIC1 --> |Hop Field/Capability<br>Verification P2/P25|Channel2["Secure Channel 2<br>(Medium Trust)"]
NIC2 --> |Hop Field/Capability<br>Verification P2/P25|Channel2
NICN --> |Hop Field/Capability<br>Verification P2/P25|Channel3["Secure Channel 3<br>(External/Legacy)"]
Channel1 --> Checkpoint1["Firewall Checkpoint<br>(Packet Inspection)"]
Channel2 --> Checkpoint2["Firewall Checkpoint<br>(Packet Inspection)"]
Channel3 --> Checkpoint3["Firewall Checkpoint<br>(Packet Inspection)"]
Checkpoint1 --> Channel_Manager
Checkpoint2 --> Channel_Manager
Checkpoint3 --> Channel_Manager
Channel_Manager["Channel Manager<br>(Dynamic Routing & Access Control)"] --> |Rerouting Signals| Channel1
Channel_Manager --> |Rerouting Signals| Channel2
Channel_Manager --> |Rerouting Signals| Channel3
Channel1 -.- |QR Gateway P5| External["External Systems/Zones (P5, P22)"]
Channel2 -.- |QR Gateway P5| External
Channel3 --> Legacy["Legacy Systems"]
subgraph "Out-of-Band Firewall (P3)"
Firewall["Firewall"] --> Checkpoint1
Firewall --> Checkpoint2
Firewall --> Checkpoint3
end
end
subgraph "ASKA Hub"
Hub["ASKA<br>Hub"] --> DTMS["DTMS<br>(P4)"]
Hub --> MSM["MSM<br>(P2)"]
DTMS --> |Trust<br>Policies|Channel_Manager
MSM --> |Threat<br>Intelligence|Channel_Manager
end
end
style Channel_Manager fill:#ccf,stroke:#888
style Firewall fill:#aaf,stroke:#666
graph TD
subgraph "ASKA Zone"
direction LR
subgraph "IES Cluster (Patent 1)"
IES1["IES 1"] --> NIC1["NIC 1<br>(Capability-Aware)"]
IES2["IES 2"] --> NIC2["NIC 2<br>(Capability-Aware)"]
IESN["... IES N"] --> NICN["NIC N<br>(Capability-Aware)"]
end
subgraph "Multi-Channel Network (Patent 3) - The Quantum Highway"
NIC1 --> |Hop Field/Capability<br>Verification P2/P25| Channel1["Secure Channel 1<br>(High Trust)"]
NIC2 --> |Hop Field/Capability<br>Verification P2/P25|Channel1
NIC1 --> |Hop Field/Capability<br>Verification P2/P25|Channel2["Secure Channel 2<br>(Medium Trust)"]
NIC2 --> |Hop Field/Capability<br>Verification P2/P25|Channel2
NICN --> |Hop Field/Capability<br>Verification P2/P25|Channel3["Secure Channel 3<br>(External/Legacy)"]
Channel_Manager["Channel Manager<br>(Dynamic Routing & Access Control)"]
end
subgraph "ASKA Hub"
Hub["ASKA<br>Hub"] --> DTMS["DTMS<br>(P4)"]
Hub --> MSM["MSM<br>(P2)"]
DTMS --> |Trust<br>Policies|Channel_Manager
MSM --> |Threat<br>Intelligence|Channel_Manager
end
end
style Channel_Manager fill:#ccf,stroke:#888
graph
subgraph "ASKA Zone"
subgraph "Multi-Channel Network (Patent 3) - The Quantum Highway"
Channel1["Secure Channel 1<br>(High Trust)"]
Channel2["Secure Channel 2<br>(Medium Trust)"]
Channel3["Secure Channel 3<br>(External/Legacy)"]
Channel1 --> Checkpoint1["Firewall Checkpoint<br>(Packet Inspection)"]
Channel2 --> Checkpoint2["Firewall Checkpoint<br>(Packet Inspection)"]
Channel3 --> Checkpoint3["Firewall Checkpoint<br>(Packet Inspection)"]
Checkpoint1 --> Channel_Manager
Checkpoint2 --> Channel_Manager
Checkpoint3 --> Channel_Manager
Channel_Manager["Channel Manager<br>(Dynamic Routing & Access Control)"] --> |Rerouting Signals| Channel1
Channel_Manager --> |Rerouting Signals| Channel2
Channel_Manager --> |Rerouting Signals| Channel3
Channel1 -.- |QR Gateway P5| External["External Systems/Zones (P5, P22)"]
Channel2 -.- |QR Gateway P5| External
Channel3 --> Legacy["Legacy Systems"]
subgraph "Out-of-Band Firewall (P3)"
Firewall["Firewall"] --> Checkpoint1
Firewall --> Checkpoint2
Firewall --> Checkpoint3
end
end
end
style Channel_Manager fill:#ccf,stroke:#888
style Firewall fill:#aaf,stroke:#666
graph TD
subgraph "ASKA Zone"
direction LR
subgraph "Multi-Channel Network (Patent 3) - The Quantum Highway"
NIC1 --> |Hop Field/Capability<br>Verification P2/P25| Channel1["Secure Channel 1<br>(High Trust)"]
NIC2 --> |Hop Field/Capability<br>Verification P2/P25|Channel1
NIC1 --> |Hop Field/Capability<br>Verification P2/P25|Channel2["Secure Channel 2<br>(Medium Trust)"]
NIC2 --> |Hop Field/Capability<br>Verification P2/P25|Channel2
NICN --> |Hop Field/Capability<br>Verification P2/P25|Channel3["Secure Channel 3<br>(External/Legacy)"]
Channel1 --> Checkpoint1["Firewall Checkpoint<br>(Packet Inspection)"]
Channel2 --> Checkpoint2["Firewall Checkpoint<br>(Packet Inspection)"]
Channel3 --> Checkpoint3["Firewall Checkpoint<br>(Packet Inspection)"]
Checkpoint1 --> Channel_Manager
Checkpoint2 --> Channel_Manager
Checkpoint3 --> Channel_Manager
Channel_Manager["Channel Manager<br>(Dynamic Routing & Access Control)"] --> |Rerouting Signals| Channel1
Channel_Manager --> |Rerouting Signals| Channel2
Channel_Manager --> |Rerouting Signals| Channel3
Channel1 -.- |QR Gateway P5| External["External Systems/Zones (P5, P22)"]
Channel2 -.- |QR Gateway P5| External
Channel3 --> Legacy["Legacy Systems"]
end
end
style Channel_Manager fill:#ccf,stroke:#888
Diagram 10 Description: Adaptive Multi-Channel Network - The Quantum Highway
This diagram visualizes the Adaptive Multi-Channel Network (Patent 3) within ASKA. It emphasizes dynamic routing, security checkpoints, and secure connections to external systems.
