3-ASKA Patents 1of3 20241031
Written by: Paul Lowndes <[email protected]>
Table of Contents
Patent Group I. Core ASKA Architecture (Foundation)
Patent Group II. Enhanced Security and Privacy
Patent 6: Zero-Knowledge Execution Environment with Decentralized Verification and Zone-Based Trust
Patent Group III. Dynamic Resource Management and Optimization
Patent Group IV. Secure User Interface and Chiplet Integration
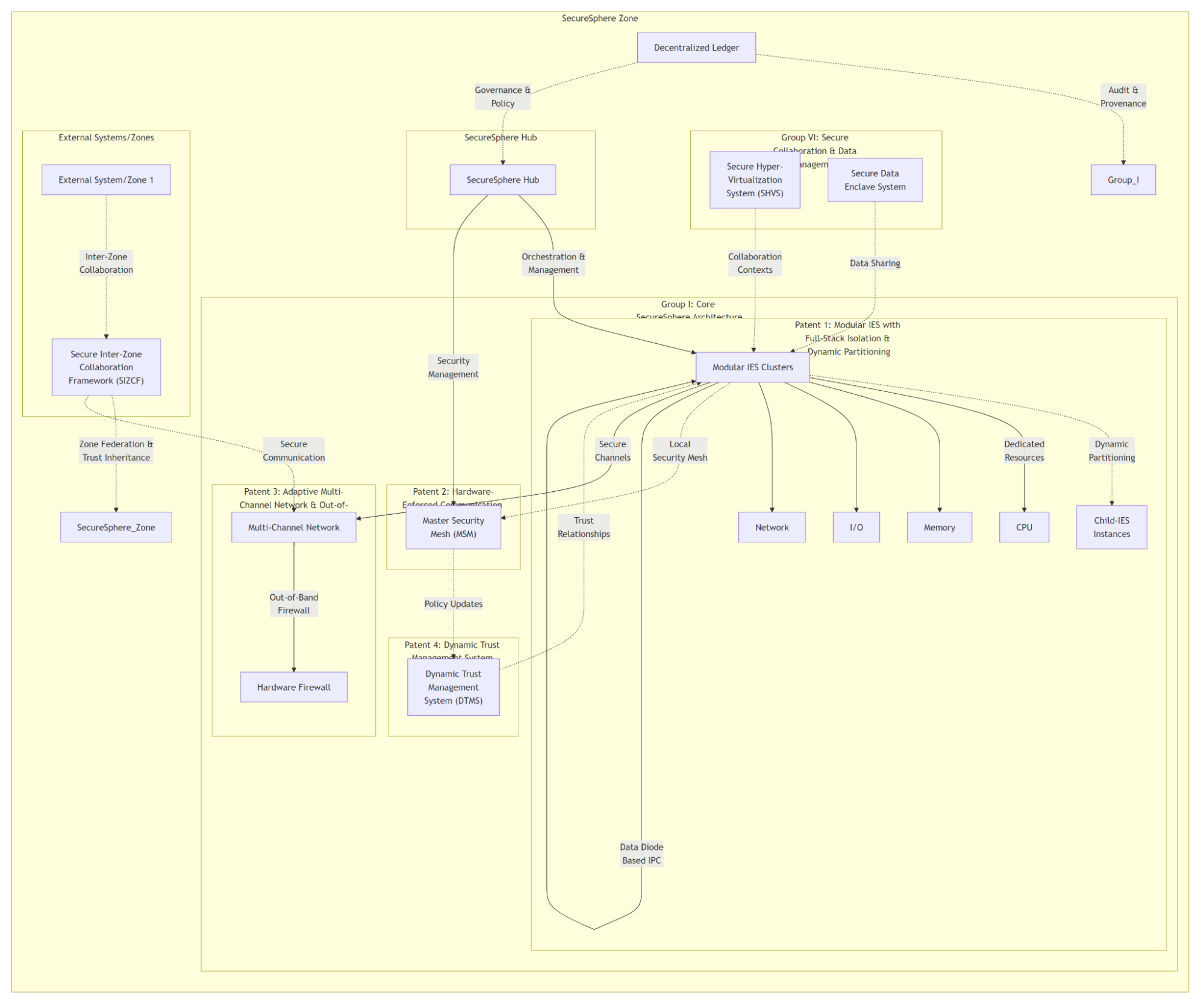
Diagram 1:
graph TD
subgraph "ASKA Zone"
subgraph "Group I: Core ASKA Architecture"
subgraph "Patent 1: Modular IES with Full-Stack Isolation & Dynamic Partitioning"
IES_Cluster["Modular IES Clusters"] -.-> |Dynamic<br>Partitioning| Child_IES["Child-IES<br>Instances"]
IES_Cluster --> |Dedicated<br>Resources| CPU["CPU"]
IES_Cluster --> Memory["Memory"]
IES_Cluster --> IO["I/O"]
IES_Cluster --> Network["Network"]
end
subgraph "Patent 2: Hardware-Enforced Communication & Security Mesh"
IES_Cluster -.- |Local<br>Security Mesh| Master_Security_Mesh["Master Security<br>Mesh (MSM)"]
IES_Cluster ---->|Data Diode<br>Based IPC| IES_Cluster
end
subgraph "Patent 3: Adaptive Multi-Channel Network & Out-of-Band Firewall"
IES_Cluster --> |Secure<br>Channels| Multi-Channel_Network["Multi-Channel Network"]
Multi-Channel_Network --> |Out-of-Band<br>Firewall| Firewall["Hardware Firewall"]
end
subgraph "Patent 4: Dynamic Trust Management System (DTMS)"
Dynamic_Trust_Management_System["Dynamic Trust<br>Management<br>System (DTMS)"] -.- |Trust<br>Relationships| IES_Cluster
Master_Security_Mesh -.- |Policy Updates| Dynamic_Trust_Management_System
end
end
subgraph "ASKA Hub"
ASKA_Hub["ASKA Hub"] --> |Orchestration &<br>Management| IES_Cluster
ASKA_Hub --> |Security<br>Management| Master_Security_Mesh
end
subgraph "Group VI: Secure Collaboration & Data Management"
Secure_Hyper-Virtualization_System["Secure Hyper-<br>Virtualization<br>System (SHVS)"] -.- |Collaboration<br>Contexts| IES_Cluster
Secure_Data_Enclave_System["Secure Data<br>Enclave System"] -.- |Data Sharing| IES_Cluster
end
subgraph "External Systems/Zones"
External_System_1["External System/Zone 1"] -.- |Inter-Zone<br>Collaboration| Secure_Inter-Zone_Collaboration["Secure Inter-Zone<br>Collaboration<br>Framework (SIZCF)"]
end
Secure_Inter-Zone_Collaboration -.- |Zone Federation &<br>Trust Inheritance| ASKA_Zone
Secure_Inter-Zone_Collaboration -.- |Secure<br>Communication| Multi-Channel_Network
Decentralized_Ledger["Decentralized Ledger"] -.- |Audit &<br>Provenance| Group_I
Decentralized_Ledger -.- |Governance &<br>Policy| ASKA_Hub
end
Diagram 1 Description:
Key Connections:
Diagram 2:
graph LR
subgraph "ASKA System"
direction LR