Components and Interactions:
Key Features and Enhancements:
graph TD
subgraph "ASKA Zone"
IES["IES Instance<br>(Trust Level: <span id='trustValue'>Medium</span>)"] --> |Access Request| Gate["Access Gate"]
Resource["Protected Resource<br>(Sensitivity: <span id='sensitivityValue'>High</span>)"] -.-> Gate
subgraph "DTMS (Patent 4) - Trust Hub"
direction LR
Trust_Level["Trust Level<br>(Past Behavior, Security Posture)"] --> Trust_Calculator["Trust Calculator"]
Monitoring_Data["Real-Time Monitoring Data"] --> Trust_Calculator
Threat_Intel["Threat Intelligence<br>(<span id='threatLevel'>Moderate</span>)"] --> Trust_Calculator
Policies["Applicable Policies<br>(Access Control Rules)"] --> Trust_Calculator
Trust_Calculator -- "Trust Score" --> Consensus_Engine["Distributed Consensus Engine"]
Consensus_Engine -- "Access Decision" --> Gate
end
Trust_Level -.-> IES
Resource -.-> Policies
Threat_Intel -.-> Resource
end
style Gate fill:#ccf,stroke:#888
style Trust_Calculator fill:#aaf,stroke:#666
style Consensus_Engine fill:#aaf,stroke:#666
linkStyle 0,7 stroke:#f9f,stroke-width:2px,color:#333
Diagram 11 Description: Dynamic Trust Management System (DTMS) in Action
This diagram visualizes the real-time operation of the Dynamic Trust Management System (DTMS) within ASKA, as described in Patent 4. It focuses on the process of evaluating an IES instance's access request to a protected resource, highlighting the dynamic nature of trust calculation and the factors influencing access decisions.
Components and Interactions:
Data Flow:
graph TD
subgraph "Secure Data Enclave (Patent 20) The Sanctuary"
subgraph "Outer Walls (ASKA Zone)"
IES_A["IES Instance A<br>(Data Source A)"] --> |Authenticated Channel P2, P3, P5| Ingestion_A["Secure Data<br>Ingestion"]
IES_B["IES Instance B<br>(Data Source B)"] --> |Authenticated Channel P2, P3, P5| Ingestion_B["Secure Data<br>Ingestion"]
DTMS["DTMS (P4)"] --> |Trust Policies| Access_Control
end
subgraph "Inner Sanctum (Secure Data Enclave)"
Ingestion_A --> |Data Validation & Sanitization| Enclave_A["Enclave A<br>(Data Processing)"]
Ingestion_B --> |Data Validation & Sanitization| Enclave_B["Enclave B<br>(Data Processing)"]
subgraph "Privacy-Preserving Analysis"
Enclave_A & Enclave_B --> |Encrypted Data| MPC_Engine["MPC Engine (P19)"]
MPC_Engine --> |Differentially Private Results| DP_Engine["Differential Privacy Engine"]
DP_Engine --> |Homomorphically Encrypted Results| HE_Engine["Homomorphic Encryption Engine"]
end
HE_Engine --> |Analysis Results| Sanitized_Output["Sanitized Output"]
end
subgraph "Secure Output Channel"
Sanitized_Output --> |Authenticated Channel P2, P3, P5| External["External Systems/Zones<br>(e.g., SIZCF - P22)"]
end
Access_Control["Access Control"] --> Enclave_A & Enclave_B
Ledger["Decentralized Ledger (P13, P15)"] -.-> |Audit Trail| Inner_Sanctum
end
style Enclave_A fill:#ccf,stroke:#888
style Enclave_B fill:#ccf,stroke:#888
style MPC_Engine fill:#aaf,stroke:#666
style DP_Engine fill:#aaf,stroke:#666
style HE_Engine fill:#aaf,stroke:#666
Diagram 12 Description: Data Enclave - The Sanctuary
This diagram provides a detailed technical illustration of the Secure Data Enclave system (Patent 20), emphasizing its security features, privacy-preserving mechanisms, and integration within ASKA.
Components and Interactions:
Key Features and Enhancements:
graph TD
subgraph "ASKA Hub"
direction LR
subgraph "Hub Display"
IES_Status["IES Status (P1)"] --> Operator1["Operator"]
Network_Traffic["Network Traffic (P3)"] --> Operator1
Security_Alerts["Security Alerts (P2, P7)"] --> Operator2["Operator"]
Resource_Utilization["Resource Utilization (P9, P10)"] --> Operator2
end
subgraph "Hub Modules"
Orchestrator["Orchestrator (P1, P10)"] --> IES_Status & Resource_Utilization
Policy_Engine["Policy Engine (P4, P16)"] --> Security_Alerts & Access_Control["Access Control"]
MSM_Interface["MSM Interface (P2)"] --> Security_Alerts
DTMS_Interface["DTMS Interface (P4)"] --> IES_Status & Access_Control
SIZCF_Interface["SIZCF Interface (P22)"] --> Network_Traffic & Collab_Status["Collaboration Status (P18)"]
AESDS_Interface["AESDS Interface (P16)"] --> Software_Updates["Software Updates"] & IES_Status
Microstructure_Interface["Microstructure Interface (P14, P17)"] --> Audit_Logs["Audit Logs"]
Ledger_Interface["Decentralized Ledger Interface (P13, P15)"] --> Audit_Logs & Security_Alerts & Software_Updates
end
subgraph "External Connections"
External_Zones["External Zones (P22)"] -.- SIZCF_Interface
IES_Clusters["IES Clusters (P1)"] -.- Orchestrator
MSM["MSM (P2)"] -.- MSM_Interface
DTMS["DTMS (P4)"] -.- DTMS_Interface
AESDS["AESDS (P16)"] -.- AESDS_Interface
Microstructure_System["3D Microstructure System (P14, P17)"] -.- Microstructure_Interface
Ledger["Decentralized Ledger (P13, P15)"] -.- Ledger_Interface
end
Operator1 -.- Hub_Control_Panel["Hub Control Panel"] -.- Operator2
Hub_Control_Panel --> Orchestrator
Hub_Control_Panel --> Policy_Engine
Hub_Control_Panel --> SIZCF_Interface
Hub_Control_Panel --> AESDS_Interface
end
style Operator1 fill:#ccf,stroke:#888
style Operator2 fill:#ccf,stroke:#888
style Hub_Control_Panel fill:#aaf,stroke:#666
graph TD
subgraph "ASKA Hub"
Hub_Control_Panel["Hub Control Panel"]
Display["Hub Display<br>(See Diagram 2)"]
Modules["Hub Modules<br>(See Diagram 3)"]
External["External Connections<br>(See Diagram 4)"]
Hub_Control_Panel --> Modules
Modules --> Display
External -.- Modules
end
style Hub_Control_Panel fill:#aaf,stroke:#666
graph TD
subgraph "Hub Display"
IES_Status["IES Status (P1)"] --> Operator1["Operator"]
Network_Traffic["Network Traffic (P3)"] --> Operator1
Security_Alerts["Security Alerts (P2, P7)"] --> Operator2["Operator"]
Resource_Utilization["Resource Utilization (P9, P10)"] --> Operator2
end
style Operator1 fill:#ccf,stroke:#888
style Operator2 fill:#ccf,stroke:#888
graph
subgraph "Hub Modules"
Orchestrator["Orchestrator (P1, P10)"] --> IES_Status & Resource_Utilization
Policy_Engine["Policy Engine (P4, P16)"] --> Security_Alerts & Access_Control["Access Control"]
MSM_Interface["MSM Interface (P2)"] --> Security_Alerts
DTMS_Interface["DTMS Interface (P4)"] --> IES_Status & Access_Control
SIZCF_Interface["SIZCF Interface (P22)"] --> Network_Traffic & Collab_Status["Collaboration Status (P18)"]
AESDS_Interface["AESDS Interface (P16)"] --> Software_Updates["Software Updates"] & IES_Status
Microstructure_Interface["Microstructure Interface (P14, P17)"] --> Audit_Logs["Audit Logs"]
Ledger_Interface["Decentralized Ledger Interface (P13, P15)"] --> Audit_Logs & Security_Alerts & Software_Updates
end
graph
subgraph "External Connections"
External_Zones["External Zones (P22)"] -.- SIZCF_Interface
IES_Clusters["IES Clusters (P1)"] -.- Orchestrator
MSM["MSM (P2)"] -.- MSM_Interface
DTMS["DTMS (P4)"] -.- DTMS_Interface
AESDS["AESDS (P16)"] -.- AESDS_Interface
Microstructure_System["3D Microstructure System (P14, P17)"] -.- Microstructure_Interface
Ledger["Decentralized Ledger (P13, P15)"] -.- Ledger_Interface
end
Diagram 13a through 13d Description: Hub - The Command Center
This diagram visualizes the ASKA Hub as a futuristic command center, showcasing its central role in managing and monitoring the ASKA Zone. The diagram emphasizes the Hub's internal modules, their interactions, and the flow of information between the Hub and other ASKA components.