subgraph "IES Cluster (Patent 1)"
IES1["IES 1<br> (Dedicated Resources)"]
IES2["IES 2<br> (Dedicated Resources)"]
IESn["... IES N"]
subgraph "IES 1 (Expanded - Patent 1)"
CPU1["Dedicated CPU"]
Memory1["Dedicated Memory"]
IO1["Dedicated I/O"]
NIC1["Network Interface"]
Zone1["Sub-Zone 1 (Mini-TRC)"]
Zone2["Sub-Zone 2 (Mini-TRC)"]
CPU1 --> ChildIES1["Child IES 1"]
Memory1 --> ChildIES1
IO1 --> ChildIES1
NIC1 --> ChildIES1
ChildIES1 --> Zone1
CPU1 --> ChildIES2["Child IES 2"]
Memory1 --> ChildIES2
IO1 --> ChildIES2
NIC1 --> ChildIES2
ChildIES2 --> Zone2
ChildIES1 -- "Capability-Augmented PCFS (P2)" --> ChildIES2
end
IES1 --> IES_1_Internal
IES2 -.- IECommunication
end
subgraph "Inter IES Communication (Patent 2)"
IECommunication["Capability-based<br>PCFS Communication"]
IECommunication --> DataDiode["Data Diode<br>(Unidirectional)"]
IECommunication ----> CapManager["Capability Manager"]
end
IES_Cluster --> IECommunication
subgraph "Master Security Mesh (MSM) (Patent 2)"
MSM["MSM<br>(Hierarchical)"]
IES1 --> MSM
IES2 --> MSM
IESn --> MSM
end
subgraph "ASKA Hub"
Hub["ASKA Hub"] --> DTMS["DTMS (Patent 4)"]
Hub --> Orchestrator["Orchestrator (P1)"]
DTMS --> CapManager
end
IES_Cluster ----> Hub
MSM ----> Hub
end
style MSM fill:#ccf,stroke:#888
style IECommunication fill:#ccf,stroke:#888
Diagram 2 Description:
Abstract: This invention discloses a secure computing architecture featuring Modular Isolated Execution Stacks (IES), enhanced with hierarchical Zones, decentralized trust management, and path-based inter-component communication. Each IES provides complete hardware-enforced isolation, encompassing dedicated processing, memory, input/output (I/O), and networking resources, preventing unauthorized access and lateral movement of threats. Within each IES, child IES instances are organized into a hierarchy of sub-zones, each associated with a localized Trust Root Configuration (mini-TRC) defining trust roots and policies for granular control. Inter-child-IES communication utilizes a capability-enhanced Packet Carried Forwarding State (PCFS) mechanism, enabling flexible, policy-driven data sharing and resource access. A dynamic partitioning mechanism adjusts child IES instance configurations based on real-time demands and policies, optimizing performance. A dedicated hardware Security Monitor enforces isolation and access control between child IES instances, while a distributed Resource Manager facilitates resource allocation based on zone-specific policies and resource availability, further leveraging a bandwidth reservation system for guaranteed resource access. This integrated approach establishes a robust and adaptable secure computing foundation.
Diagram 1:
graph TD
subgraph "Modular IES Instance (Patent 1)"
subgraph "Dedicated Hardware Resources"
CPU["CPU"]
Memory["Memory"]
Storage["Storage"]
NIC["Network<br>Interface<br>Card"]
IO["I/O<br>Controller"]
end
subgraph "Secure Execution Environment"
Kernel["Secure<br>Kernel"] --> |Loads & Manages| OS["Operating<br>System"]
OS --> |Executes| Applications["Applications"]
Applications -.- |Secure UI Interaction-Patent 11| Secure_UI_Kernel["Secure UI<br>Kernel"]
Applications -.- |Data Sharing-Patent 12| Secure_Data_Enclave["Secure<br>Data Enclave"]
end
subgraph "Local Security Mesh"
Anomaly_Detection["Anomaly<br>Detection<br>Module"] --> |Alert| Isolation_Module["Isolation<br>Module"]
Anomaly_Detection --> |Report| Security_Log["Security Log"]
Anomaly_Detection -.- |Telemetry| Master_Security_Mesh["Master Security<br>Mesh (MSM)"]
end
subgraph "Dynamic Partitioning (Patent 1)"
Resource_Manager["Resource<br>Manager"] --> |Dynamically<br>Partitions| IES_Instance
Resource_Manager --> |Allocates<br>Resources| Child_IES_1["Child-IES<br>Instance 1"]
Resource_Manager --> |Allocates<br>Resources| Child_IES_2["Child-IES<br>Instance 2"]
Child_IES_1 -.- |Data DiodeBased IPC-Patent 2| Child_IES_2
Resource_Manager -.- |Real-time<br>Monitoring| Secure_Execution_Environment
Resource_Manager -.- |Policy Updates| ASKA_Hub["ASKA<br>Hub"]
end
CPU --> Kernel
Memory --> Kernel
Storage --> IO
NIC ----> Firewall["Hardware Firewall<br>(Patent 3)"]
IO --> |Secure Access| Peripherals["Peripherals"]
Local_Security_Mesh -.- Secure_Execution_Environment
Dynamic_Partitioning -.- Secure_Execution_Environment
end
Diagram 1 Description:
Diagram 2:
graph LR
subgraph "ASKA Endpoint (Example)"
direction LR
subgraph "Modular IES Cluster (Patent 1)"
IES_1["IES Instance 1<br>(Web Browser)"]
IES_2["IES Instance 2<br>(Email Client)"]
IES_3["IES Instance 3<br>(Document Editor)"]
IES_Parent["Parent IES<br>(Dynamic Partitioning)"]
IES_1 --> IES_Parent
IES_2 --> IES_Parent
IES_3 --> IES_Parent
subgraph "Hardware Resources (Dedicated per IES)"
CPU["CPU"]
Memory["Memory"]
IO["I/O"]
Network["Network"]
CPU_1["CPU"] --> IES_1
Memory_1["Memory"] --> IES_1
IO_1["I/O"] --> IES_1
Network_1["Network"] --> IES_1
CPU_2["CPU"] --> IES_2
Memory_2["Memory"] --> IES_2
IO_2["I/O"] --> IES_2
Network_2["Network"] --> IES_2
CPU_3["CPU"] --> IES_3
Memory_3["Memory"] --> IES_3
IO_3["I/O"] --> IES_3
Network_3["Network"] --> IES_3
end
end
subgraph "Secure UI Kernel (Patent 11)"
UI_Kernel["Secure UI Kernel"]
UI_Kernel -.- |UI Interaction| IES_1
UI_Kernel -.- |UI Interaction| IES_2
UI_Kernel -.- |UI Interaction| IES_3
end
subgraph "HESE-DAR (Patent 24)"
HESE_DAR["HESE-DAR"]
HESE_DAR -.- |Secure Storage| IES_1
HESE_DAR -.- |Secure Storage| IES_2
HESE_DAR -.- |Secure Storage| IES_3
end
subgraph "Inter-IES Communication (Patent 2)"
Data_Diode["Data Diode"]
IES_1 --> Data_Diode --> IES_2
IES_2 --> Data_Diode --> IES_3
IES_1 -.-> Data_Diode -.-> IES_3
end
subgraph "External Communication (Patent 3)"
Firewall["Firewall"]
IES_1 --> Firewall --> Internet["Internet"]
IES_2 --> Firewall --> Internet
IES_3 --> Firewall --> Internet
end
subgraph "Master Security Mesh (Patent 2)"
MSM["MSM"]
IES_1 --> MSM
IES_2 --> MSM
IES_3 --> MSM
end
%% Positioning and Connections
Modular_IES_Cluster --- Secure_UI_Kernel
Modular_IES_Cluster --- HESE_DAR
Modular_IES_Cluster --- Inter_IES_Communication
Modular_IES_Cluster --- External_Communication
Modular_IES_Cluster --- Master_Security_Mesh
end
subgraph "ASKA Hub (Patents 4, 16)"
Hub["ASKA Hub<br>(Resource Mgmt, DTMS)"] -.-> |Resource Allocation &<br>Security Policies| Modular_IES_Cluster
end
subgraph "Decentralized Ledger (Patents 13, 15)"
Ledger["Decentralized Ledger"] -.-> |Auditing & Governance| ASKA_Hub
Ledger -.-> |Auditing & Provenance| Modular_IES_Cluster
end
Diagram 2 Description:
This diagram illustrates Patent 1 (Modular IES) within a broader ASKA Endpoint context, demonstrating its integration with other key ASKA technologies. The focus is on showcasing how multiple IES instances operate concurrently and securely within a single endpoint, each with dedicated resources and secure communication channels.
Endpoint Focus: The largest subgraph, "ASKA Endpoint," contains all components operating within a single endpoint device. This provides context for the IES cluster.
Modular IES Cluster (Patent 1): This subgraph depicts the core concept of the patent:
IES Instances: Three IES instances are shown, each dedicated to a specific application (Web Browser, Email Client, Document Editor). This exemplifies how different applications can run in isolated environments. Parent IES (Dynamic Partitioning): This visually represents the capability of a parent IES instance to be dynamically partitioned into child IES instances, enabling granular control and flexible resource allocation. Hardware Resources (Dedicated per IES): Each IES instance has its own dedicated set of hardware resources (CPU, Memory, I/O, Network), enforcing strong isolation.