Components and Interactions:
Key Features and Enhancements:
graph LR
subgraph ASKA
direction LR
subgraph Control_Plane["Control Plane"]
Hub_CP["ASKA Hub<br>Control Plane"] --> DTMS["DTMS (P4)"]
Hub_CP --> ZM["Zone Manager<br>(P18, P22)"]
Hub_CP --> CM["Capability Manager<br>(P2, P25)"]
Hub_CP --> RM["Resource Manager<br>(P9, P10)"]
Hub_CP --> AESDS_CP["AESDS Control Plane<br>(P16)"]
Hub_CP --> MSM["MSM (P2, P7)"]
DTMS -.- IES_CP["IES Control Plane (P1)"]
ZM -.- IES_CP
CM -.- IES_CP
RM -.- IES_CP
AESDS_CP -.- IES_CP
MSM -.- IES_CP
IES_CP --> NIC_CP["Network Interface<br>Control Plane (P3)"]
NIC_CP --> Network["Secure Multi-Channel<br>Network (P3, P5)"]
Network --> External["External Systems/Zones (P22)"]
end
subgraph Data_Plane["Data Plane"]
IES_DP["IES Data Plane (P1, P24)"] --> NIC_DP["Network Interface<br>Data Plane (P2, P3)"]
IES_DP -.-> Chiplet["Chiplet Fabric (P12)"]
NIC_DP --> Network
NIC_DP --> IOMMU["IOMMU (P9)"]
IOMMU --> Peripherals["Peripherals"]
subgraph "IES Internals"
App["Application"] --> SecOS["Secure OS (P1)"]
SecOS --> SecKernel["Secure Kernel (P1)"]
SecKernel --> MMU["MMU (P8)"]
MMU --> Memory["Protected Memory (P8)"]
App --> HESE_DAR["HESE-DAR (P24)"]
end
IES_DP --> IES_Internals
end
Control_Plane -.-|Coordination & Control| Data_Plane
subgraph UI_Plane["Secure UI Plane (P11)"]
UIK["Secure UI Kernel"] --> UIDB["Multi-region<br>Display Buffer"]
UIDB --> Display["Display"]
IES_DP --> UIK
end
subgraph Ledger["Decentralized Ledger<br>(P13, P15, P17, P21)"]
end
Control_Plane -.- |Auditing & Logging|Ledger
Data_Plane -.- |Auditing & Logging|Ledger
AESDS_CP -.- Ledger
end
graph LR
subgraph ASKA
subgraph Control_Plane["Control Plane"]
Network["Secure Multi-Channel<br>Network (P3, P5)"]
end
subgraph Data_Plane["Data Plane"]
IES_DP["IES Data Plane (P1, P24)"]
end
Control_Plane -.-|Coordination & Control| Data_Plane
subgraph UI_Plane["Secure UI Plane (P11)"]
UIK["Secure UI Kernel"] --> UIDB["Multi-region<br>Display Buffer"]
UIDB --> Display["Display"]
IES_DP --> UIK
end
subgraph Ledger["Decentralized Ledger<br>(P13, P15, P17, P21)"]
end
Control_Plane -.- |Auditing & Logging|Ledger
Data_Plane -.- |Auditing & Logging|Ledger
end
graph LR
subgraph Control_Plane["Control Plane"]
Hub_CP["ASKA Hub<br>Control Plane"] --> DTMS["DTMS (P4)"]
Hub_CP --> ZM["Zone Manager<br>(P18, P22)"]
Hub_CP --> CM["Capability Manager<br>(P2, P25)"]
Hub_CP --> RM["Resource Manager<br>(P9, P10)"]
Hub_CP --> AESDS_CP["AESDS Control Plane<br>(P16)"]
Hub_CP --> MSM["MSM (P2, P7)"]
DTMS -.- IES_CP["IES Control Plane (P1)"]
ZM -.- IES_CP
CM -.- IES_CP
RM -.- IES_CP
AESDS_CP -.- IES_CP
MSM -.- IES_CP
IES_CP --> NIC_CP["Network Interface<br>Control Plane (P3)"]
NIC_CP --> Network["Secure Multi-Channel<br>Network (P3, P5)"]
Network --> External["External Systems/Zones (P22)"]
end
graph
subgraph Data_Plane["Data Plane"]
IES_DP["IES Data Plane (P1, P24)"] --> NIC_DP["Network Interface<br>Data Plane (P2, P3)"]
IES_DP -.-> Chiplet["Chiplet Fabric (P12)"]
NIC_DP --> Network
NIC_DP --> IOMMU["IOMMU (P9)"]
IOMMU --> Peripherals["Peripherals"]
subgraph "IES Internals"
App["Application"] --> SecOS["Secure OS (P1)"]
SecOS --> SecKernel["Secure Kernel (P1)"]
SecKernel --> MMU["MMU (P8)"]
MMU --> Memory["Protected Memory (P8)"]
App --> HESE_DAR["HESE-DAR (P24)"]
end
IES_DP --> IES_Internals
end
Diagram 14 Description for Control / Data Planes:
This diagram provides a high-level overview of ASKA's architecture, separating the control plane and data plane elements and illustrating their interaction. It highlights how core ASKA components participate in both planes and how they coordinate.
graph LR
subgraph ASKA
direction LR
subgraph "IES Cluster (P1)"
IES1["IES 1"]
IES2["... IES N"]
IES1 -.- InterIESComm
IES2 -.- InterIESComm
subgraph "IES 1 Internals"
CPU["CPU"]
Memory["Memory<br>(P8)"]
IO["I/O"]
NIC["Network<br> Interface"]
subgraph "Child IES (P1)"
ChildIES1["Child IES 1<br>(Zone 1)"]
ChildIES2["...Child IES n<br>(Zone n)"]
ChildIES1 -.- DRCI
ChildIES2 -.- DRCI
subgraph "Zone 1 Details"
MiniTRC1["Mini-TRC"] --> DTMS_local["Local DTMS (P4)"]
RM_local["Local<br>Resource Mgr<br>(P9, P10)"]
ChildIES1 --> MiniTRC1
ChildIES1 --> RM_local
end
end
CPU --> ChildIES1 & ChildIES2
Memory --> ChildIES1 & ChildIES2
IO --> ChildIES1 & ChildIES2
NIC --> ChildIES1 & ChildIES2
subgraph "IES <br> Security Components"
LSM_1["Local Security<br>Mesh (P2)"]
AD["Anomaly Detection (P7)"]
LSM_1 --> AD
LSM_1 -.- Secure_Boot["Secure Boot (P1, P13)"]
end
ChildIES1 & ChildIES2 --> IES_Security_Components
NIC --> Firewall_local["Local Firewall (P3)"]
end
IES1 --> Hardware_Isolation["Hardware Isolation"] --> IES_1_Internals
end
subgraph "Inter-IES Communication (P2)"
InterIESComm["Inter-IES Comm"]
InterIESComm --> DataDiode["Data Diode"]
InterIESComm --> CEP("Capability-Enhanced PCFS<br>(Hop Fields & Capabilities)")
InterIESComm --> CM["Capability Manager"]
end
subgraph "ASKA Hub"
Hub["ASKA Hub"]
subgraph "Hub Components"
DTMS["DTMS (P4)"]
ZM["Zone Manager (P18, P22)"]
CM
RM_hub["Resource Mgr (P9,P10)"]
AESDS["AESDS (P16)"]
MSM["MSM (P2,P7)"]
end
Hub --> Hub_Components
end
subgraph UI_Plane["Secure UI Plane (P11)"]
UIK["Secure UI Kernel<br>(Zone n+1)"] --> UIDB["Multi-region<br>Display Buffer"]
UIDB --> Display["Display"]
IES1 -.-> UIK
end
subgraph "Multi-Channel Network (P3, P5)"
Network["Multi-Channel Network"]
Network --> QR["Quantum-Resistant Gateway (P5)"]
Network --> Firewall["Global<br>Firewall (P3)"]
end
subgraph "External Systems/Zones (P22)"
External["External Systems"]
External -.- SIZCF["SIZCF"] --> QR
end
IES_Cluster ----> Network
IES_Cluster ----> InterIESComm ----> Network
Hub -.- Network
Hub -.- DTMS
InterIESComm ----> Firewall
subgraph "Decentralized Ledger (P13, P15, 17, 21)"
Ledger["Decentralized Ledger"]
end
IES_Cluster -.- Ledger
Hub -.- Ledger
subgraph "Data Services (P6, P19, P20)"
FL["Federated Learning (P19)"]
SDE["Secure Data Enclaves (P20)"]
ZKEE["Zero-Knowledge<br>Execution (P6)"]
IES1 -.- FL
IES1 -.- SDE
IES1 -.- ZKEE
end
SDE -.- SHVS["Secure Hypervisor (P18)"]
SHVS -.- Collab["Collaboration Contexts (P18)"]
ZM ----> Collab
subgraph "3D Microstructure System (P14, P17)"
MS["Microstructure System"] --> Ledger
end
IES1 -.-> SecureBoot["Secure Boot (P1)"]
Secure_Boot --> Attestation["Attestation<br>Service (P13)"]
IES1 --> Attestation
MFA["MFA (P23)"] --> UIK
subgraph "Automated Software<br> Deployment (P16,P21)"
AESDS[Automated Software Deployment] -->IES_Cluster
end
end
graph
subgraph ASKA
IES1["IES 1 .. N"]
InterIESComm["Inter-IES Comm"]
Hub["ASKA Hub"]
UIK["Secure UI Kernel<br>(Zone n+1)"] --> UIDB["Multi-region<br>Display Buffer"]
UIDB --> Display["Display"]
IES1 -.-> UIK
Network["Multi-Channel Network"]
Network --> QR["Quantum-Resistant Gateway (P5)"]
Network --> Firewall["Global<br>Firewall (P3)"]
External["External Systems"]
External -.- SIZCF["SIZCF"] --> QR
IES_Cluster ----> Network
IES_Cluster ----> InterIESComm ----> Network
Hub -.- Network
Hub -.- DTMS["DTMS (P4)"]
InterIESComm ----> Firewall
Ledger["Decentralized Ledger"]
IES_Cluster -.- Ledger
Hub -.- Ledger
ZM["Zone Manager (P18, P22)"]
AESDS["AESDS (P16)"]
SDE["Secure Data Enclaves (P20)"]
SDE -.- SHVS["Secure Hypervisor (P18)"]
SHVS -.- Collab["Collaboration Contexts (P18)"]
ZM ----> Collab
MS["Microstructure System"] --> Ledger
IES1 -.-> SecureBoot["Secure Boot (P1)"]
SecureBoot --> Attestation["Attestation<br>Service (P13)"]
IES1 --> Attestation
MFA["MFA (P23)"] --> UIK
AESDS[Automated Software Deployment]
AESDS --> |Software Updates| IES_Clusters
end
Diagram 15 Description:
This diagram provides a detailed overview of ASKA, highlighting detailed integration throughout the system's architecture. It visually represents the connections between specific ASKA components and patents.
1. ASKA (Top-Level): Encompasses all components and illustrates the system's modular and layered security approach.
2. IES Cluster (Patent 1): Illustrates the core of ASKA's isolation technology.
3. ASKA Hub:
4. Multi-Channel Network (P3, P5):
5. External Systems/Zones (P22): Represents external entities and zones that interact with ASKA through the SIZCF (Secure Inter-Zone Collaboration Framework).
6. Decentralized Ledger (P13, 15, 17, 21): Securely stores TRCs, audit logs, and other critical information, illustrating ASKA's decentralized governance and auditing approach.
7. Data Services (P6, P19, P20):
8. Other Components and Connections:
High-Level Components (Main Diagram):
Sections (Sub-Diagrams):
Discussion of Diagrams 16a through 16f:
Diagrams 16a through 16f illustrate the intricate integration of ASKA's automated software development (AESDS - Patent 16) with its trust and security mechanisms, specifically the Sovereign Trust Network (STN - Patent 27) and Dynamic Trust Gateway (DTG - Patent 28). This write-up provides a detailed technical analysis of this subsystem, highlighting the key innovations, components, interactions, and security benefits.
Core Innovation:
The core innovation lies in the synergistic combination of automated software evolution with hardware-enforced isolation, dynamic trust management, and proactive security. The AESDS doesn't just generate and deploy updates; it does so within a highly secure and adaptive framework. The integration with the STN and DTG extends these automated processes to the most sensitive parts of ASKA, ensuring the continuous evolution and hardening of the entire system. Furthermore, the IAMA module within AESDS adds a layer of proactive defense by leveraging insights from legacy system monitoring to strengthen ASKA against potential threats.