Secure UI Kernel (Patent 11): Shows the secure UI kernel, which allows user interaction with the isolated IES instances without compromising security.
HESE-DAR (Patent 24): The Hardware-Enforced Secure Encrypted Enclave for Data at Rest is included, demonstrating how data stored by each IES instance can be securely encrypted.
Inter-IES Communication (Patent 2): Shows the use of Data Diodes for secure, unidirectional communication between IES instances, preventing unauthorized data flows.
External Communication (Patent 3): Illustrates the Firewall mediating external network access for the IES instances, ensuring secure communication with the outside world.
Master Security Mesh (Patent 2): The MSM provides security monitoring and oversight for all IES instances on the endpoint.
ASKA Hub (Patents 4, 16): Shows the Hub's role in resource management (Patent 10 is implicitly included) and policy enforcement via the Dynamic Trust Management System (DTMS).
Decentralized Ledger (Patents 13, 15): The ledger is shown as providing auditing and governance functions for both the Hub and the IES cluster.
Diagram 3:
graph LR
subgraph "ASKA Zone"
direction LR
subgraph "Patent 1: Modular IES with Full Stack Isolation & Dynamic Partitioning"
IES_Cluster["Modular IES Clusters"] -.-> |Dynamic
Partitioning| Child_IES["Child-IES
Instances"]
IES_Cluster --> |Dedicated
Resources| CPU["CPU"]
IES_Cluster --> Memory["Memory"]
IES_Cluster --> IO["I/O"]
IES_Cluster --> Network["Network"]
end
subgraph "ASKA Hub (Patents 4, 16)"
ASKA_Hub["ASKA Hub"] --> |Orchestration &
Management| IES_Cluster
ASKA_Hub --> |Security
Management| Master_Security_Mesh["Master Security
Mesh (MSM)"]
ASKA_Hub --> |Resource Mgmt| Resource_Manager["Resource Manager (Patent 10)"]
ASKA_Hub --> |DTMS| Dynamic_Trust_Management_System["Dynamic Trust
Management System (DTMS)"]
end
subgraph "Patent 2: Hardware-Enforced Communication & Security Mesh"
IES_Cluster -.- |Local
Security Mesh| Master_Security_Mesh
IES_Cluster ---->|Data Diode
Based IPC| IES_Cluster
end
subgraph "Patent 3: Adaptive Multi Channel Network & Out of Band Firewall"
IES_Cluster --> |Secure
Channels| Multi-Channel_Network["Multi-Channel Network"]
Multi-Channel_Network --> |Out-of-Band
Firewall| Firewall["Hardware Firewall"]
end
subgraph "Patent 11: Secure UI Kernel"
Secure_UI_Kernel["Secure UI Kernel"] -.- |Secure UI Interaction| IES_Cluster
end
subgraph "Patent 20: Secure Data Enclave System"
Secure_Data_Enclave["Secure Data Enclave"] -.- |Secure Data Sharing| IES_Cluster
end
subgraph "Patent 22: Secure InterZone Collaboration Framework"
Secure_Inter-Zone_Collaboration["Secure Inter-Zone
Collaboration Framework (SIZCF)"] -.- |Zone Federation &
Trust Inheritance| ASKA_Zone
Secure_Inter-Zone_Collaboration -.- |Secure
Communication| Multi-Channel_Network
end
subgraph "Decentralized Governance (Patents 13, 15)"
Decentralized_Ledger["Decentralized Ledger"] -.- |Audit &
Provenance| IES_Cluster
Decentralized_Ledger -.- |Governance &
Policy| ASKA_Hub
end
%% Connections
ASKA_Hub --- IES_Cluster
IES_Cluster --- Master_Security_Mesh
IES_Cluster --- Multi-Channel_Network
Secure_UI_Kernel --- IES_Cluster
Secure_Data_Enclave --- IES_Cluster
Secure_Inter-Zone_Collaboration --- ASKA_Zone
Decentralized_Ledger --- ASKA_Hub
Decentralized_Ledger --- IES_Cluster
end
subgraph "External Systems/Zones"
External_System_1["External System/Zone 1"]
External_System_2["External System/Zone 2"]
External_System_3["..."]
end
Secure_Inter-Zone_Collaboration -.- External_Systems/Zones
Description for Diagram 3:
This diagram illustrates the connections between the innovation from Patent 1 (Modular IES with Full-Stack Isolation & Dynamic Partitioning) and the rest of the ASKA architecture.