Component Breakdown and Interactions:
High-Level Integration Points:
Security Benefits:
graph LR
subgraph "ASKA System (Patents 16, 27, 28)"
subgraph "Automated Evolutionary Software Development (AESDS) (Patent 16)"
AESDS["AESDS"] --> |Software Updates| STN["Sovereign Trust Network (P27)"]
AESDS --> |Software Updates| DTG["Dynamic Trust Gateway (P28)"]
AESDS --> |Software Updates| ASKA_Core["ASKA Core"]
IAMA["IAMA Module (P16, C9)"] --> |Hostile Intelligence Analysis| AESDS
Legacy_System["Legacy System<br>(Connected to STN)"] --> |Monitored Activity| IAMA
end
subgraph "Sovereign Trust Network (STN) (Patent 27)"
STN --> |Secure Key Management| Key_Manager["Key Manager"]
STN --> |Secure Authentication| Auth_Manager["Authentication Manager"]
STN --> |Isolated Data Plane| NonSwitched_Firewall["Non-Switched Firewall Segment"]
NonSwitched_Firewall --> |Data & Control Path|DTG
STN -.- |Minimal Control Plane Interface| ASKA_Control_Plane["ASKA Control Plane"]
Iso_Security_Stack["Isomorphic Security Stack"] --> STN
IAMA --> |Security Updates| Iso_Security_Stack
end
subgraph "Dynamic Trust Gateway (DTG) (P28)"
DTG --> |Dynamic Channel Management| MultiPath_Manager["Multi-Path<br> Manager"]
DTG --> |Capability Management| Cap_Manager["Capability<br> Manager"]
DTG --> |Access Control & Sanitization| AuthZ["Authorization<br> Engine"]
MultiPath_Manager --> |Secure Paths| ATN["Authenticated Trust Network (P3)"]
ATN --> ASKA_Core
STN --- |Data & Control<br>Path| DTG
Metrics_Engine["Metrics Engine"] --> |Performance & Trust Metrics| DTG
DTMS["Dynamic Trust Management System (P4)"] --> |Trust Levels| DTG
AESDS -.-> |Policy Adjustments| DTG
AESDS -.-> |Adaptive Security| DTG
end
subgraph "ASKA Core"
IES_Cluster["IES Clusters (P1)"]
ASKA_Core --> IES_Cluster
ASKA_Core --> |Secure UI| UI_Kernel["Secure UI Kernel (P11)"]
end
Decentralized_Ledger["Decentralized Ledger<br>(Patents 13, 15)"] -.-> AESDS
Decentralized_Ledger -.-> STN
Decentralized_Ledger -.-> DTG
MDATS["Multi-Dimensional Audit Trail (P17)"] -.-> AESDS
end
Diagram 16a Description:
This main diagram provides a high-level overview of the integration between the Automated Evolutionary Software Development System (AESDS - Patent 16), the Sovereign Trust Network (STN - Patent 27), and the Dynamic Trust Gateway (DTG - Patent 28) within ASKA. It highlights the key interactions and dependencies between these components, emphasizing the secure software development and deployment process, the isolated nature of the STN, and the adaptive security mechanisms employed by the DTG.
ASKA System (Patents 16, 27, 28): This top-level subgraph encapsulates the integrated system.
Automated Evolutionary Software Development (AESDS) (Patent 16):
Sovereign Trust Network (STN) (Patent 27):
Dynamic Trust Gateway (DTG) (Patent 28):
ASKA Core:
Overarching Components:
Key Features Highlighted:
---
config:
theme: default
themeVariables:
fontSize: 38px
-- background: "#333333"
-- primaryColor: "#333333"
---
graph LR
subgraph "AESDS (Patent 16)"
direction LR
subgraph "AI Engine (Enhanced)"
KB["Knowledge Base<br>(ASKA Architecture,<br>Best Practices, Libraries)"] --> AIEngine
Isomorphic_Model["Isomorphic Model<br>(Legacy System Representation)"] --> AIEngine
Metrics["Performance Metrics<br>(STN, DTG, IES)"] --> AIEngine
User_Feedback["User Feedback"] --> AIEngine
Threat_Intel["Threat Intelligence"] --> AIEngine
AIEngine["AI Engine<br>(Code Generation & Refinement)"] --> |Software Candidates| Code_Generator["Code Generator<br>(STN, DTG, Core)"]
Code_Generator -.- |Vulnerability<br>Data| IAMA
subgraph "IAMA (Isomorphic Architecture<br>Monitoring & Adaptation)"
Legacy_System["Legacy System<br>(Connected to STN)"] --> Data_Diode["Data Diode (P2)"]
Data_Diode --> Legacy_Monitor["Legacy System Monitor"]
Legacy_Monitor --> Isomorphic_Model
end
IAMA --> AIEngine
AIEngine --> IAMA
subgraph "Vulnerability Database"
Vuln_DB["Vulnerability Database<br>(STN-Specific,<br>DTG-Specific,<br>Core-Specific)"]
IAMA --> Vuln_DB
AIEngine --> Vuln_DB
end
end
subgraph "Specialized Code Generators"
Code_Generator --> STN_Code_Gen["STN Code Generator<br>(Kernel, OS, Drivers,<br>Security Modules)"]
Code_Generator --> DTG_Code_Gen["DTG Code Generator<br>(SCA, Capability Manager,<br>Authorization Engine)"]
Code_Generator --> Core_Code_Gen["Core Code Generator<br>(IES, Hub, UI)"]
end
STN_Code_Gen --> |STN Updates| Sandbox_STN["STN Sandbox<br>(Isolated Testing)"]
DTG_Code_Gen --> |DTG Updates| Sandbox_DTG["DTG Sandbox<br>(Isolated Testing)"]
Core_Code_Gen --> |Core Updates| Sandbox_Core["Core Sandbox<br>(Isolated Testing)"]
subgraph "ASKA Interface"
SSI["ASKA Interface<br>(Patents 2,3,4)"]
SSI --> STN["Sovereign Trust Network (P27)"]
SSI --> DTG["Dynamic Trust Gateway (P28)"]
end
subgraph "Parallel Sandboxes"
Sandbox_STN["STN Sandbox"] --> SSI
Sandbox_DTG["DTG Sandbox"] --> SSI
subgraph "STN Sandbox Internals"
STN_Iso_MSM["Isomorphic MSM"]
STN_Iso_DTMS["Isomorphic DTMS"]
STN_Key_Mgr["Key Manager"]
STN_Auth_Mgr["Authentication<br>Manager"]
STN_Code_Gen --> STN_Iso_MSM & STN_Iso_DTMS & STN_Key_Mgr & STN_Auth_Mgr
end
Sandbox_STN --> STN_Sandbox_Internals
subgraph "DTG Sandbox Internals"
DTG_SCA["SCA"]
DTG_Cap_Mgr["Capability<br>Manager"]
DTG_AuthZ["AuthZ Engine"]
DTG_Code_Gen --> DTG_SCA & DTG_Cap_Mgr & DTG_AuthZ
end
Sandbox_DTG --> DTG_Sandbox_Internals
Sandbox_Core["Core Sandbox (Patent 1)"] --> SSI
subgraph "Core Sandbox Internals"
IES["IES Instance"]
Hub_Module["Hub Module"]
UI_Kernel["UI Kernel"]
Core_Code_Gen --> IES & Hub_Module & UI_Kernel
end
Sandbox_Core --> Core_Sandbox_Internals
end
AIEngine --> |Test Requests| Parallel_Sandboxes
Parallel_Sandboxes --> |Test Results, Metrics| AIEngine
end
style IAMA fill:#ccf,stroke:#888,stroke-width:2px
Diagram 16b Description: AESDS with IAMA Module (Patent 16, Claim 9)
This sub-diagram provides a detailed view of the AESDS (Patent 16), focusing on its integration with the STN (Patent 27) and DTG (Patent 28) for software updates and adaptive security. It expands upon the high-level representation in the main diagram, revealing the internal complexities of the AESDS and its specialized components for generating and deploying updates to these critical ASKA subsystems.
AESDS (Patent 16): This subgraph encompasses the enhanced AESDS.
AI Engine (Enhanced):
IAMA (Isomorphic Architecture Monitoring & Adaptation): This module analyzes the legacy system connected to the STN.
Vulnerability Database:
Specialized Code Generators:
Parallel Sandboxes: This section emphasizes the isolated testing environments for each type of update.
graph TD
subgraph "Sovereign Trust Network (STN) (Patent 27)"
subgraph "Dedicated Data Plane (Physically Isolated)"
Data_Input["Data Input<br>(From ASKA)"] --> NonSwitched_Firewall["Non-Switched Firewall Segment"]
NonSwitched_Firewall --> STN_Router["STN Router"]
STN_Router --> IES_Cluster["STN IES Cluster (P1)"]
IES_Cluster --> HESE_DAR["HESE-DAR (P24)"]
IES_Cluster -.- |"Secure Channel (P2, P3, P5)"| DTG["Dynamic Trust Gateway (P28)"]
subgraph "External High-Trust Communication"
Data_Diode["Data Diode (P2)"] --> QR_Gateway["Quantum-Resistant Gateway (P5)"]
QR_Gateway --> Dedicated_Channel["Dedicated Channel (P3)"]
Dedicated_Channel --> Ext_High_Trust["External High-Trust Environments"]
IES_Cluster ----> Data_Diode
end
end
subgraph "Minimal Control Plane Interface"
direction TB
Dedicated_Control_Channel["Dedicated Control Channel<br>(Authenticated & Encrypted)"] --> STN_Control_Plane["STN Control Plane"]
subgraph "Control Plane Modules"
direction TB
STN_Control_Plane --> Auth_Manager["Authentication Manager<br>(Passkeys, HW-Rooted Trust)"]
Auth_Manager -.-> MFA["MFA (P23)"]
STN_Control_Plane --> Resource_Mgr["Resource Mgr (P9, P10)"]
STN_Control_Plane --> IAMA_Interface["IAMA Interface (P16, C9)"]
IAMA_Interface --> AESDS["AESDS (P16)"]
ASKA_Control_Plane["ASKA Control Plane"] -.-> Dedicated_Control_Channel
end
end
subgraph "Isomorphic Security Stack"
Iso_MSM["Isomorphic MSM (P2)"]
Iso_DTMS["Isomorphic DTMS (P4)"]
Iso_Security_Modules["Isomorphic Security Modules"]
IAMA["IAMA Module (P16, C9)"] --> Iso_MSM
Iso_MSM --> Iso_DTMS
Iso_DTMS --> Iso_Security_Modules
Iso_Security_Modules --> IES_Cluster
Legacy_System["Legacy System"] --> Data_Diode_Monitor["Data Diode (P2)"]
Data_Diode_Monitor --> Legacy_Monitor["Legacy System Monitor"]
Legacy_Monitor --> IAMA
end
subgraph "Key Recovery System"
Sync_Nodes["Hierarchical Network of<br>Trusted Sync Nodes"]
Recovery_Controller["Recovery Controller"]
Key_Manager["Key Manager"]
Sync_Nodes --> Recovery_Controller
Recovery_Controller --> Key_Manager
Key_Manager --> HESE_DAR
Sync_Nodes -.- |"Authenticated Channel (P27)"| External_High_Trust
end
Dedicated_Data_Plane --- Minimal_Control_Plane_Interface
Minimal_Control_Plane_Interface --- Isomorphic_Security_Stack
Isomorphic_Security_Stack --- Key_Recovery_System
subgraph "Fully Segmented Pathway to Fed Multicloud"
direction TB
subgraph "ASKA Instance"
direction TB
ASKA["ASKA"] --> ASKA_Edge["ASKA Edge Network<br>(Last Mile)"]
style ASKA fill:#ccf,stroke:#888
end
ASKA_Edge --> Remote_Infra["Remote Infrastructure<br>(Dedicated Lines)"]
Remote_Infra --> Remote_Cloud["Remote Multicloud<br>(Secure Enclaves)"]
style Remote_Infra fill:#aaf,stroke:#666
style Remote_Cloud fill:#8f8,stroke:#444
end
Dedicated_Data_Plane --> Fully_Segmented_Pathway_to_Remote_Multicloud
end
style Dedicated_Data_Plane fill:#ccf,stroke:#888
style Isomorphic_Security_Stack fill:#aaf,stroke:#666
graph
subgraph "STN Module"
A1["Dedicated Data Plane (Physically Isolated)"] --> A2["Non-Switched Firewall Segment"]
A2 --> A3["STN Router"]
A3 --> A4["STN IES Cluster (P1)"]
A4 --> A5["HESE-DAR (P24)"]
B1["External High-Trust Communication"] --> B2["Data Diode (P2)"]
B2 --> B3["Quantum-Resistant Gateway (P5)"]
B3 --> B4["Dedicated Channel (P3)"]
B4 --> A4
C1["Minimal Control Plane Interface"] --> C2["Dedicated Control Channel (Auth & Encrypted)"]
C2 --> C3["Control Plane Modules"]
C3 --> C4["STN Control Modules: Auth Manager, Resource Manager, IAMA (P16, C9)"]
D1["Isomorphic Security Stack"] --> D2["Isomorphic MSM, DTMS (P4)"]
D2 --> D3["Security Modules"]
D3 --> A4
E1["Key Recovery System"] --> E2["Trusted Sync Nodes"]
E2 --> E3["Recovery Controller"]
E3 --> E4["Key Manager"]
E4 --> A5
end
style A1,A2,A3,A4,A5 fill:#F0F8FF,stroke:#000,stroke-width:1px
style B1,B2,B3,B4 fill:#E6E6FA,stroke:#000,stroke-width:1px
style C1,C2,C3,C4 fill:#FFE4E1,stroke:#000,stroke-width:1px
style D1,D2,D3 fill:#FAFAD2,stroke:#000,stroke-width:1px
style E1,E2,E3,E4 fill:#E0FFFF,stroke:#000,stroke-width:1px
flowchart TD
%% Simplified shared components
Shared["STN Overview Components"]:::shared -- Shared Connection --> A4
%% External-specific elements
A1["ASKA Input (External Data)"] --> A2["Non-Switched Firewall Segment"]
A2 --> A4["STN Router"]
A4 --> A5["IES Execution & Analysis"]
A5 --> A6["External High-Trust Comm"]
style Shared fill:#D3D3D3,stroke:#000,stroke-width:2px
style A1,A2,A4,A5,A6 fill:#FFDAB9,stroke:#000,stroke-width:1px
classDef shared fill:#F0F8FF,stroke:#000,stroke-width:1px
Diagram Description:
This sub-diagram details the external facing design of the Sovereign Trust Network (STN) as described in Patent 27, highlighting the isolated data plane, minimal control plane interface, isomorphic security stack, and the fully segmented pathway to the remote multicloud.
Sovereign Trust Network (STN) (Patent 27): This top-level subgraph encapsulates all STN components.
Dedicated Data Plane (Physically Isolated): Emphasizes the complete physical and logical separation of the STN's data plane.
Minimal Control Plane Interface: This subgraph details the STN's restricted control plane.
Isomorphic Security Stack: This section highlights the novel security architecture of the STN.