Key Components and Connections:
How it Connects the Innovation to the Rest of ASKA:
Diagram 4:
graph TD
subgraph "ASKA Endpoint"
subgraph "Modular IES Cluster (Patent 1)"
IES_1["IES Instance 1 <br>(e.g., Web Browser)"]
IES_2["IES Instance 2 <br>(e.g., Email Client)"]
IES_3["IES Instance 3 <br>(e.g., Doc Editor)"]
subgraph "IES 1 Internals (Expanded)"
CPU["Dedicated CPU"]
Memory["Dedicated Memory"]
IO["Dedicated I/O"]
NIC["Network Interface"]
subgraph "Zonal Isolation"
Zone1["Sub-Zone 1 <br>(Mini-TRC)"]
Zone2["Sub-Zone 2 <br>(Mini-TRC)"]
ChildIES1["Child IES 1"] --> Zone1
ChildIES2["Child IES 2"] --> Zone2
ChildIES1 -- "Capability-Augmented PCFS (P2)" --> ChildIES2
end
CPU --> ChildIES1
Memory --> ChildIES1
IO --> ChildIES1
NIC --> ChildIES1
CPU --> ChildIES2
Memory --> ChildIES2
IO --> ChildIES2
NIC --> ChildIES2
subgraph "Secure Execution Environment"
Kernel["Secure Kernel<br>(Secure Boot)"]
OS["Secure OS"]
Kernel --> OS --> Apps["Applications"]
Kernel -.-> Microstructure["Microstructure (P14)"]
end
LSM["Local Security Mesh (P2)"] -.-> AnomalyDetection["Anomaly Detection (P7)"]
LSM -.-> Kernel
ChildIES1 --> LSM
ChildIES2 --> LSM
RM["Resource Manager (P9, P10)"] --> ChildIES1
RM --> ChildIES2
ChildIES1 -.-> DynamicPartitioning
ChildIES2 -.-> DynamicPartitioning
DynamicPartitioning["Dynamic Partitioning & Resource Borrowing<br>(Patents 1, 9)"]
NIC --> Firewall["Firewall (P3)"]
Apps -.-> SecureUIKernel
SecureUIKernel["Secure UI Kernel (P11)"]
end
IES_1 --> IES_1_Internals
IES_2 -.-> InterIESComm
IES_3 -.-> InterIESComm
IES_1 ----> DTMS["DTMS (P4)"]
end
subgraph "Inter-IES Communication (Patent 2)"
DataDiode["Data Diode<br>(Unidirectional)"]
CapManager["Capability Manager <br>(Dynamic)"]
IES_1 --> DataDiode --> IES_2
IES_2 --> DataDiode --> IES_1
DTMS --> CapManager
CapManager --> IES_1
CapManager --> IES_2
CapManager --> IES_3
end
subgraph "ASKA Hub"
Hub["ASKA Hub"] -.-> IES_Cluster
Hub --> DTMS
end
IES_Cluster --> Hub
end
graph TD
subgraph "ASKA Endpoint"
subgraph "Inter#8209;IES Communication (Patent 2)"
DataDiode["Data Diode<br>(Unidirectional)"]
CapManager["Capability Manager <br>(Dynamic)"]
IES_1 --> DataDiode --> IES_2
IES_2 --> DataDiode --> IES_1
DTMS --> CapManager
CapManager --> IES_1
CapManager --> IES_2
CapManager --> IES_3
end
subgraph "Modular IES Cluster (Patent 1)"
IES_1["IES Instance 1 <br>(e.g., Web Browser)"]
IES_2["IES Instance 2 <br>(e.g., Email Client)"]
IES_3["IES Instance 3 <br>(e.g., Doc Editor)"]
IES_2 -.-> InterIESComm
IES_3 -.-> InterIESComm
IES_1 ----> DTMS["DTMS (P4)"]
end
subgraph "ASKA Hub"
Hub["ASKA Hub"] -.-> IES_Cluster
Hub --> DTMS
end
IES_Cluster --> Hub
end
graph
subgraph "ASKA Endpoint"
subgraph "Modular IES Cluster (Patent 1)"
subgraph "IES 1 Internals (Expanded)"
CPU["Dedicated CPU"]
Memory["Dedicated Memory"]
IO["Dedicated I/O"]
NIC["Network Interface"]
subgraph "Zonal Isolation"
Zone1["Sub-Zone 1 <br>(Mini-TRC)"]
Zone2["Sub-Zone 2 <br>(Mini-TRC)"]
ChildIES1["Child IES 1"] --> Zone1
ChildIES2["Child IES 2"] --> Zone2
ChildIES1 -- "Capability-Augmented PCFS (P2)" --> ChildIES2
end
CPU --> ChildIES1
Memory --> ChildIES1
IO --> ChildIES1
NIC --> ChildIES1
CPU --> ChildIES2
Memory --> ChildIES2
IO --> ChildIES2
NIC --> ChildIES2
subgraph "Secure Execution Environment"
Kernel["Secure Kernel<br>(Secure Boot)"]
OS["Secure OS"]
Kernel --> OS --> Apps["Applications"]
Kernel -.-> Microstructure["Microstructure (P14)"]
end
LSM["Local Security Mesh (P2)"] -.-> AnomalyDetection["Anomaly Detection (P7)"]
LSM -.-> Kernel
ChildIES1 --> LSM
ChildIES2 --> LSM
RM["Resource Manager (P9, P10)"] --> ChildIES1
RM --> ChildIES2
ChildIES1 -.-> DynamicPartitioning
ChildIES2 -.-> DynamicPartitioning
DynamicPartitioning["Dynamic Partitioning & Resource Borrowing<br>(Patents 1, 9)"]
NIC --> Firewall["Firewall (P3)"]
Apps -.-> SecureUIKernel
SecureUIKernel["Secure UI Kernel (P11)"]
end
end
end
graph TD
subgraph "ASKA Endpoint"
direction LR
subgraph "Modular IES Cluster (Patent 1)"
subgraph "IES 1 Internals (Expanded)"
CPU["Dedicated CPU"]
Memory["Dedicated Memory"]
IO["Dedicated I/O"]
NIC["Network Interface"]
subgraph "Zonal Isolation"
Zone1["Sub-Zone 1 <br>(Mini-TRC)"]
Zone2["Sub-Zone 2 <br>(Mini-TRC)"]
ChildIES1["Child IES 1"] --> Zone1
ChildIES2["Child IES 2"] --> Zone2
ChildIES1 -- "Capability-Augmented PCFS (P2)" --> ChildIES2
end
CPU --> ChildIES1
Memory --> ChildIES1
IO --> ChildIES1
NIC --> ChildIES1
CPU --> ChildIES2
Memory --> ChildIES2
IO --> ChildIES2
NIC --> ChildIES2
RM["Resource Manager (P9, P10)"] --> ChildIES1
RM --> ChildIES2
ChildIES1 -.-> DynamicPartitioning
ChildIES2 -.-> DynamicPartitioning
DynamicPartitioning["Dynamic Partitioning & Resource Borrowing<br>(Patents 1, 9)"]
NIC --> Firewall["Firewall (P3)"]
end
end
end
graph
subgraph "ASKA Endpoint"
subgraph "Modular IES Cluster (Patent 1)"
subgraph "IES 1 Internals (Expanded)"
subgraph "Zonal Isolation"
ChildIES1["Child IES 1"]
ChildIES2["Child IES 2"]
end
subgraph "Secure Execution Environment"
Kernel["Secure Kernel<br>(Secure Boot)"]
OS["Secure OS"]
Kernel --> OS --> Apps["Applications"]
Kernel -.-> Microstructure["Microstructure (P14)"]
end
LSM["Local Security Mesh (P2)"] -.-> AnomalyDetection["Anomaly Detection (P7)"]
LSM -.-> Kernel
ChildIES1 --> LSM
ChildIES2 --> LSM
Apps -.-> SecureUIKernel
SecureUIKernel["Secure UI Kernel (P11)"]
end
end
end
Description for Diagram 4:
This diagram illustrates the detailed internals of a ASKA endpoint, focusing on the Modular IES Cluster as described in Patent 1 and its integration with the secure communication mechanisms of Patent 2. The diagram uses a layered approach, highlighting the hardware and software components within an IES, the secure communication channels between IES instances, and the overarching management and security provided by the ASKA Hub and the Master Security Mesh (MSM).
1. ASKA Endpoint (Example): This top-level subgraph encapsulates the components and interactions within a representative ASKA endpoint. The "direction LR" declaration sets the layout direction from left to right.
2. Modular IES Cluster (Patent 1): This subgraph represents a cluster of IES instances, the core of ASKA's isolation technology.
3. Inter-IES Communication (Patent 2): This subgraph details the secure communication mechanisms between IES instances.
4. ASKA Hub: Represents the central management entity.
This detailed description clarifies the components, interactions, and data flows within a ASKA endpoint, focusing on the innovations of Patents 1 and 2. The layered structure and explicit patent references aid in understanding the system's architecture and security mechanisms. This visualization is instrumental in conveying the novel aspects and benefits of ASKA's hardware-rooted security approach.
Diagram 5:
graph LR
subgraph ASKA System
A[ASKA Hub] --> B(Dynamic Trust Management System);
A --> C(Automated Evolutionary Software Development System);
A --> D(Multi-Dimensional Audit Trail System);
style A fill:#ccf,stroke:#333,stroke-width:2px
style B fill:#ccf,stroke:#333,stroke-width:2px
style C fill:#ccf,stroke:#333,stroke-width:2px
style D fill:#ccf,stroke:#333,stroke-width:2px
class A,B,C,D secure
end
subgraph "Modular Isolated Execution Stacks (IES)"
E((IES Instance)) --> F(Resource Manager);
E --> G(Security Monitor);
E --> H[Child IES 1];
E --> I[Child IES 2];
F --> B;
G --> B;
H --> B;
I --> B;
H -.-> I;
I -.-> H;
style E fill:#bbf,stroke:#333,stroke-width:2px
style F fill:#bbf,stroke:#333,stroke-width:2px
style G fill:#bbf,stroke:#333,stroke-width:2px
style H fill:#bbf,stroke:#333,stroke-width:2px
style I fill:#bbf,stroke:#333,stroke-width:2px
class E,F,G,H,I ies
subgraph Child IES Communication
H --> J[Capability-Enhanced PCFS];
I --> J;
style J fill:#aaf,stroke:#333,stroke-width:2px
class J communication
end
end
linkStyle 0,1,2,3,4,5,6,7,8,9,10,11,12 stroke:#555,stroke-width:1px
classDef secure fill:#ccf,stroke:#333,stroke-width:2px
classDef ies fill:#bbf,stroke:#333,stroke-width:2px
classDef communication fill:#aaf,stroke:#333,stroke-width:2px
Description for Diagram 5:
This diagram details the architecture of the Modular Isolated Execution Stacks (IES) as defined in Patent 1, showcasing its interaction with ASKA's core components and its internal workings.
1. ASKA Core Components: The top section represents the core ASKA components:
2. Modular Isolated Execution Stacks (IES): This section focuses on the structure and operation of a single IES instance (E) and its constituent parts.
Key Interactions:
Claims:
(a) a hierarchy of Zones, each Zone associated with a localized Trust Root Configuration (mini-TRC) stored on a tamper-evident storage medium, said mini-TRC defining a set of trust roots, trust policies expressible in a declarative language, and inter-zone communication policies for said Zone;
(b) a plurality of child IES instances, each associated with a Zone within said hierarchy, said child IES instance comprising: (i) dedicated and physically isolated processing, memory, input/output (I/O), and networking resources, preventing cross-instance interference; (ii) a local Security Monitor enforcing resource access control and isolation; and (iii) a unique, cryptographically verifiable identifier;
(c) a Dynamic Trust Management System (DTMS) establishing and managing trust relationships between child IES instances within and across Zones, utilizing said mini-TRCs, cryptographic identity verification, dynamic trust metrics derived from observed behavior and declared security posture, and a distributed consensus-based validation mechanism;
(d) a secure communication fabric between said child IES instances comprising dynamically reconfigurable, capability-augmented PCFS channels and hardware-enforced unidirectional communication channels, wherein said PCFS channels utilize hop fields encoding: (i) forwarding information, including source and destination child IES identifiers and path segments within the IES; (ii) dynamically issued capabilities defining permitted actions (read, write, execute), address ranges, and object types accessible within the destination child IES; and (iii) policy information expressed in a declarative language, including at least one of: rate limiting parameters, quality of service (QoS) requirements, or security check specifications;
(e) a dynamic partitioning mechanism, integrated with said DTMS, for securely creating, deleting, and modifying child IES instances, allocating resources to said instances based on real-time workload demands, security requirements, and trust policies defined in said mini-TRCs, and securely migrating workloads between child IES instances while maintaining isolation; and
(f) a distributed Resource Manager facilitating secure and efficient resource borrowing and allocation between said child IES instances based on resource availability, trust relationships, and trust policies defined in said mini-TRCs, further leveraging a bandwidth reservation system for guaranteed resource access.
Dependent Claims:
Abstract: This invention presents a secure communication system for multi-kernel computing environments, specifically designed for enhancing the security and flexibility of interactions between Isolated Execution Stacks (IES). The system employs a dual-channel approach, combining hardware-enforced unidirectional communication channels for high-assurance data flows with dynamically reconfigurable, capability-augmented Packet-Carried Forwarding State (PCFS) channels for flexible, policy-driven communication. PCFS channels utilize hop fields encoding forwarding information, fine-grained capabilities with limited lifetimes and revocation mechanisms, and declarative security policies, enabling precise control over access to resources and permitted actions within destination IES instances. A hierarchical security mesh, comprising local security meshes within each IES and a central Master Security Mesh (MSM), provides real-time monitoring, anomaly detection, and interrupt-based attack mitigation. A consent protocol, enhances security by requiring mutual agreement between IES instances before establishing communication. This integrated approach creates a highly secure, adaptable, and efficient communication framework for multi-kernel systems, mitigating a wide range of attacks, including timing side-channel attacks, while supporting flexible and dynamic inter-component interactions. The system further integrates with ASKA's decentralized governance framework, enabling zone-specific communication policies and distributed policy management.
Diagram 1:
graph TD
subgraph ASKA_System["ASKA System"]
subgraph IES_Cluster["IES Cluster (Patent 1)"]
IES_1["IES 1"]
IES_2["IES 2"]
IES_N["... IES N"]
subgraph IES_1_Internal["IES 1 Internal"]
App_1["Application 1"] --> Data_Diode_1["Data Diode"]
Data_Diode_1 --> Secure_Comm_Bus_1["Secure Comm Bus"]
Local_MSM_1["Local MSM"] --> Data_Diode_1
Local_MSM_1 --> Secure_Comm_Bus_1
end
IES_1 --> IES_1_Internal
subgraph IES_2_Internal["IES 2 Internal"]
Secure_Comm_Bus_2["Secure Comm Bus"] --> App_2["Application 2"]
Data_Diode_2["Data Diode"] --> App_2
Local_MSM_2["Local MSM"] --> Data_Diode_2
Local_MSM_2 --> Secure_Comm_Bus_2
end
IES_2 --> IES_2_Internal
Data_Diode_1 --> IES_2_Internal
IES_1_Internal --> Data_Diode_2
Local_MSM_1 --> MSM["Master Security Mesh (MSM)"]
Local_MSM_2 --> MSM
Local_MSM_N["Local MSM"] --> MSM
DTMS["DTMS (Patent 4)"] --> MSM
MSM -->|Security Policies| DTMS
end
subgraph External_Systems["External Systems"]
Legacy_System["Legacy System"]
External_Network["External Network (Patent 5)"]
Firewall["Firewall (Patent 3)"] --> Legacy_System
Firewall --> External_Network
IES_Cluster ----> Firewall
end
subgraph Secure_UI["Secure UI (Patent 11)"]
UI_Kernel["UI Kernel"]
IES_1 --> UI_Kernel
IES_2 --> UI_Kernel
end
end
style MSM fill:#ccf,stroke:#888,stroke-width:2px
Description of Diagram 1:
This diagram illustrates Patent 2, focusing on Hardware-Enforced Unidirectional Communication and the Security Mesh within the ASKA System. It provides a detailed view of how data diodes and the hierarchical MSM ensure secure data flow and system integrity.
Key Features and Interactions:
Diagram 2:
graph TD
subgraph "ASKA System"
subgraph "Inter-IES Communication (Patent 2)"
IES1["IES 1"]
IES2["IES 2"]
IESn["... IES N"]
IES1 -.- IECommunication
IES2 -.- IECommunication
IESn -.- IECommunication
subgraph "Secure Communication Channels (Patent 2)"
DataDiode["Data Diode<br>(Unidirectional)"]
CapManager["Capability Manager<br>(Dynamic)"]
IES1 --> DataDiode --> IES2
IES2 --> DataDiode --> IES1
DTMS["DTMS (P4)"] --> CapManager
CapManager -->|"Capabilities"| IES1
CapManager -->|"Capabilities"| IES2
end
subgraph "Hierarchical Security Mesh (Patent 2)"
Local_MSM1["Local MSM (IES 1)"] --> MSM
Local_MSM2["Local MSM (IES 2)"] --> MSM
Local_MSMn["...Local MSM (IES N)"] --> MSM
MSM["Master Security Mesh (MSM)"]
IES1 --> Local_MSM1
IES2 --> Local_MSM2
IESn --> Local_MSMn
end
end
subgraph "IES Cluster (Patent 1)"
IES_Cluster["Modular IES Cluster"]
IES1 --> IES_Cluster
IES2 --> IES_Cluster
IESn --> IES_Cluster
subgraph "IES 1 Internal"
CPU1["Dedicated CPU"]
Memory1["Dedicated Memory"]
IO1["Dedicated I/O"]
NIC1["Network Interface"]
IES_Internal_Security["Internal Security<br>Mechanisms (P1)"]
CPU1 --> IES_Internal_Security
Memory1 --> IES_Internal_Security
IO1 --> IES_Internal_Security
NIC1 --> IES_Internal_Security
end
IES1 --> Hardware_Isolation["Hardware Isolation"] --> IES_1_Internal
end
subgraph "ASKA Hub"
Hub["ASKA Hub"] --> DTMS
Hub -.-> Orchestrator["Orchestrator (P1)"]
end
IECommunication ----> Hub
MSM ----> Hub
end
style MSM fill:#ccf,stroke:#888
style IECommunication fill:#aaf,stroke:#666
Description for Diagram 2:
Diagram Rationale and Explanation (Patent 2-centric view relative to Patent 1):
Diagram 3:
graph TD
subgraph "ASKA System"
subgraph "IES Cluster (Patent 1)"
IES1["IES 1"]
IES2["IES 2"]
IESn["... IES N"]
IES1 -.- InterIESComm
IES2 -.- InterIESComm
IESn -.- InterIESComm
end
subgraph "Inter-IES Communication (Patent 2)"
DataDiode["Data Diode (Unidirectional)"]
PCFS["PCFS Channel<br>(Hop Fields & Capabilities)"]
CapManager["Capability Manager (Dynamic)"]
IES1 --> DataDiode --> IES2
IES1 --> PCFS --> IES2
DTMS["DTMS (Patent 4)"] --> CapManager
PolicyEngine["Policy Engine"] --> CapManager
CapManager --> PCFS
MSM["Master Security Mesh (MSM)"] --> PCFS
end
subgraph "ASKA Hub"
Hub["ASKA Hub"] --> DTMS
Hub --> PolicyEngine
Hub --> Orchestrator["Orchestrator (Patent 1)"]
end
InterIESComm --> Hub
MSM --> Hub
subgraph "External Systems (Patents 3, 5)"
Firewall["Firewall (Patent 3)"]
QRGateway["Quantum-Resistant Gateway (Patent 5)"]
External["External Systems"]
Firewall --> External
QRGateway --> External
InterIESComm ----> Firewall
InterIESComm ----> QRGateway
end
end
style InterIESComm fill:#aaf,stroke:#666
style PCFS fill:#ccf,stroke:#888
style CapManager fill:#ccf,stroke:#888
Description for Diagram 3:
This diagram focuses specifically on Patent 2 (Secure Inter-IES Communication System), highlighting its core components and integration within the ASKA system.
Key Features:
This focused diagram effectively visualizes the core innovation of Patent 2 and its role within the ASKA system. It is more concise and easier to understand than a diagram attempting to cover all 24 patents, making it more effective for presentations and technical discussions specifically about Patent 2. It also demonstrates how Patent 2 interacts with Patent 1 and leverages various aspects of ASKA’s security infrastructure. This detailed breakdown clarifies the system's security features, the dynamic nature of the capability management, and its seamless integration within the ASKA architecture.
Diagram 4:
graph LR
subgraph ASKA System
A[ASKA Hub] --> B(Dynamic Trust Management System)
A --> C(Automated Evolutionary Software Development System)
A --> D(Multi-Dimensional Audit Trail System)
style A fill:#ccf,stroke:#333,stroke-width:2px
style B fill:#ccf,stroke:#333,stroke-width:2px
style C fill:#ccf,stroke:#333,stroke-width:2px
style D fill:#ccf,stroke:#333,stroke-width:2px
class A,B,C,D secure
end
subgraph "Secure Inter-IES Communication (Patent 2)"
E[IES Instance 1] -.-> F(Capability Manager)
F --> E
E --> G[Secure Communication Agent]
G --> H["Local Security Mesh (MSM)"]
H --> B
I[IES Instance 2] -.-> F
F --> I
I --> K[Secure Communication Agent]
K --> L["Local Security Mesh (MSM)"]
L --> B
E --> M(Data Diode)
M --> I
G --> N[Capability-Enhanced PCFS]
K --> N
style E fill:#bbf,stroke:#333,stroke-width:2px
style I fill:#bbf,stroke:#333,stroke-width:2px
style F fill:#bbf,stroke:#333,stroke-width:2px
style G fill:#bbf,stroke:#333,stroke-width:2px
style K fill:#bbf,stroke:#333,stroke-width:2px
style H fill:#bbf,stroke:#333,stroke-width:2px
style L fill:#bbf,stroke:#333,stroke-width:2px
style M fill:#bbf,stroke:#333,stroke-width:2px
style N fill:#aaf,stroke:#333,stroke-width:2px
class E,I,F,G,K,H,L,M,N ies
class N communication
end
linkStyle default stroke:#555,stroke-width:1px
classDef secure fill:#ccf,stroke:#333,stroke-width:2px
classDef ies fill:#bbf,stroke:#333,stroke-width:2px
classDef communication fill:#aaf,stroke:#333,stroke-width:2px
Description for Diagram 4:
System for Secure and Trustworthy Computation and Communication
This diagram presents a novel ASKA system and method for achieving secure and trustworthy computation and communication across multiple isolated execution environments (IES) and zones, even in the presence of compromised components or hostile external actors. The ASKA system leverages a combination of hardware-enforced isolation, dynamic trust management, AI