Key Recovery System:
Fully Segmented Pathway to Remote Multicloud: This crucial subgraph visually represents the complete physical and logical segmentation of the STN's data plane from the ASKA instance to the RemoteMulticloud.
graph LR
subgraph "Sovereign Trust Network (STN) Internals (Patent 27)"
subgraph "Dedicated Data Plane"
Data_Input["Encrypted Data Input<br>(from DTG)"] --> Firewall["STN Firewall<br>(Packet Filtering,<br>Integrity Checks)"]
Firewall --> Router["STN Router<br>(Secure Routing,<br>Path Validation)"]
Router --> IES_Cluster["IES Cluster (Patent 1)"]
subgraph "IES Instance (Example)"
IES["IES"] --> Secure_Kernel["Secure Kernel (P1)"]
Secure_Kernel --> MMU_C["MMU (P8)"]
MMU_C --> Encrypted_Memory["Encrypted Memory (P8)"]
Secure_Kernel --> Secure_OS["Secure OS (P1)"]
Secure_OS --> STN_App["STN Application<br>(Key Management,<br>Authentication)"]
STN_App -.-|"Key Operations"| HESE_DAR["HESE-DAR (P24)"]
IES --> RNG["Hardware RNG (P18)"]
end
IES_Cluster --> IES
HESE_DAR["HESE-DAR"] -->|"Encrypted Storage"| Secure_Storage["Secure Storage"]
IES_Cluster -.- |"Secure Channel (P2, P3, P5)"|DTG["Dynamic Trust Gateway (P28)"]
subgraph "External High-Trust Communication"
Data_Diode["Data Diode (P2)"] --> QR_Gateway["Quantum-Resistant Gateway (P5)"]
QR_Gateway --> Dedicated_Channel["Dedicated Channel (P3)"]
Dedicated_Channel --> Ext_High_Trust["External High-Trust Environments"]
IES_Cluster ----> Data_Diode
end
end
subgraph "Minimal Control Plane Interface"
Dedicated_Control_Channel["Dedicated Control Channel<br>(Authenticated & Encrypted)"] --> STN_Control_Plane
STN_Control_Plane["STN Control Plane"] --> Auth_Manager["Authentication Manager<br>(Passkeys, HW-Rooted Trust)"]
STN_Control_Plane --> Resource_Mgr["Resource Mgr (P9, P10)"]
STN_Control_Plane --> IAMA_Interface["IAMA Interface (P16, C9)"]
IAMA_Interface --> AESDS["AESDS (P16)"]
ASKA_Control_Plane["ASKA Control Plane"] -.-> Dedicated_Control_Channel
end
subgraph "Isomorphic Security Stack"
IAMA["IAMA Module (P16, C9)"] --> Iso_MSM["Isomorphic MSM (P2)"]
Legacy_System["Legacy System"] --> Data_Diode_Monitor["Data Diode (P2)"]
Data_Diode_Monitor --> Legacy_Monitor["Legacy System Monitor<br>(Behavior Analysis)"]
Legacy_Monitor --> IAMA
Iso_MSM --> Iso_DTMS["Isomorphic DTMS (P4)"]
subgraph "Isomorphic DTMS (P4)"
Iso_Trust_Calc["Trust Calculator"]
Iso_Policy_Engine["Policy Engine"]
Iso_Trust_DB["Trust Database"]
Iso_MSM --> Iso_Trust_Calc
Iso_Policy_Engine --> Iso_Trust_Calc
Iso_Trust_Calc --> Iso_Trust_DB
IAMA -.-> Iso_Policy_Engine
end
Iso_DTMS --> Iso_PEP["Policy Enforcement Point (PEP)"]
Iso_PEP --> IES_Cluster
end
subgraph "Key Recovery System"
Sync_Nodes["Hierarchical Network of<br>Trusted Sync Nodes"]
Recovery_Controller["Recovery Controller<br>(Multi-Factor Auth)"]
Key_Manager["Key Manager<br>(PQ Crypto - P5)"]
Sync_Nodes --> Recovery_Controller
Recovery_Controller --> Key_Manager
Key_Manager --> HESE_DAR
subgraph "MFA (P23)"
Biometrics["Biometrics"]
Hardware_Token["Hardware Token"]
Microstructure["3D Microstructure<br>(P14)"]
Biometrics --> Recovery_Controller
Hardware_Token --> Recovery_Controller
Microstructure --> Recovery_Controller
end
Sync_Nodes -.- |"Authenticated Channel (P27)"| External_High_Trust["External High-Trust<br>Environments"]
end
Dedicated_Data_Plane --- Minimal_Control_Plane_Interface
Minimal_Control_Plane_Interface --- Isomorphic_Security_Stack
Isomorphic_Security_Stack --- Key_Recovery_System
end
style Dedicated_Data_Plane fill:#ccf,stroke:#888
style Isomorphic_Security_Stack fill:#aaf,stroke:#666
flowchart TD
%% Simplified shared components
Shared["STN Overview Components"]:::shared -- Shared Connection --> A4
%% Internal-specific elements
A1["Encrypted Data Input from DTG"] --> A2["STN Firewall"]
A2 --> A3["Secure Kernel & OS"]
A3 --> A4["IES Secure Execution"]
A4 --> A5["Isomorphic MSM / DTMS Operations"]
A5 --> A6["Secure Storage (HESE-DAR)"]
style Shared fill:#D3D3D3,stroke:#000,stroke-width:2px
style A1,A2,A3,A4,A5,A6 fill:#87CEEB,stroke:#000,stroke-width:1px
classDef shared fill:#F0F8FF,stroke:#000,stroke-width:1px
Diagram Description:
This sub-diagram provides an in-depth view of the STN's internal workings. It expands on the "STN Externals" diagram by showing the internal structure of key components and their integration with other ASKA technologies.
Sovereign Trust Network (STN) Internals (Patent 27):
Dedicated Data Plane: This section emphasizes the complete isolation of the STN's data plane.
Minimal Control Plane Interface: This section shows the restricted control plane access to the STN. A dedicated, secure control channel is used, separate from the ASKA Control Plane. The diagram also details the internal control modules within the STN's control plane, including connections to Patents 9, 10, 16 (IAMA Interface), and 23 (MFA).
Isomorphic Security Stack: This section highlights the STN's isolated security infrastructure, which is a novel feature.
Key Recovery System:
TODO: split this diagram into separate, even more granular diagrams for specific components: Isomorphic DTMS, the Key Recovery System, and the IES instance internals.
graph
subgraph "Dynamic Trust Gateway (DTG) Internals (Patent 28)"
subgraph "Secure Communication Agent (SCA)"
ATN_Interface["ATN Interface<br>(Multi-Channel Network - Patent 3)"] --> Path_Manager["Multi-Path Manager<br>(Dynamic Path Selection,<br> Load Balancing)"]
Path_Manager --> Path1["Secure Path 1<br>(Quantum-Resistant - Patent 5)"]
Path_Manager --> PathN["... Secure Path N"]
Path1 --> STN_Interface["STN Interface"]
PathN --> STN_Interface
DTMS["DTMS (Patent 4)"] --> Path_Manager
AESDS_IAMA["AESDS IAMA<br>(Patent 16, Claim 9)"] -.-> Path_Manager
Path_Manager -->|"Path Status & Metrics"| Metrics_Engine
subgraph "Path 1 Details"
direction TB
Data_Diode_1["Data Diode (P2)"] --> Encryptor_1["Encryptor (P5)"]
Encryptor_1 --> MAC_1["MAC (P26)"]
MAC_1 --> TX_Queue_1["Transmission Queue"]
TX_Queue_1 --> Physical_Interface_1["Physical Network Interface (P3)"]
end
Path1 --> Path_1_Details
subgraph "Path N Details"
direction TB
Data_Diode_N["Data Diode (P2)"] --> Encryptor_N["Encryptor (P5)"]
Encryptor_N --> MAC_N["MAC (P26)"]
MAC_N --> TX_Queue_N["Transmission Queue"]
TX_Queue_N --> Physical_Interface_N["Physical Network Interface (P3)"]
end
PathN --> Path_N_Details
end
subgraph "Capability Manager"
Policy_Engine["Policy Engine (TRC-based)"] --> Capability_Gen["Capability Generator"]
Capability_Gen --> Capability_Store["Capability Store<br>(Hardware-backed)"]
Capability_Store -->|"Capabilities"| SCA
DTMS --> Capability_Gen
Metrics_Engine --> Capability_Gen
MPA["Multi-Path Capability<br>Aggregator"] --> Capability_Store
SCA -->|"Path Capabilities"| MPA
subgraph "Hardware Accelerated Capabilities"
Chiplet["Capability Manager Chiplet (P12)"] --> Capability_Store
end
end
subgraph "Data Handling & Security"
STN_Interface --> DPI["Deep Packet Inspection (DPI)<br>(Hardware Accelerated)"]
DPI --> Sanitizer["Data Sanitizer"]
Sanitizer --> AuthZ["Authorization Engine<br>(Capability-Based)"]
AuthZ -- Authorized --> Data_Handler["Data Handler"]
AuthZ -- Unauthorized --> Access_Denied["Access Denied"]
Data_Handler --> Formatter["Data Formatter/Serializer"]
Formatter --> STN["Sovereign Trust Network (Patent 27)"]
MSM["Master Security Mesh (Patent 2)"] --> DPI
end
subgraph "Decentralized Governance & Auditing"
Ledger["Decentralized Ledger<br>(Patents 13, 15)"]
DTG_Controller["DTG Controller"] --> Ledger
Metrics_Engine["Metrics Engine<br>(Path Performance, Trust,<br> Resource Usage)"] --> Ledger
Data_Handler --> Ledger
Policy_Engine -.-> Ledger
end
SCA --- Capability_Manager
Capability_Manager --- Data_Handling_Security
Data_Handling_Security --- Decentralized_Governance_Auditing
end
ATN["Authenticated Trust Network"] --> ATN_Interface
STN_Interface --> STN
Diagram 16e Description: DTG Internals (Patent 28)
This sub-diagram details the internal workings of the Dynamic Trust Gateway (DTG) as described in Patent 28, focusing on its role in mediating secure communication between the Authenticated Trust Network (ATN) and the Sovereign Trust Network (STN) within a single ASKA instance. The diagram emphasizes the secure communication agent's multi-path management, the dynamic capability manager's hardware acceleration, and the data handling and security processes.
Dynamic Trust Gateway (DTG) Internals (Patent 28): This top-level subgraph encapsulates all DTG components.
Secure Communication Agent (SCA): This subgraph details the secure communication paths and their management.
Capability Manager: This subgraph focuses on the dynamic management of capabilities.
Data Handling & Security:
Decentralized Governance & Auditing:
graph LR
subgraph "ASKA System (External Connections)"
direction LR
subgraph "Sovereign Trust Network (STN)"
STN["STN (P27)"] --> NonSwitched_Firewall["Non-Switched<br>Firewall Segment"]
NonSwitched_Firewall --> QR_Gateway["Quantum-Resistant<br>Gateway (P5)"]
QR_Gateway --> Dedicated_Channel["Dedicated Channel (P3)"]
Dedicated_Channel --> External_High_Trust["External High-Trust<br>Environments"]
subgraph "STN Control Plane"
STN_CP["STN Control Plane"]-.- |Minimal Interface|ASKA_Hub_CP
end
STN -.- |Minimal Control Plane<br>Interface|STN_CP
subgraph "Key Recovery Network"
STN --> Sync["Sync Nodes"]
Sync -.- |Authenticated Channels| External_High_Trust
end
end
subgraph "Dynamic Trust Gateway (DTG) (P28)"
DTG --> Switched_Firewall["Switched Firewall<br>(DTG Segment)"]
Switched_Firewall --> Data_Diode["Data Diode (P2)"]
Data_Diode --> QR_Gateway_DTG["Quantum-Resistant<br>Gateway (P5)"]
QR_Gateway_DTG --> Multi_Channel_Network["Multi-Channel<br>Network (P3)"]
Multi_Channel_Network --> External_Systems["External Systems/<br>Zones (P22)"]
DTG --> NonSwitched_Firewall_DTG["Non-Switched<br> Firewall Segment<br>(DTG Segment)"]
NonSwitched_Firewall_DTG --> QR_Gateway
DTG -.- |Control Plane<br>Interface|ASKA_Hub_CP
subgraph "DTG Control Plane"
DTG_CP["DTG Control Plane"] --> Policy_Decision_Point["Policy Decision Point<br>(PDP)"]
PDP --> Policy_Enforcement_Point["Policy Enforcement Point<br>(PEP)"]
PEP --> Switched_Firewall & Data_Diode & QR_Gateway_DTG & Multi_Channel_Network & NonSwitched_Firewall_DTG
ASKA_Hub_CP -.-> DTG_CP
end
DTG -.- DTG_CP
end
subgraph "Automated Evolutionary Software Development (AESDS) (Patent 16)"
AESDS["AESDS"] --> Switched_Firewall_AESDS["Switched Firewall<br>(AESDS Segment)"]
Switched_Firewall_AESDS --> Secure_Comm["Secure Communication<br>(Patents 2, 3, 5)"]
Secure_Comm --> External_Untrusted["External Untrusted<br>Environments (Monitored)"]
IAMA["IAMA Module (P16, C9)"] --> Legacy_System["Legacy System<br>(Connected to STN)"]
AESDS -.-|Software Updates| STN
AESDS -.-|Software Updates| DTG
AESDS -.-|Software Updates| ASKA_Core["ASKA Core"]
end
subgraph "ASKA Hub (Control Plane)"
ASKA_Hub_CP["ASKA Hub<br>(Control Plane)"]
end
STN -.- ASKA_Hub_CP
DTG -.- ASKA_Hub_CP
AESDS -.- ASKA_Hub_CP
end
class sovereign fill:#ccf,stroke:#888
classDef authenticated fill:#aaf,stroke:#666
class STN sovereign
class DTG,AESDS authenticated
Diagram 16f Description: External Integrations
This diagram focuses on the external connections of the DTG (Patent 28) and AESDS (Patent 16), showing how these components interact with systems and networks outside of the ASKA core. It also includes a generalized representation of the STN's external connections for context.
ASKA System (External Connections): This top-level subgraph encapsulates all external connections.
Sovereign Trust Network (STN):
Dynamic Trust Gateway (DTG) (Patent 28): This section details the DTG's multifaceted external connections.
Automated Evolutionary Software Development (AESDS) (Patent 16):
ASKA Hub (Control Plane): Acts as the central control point for managing the STN, DTG, and AESDS.
Key Features Highlighted: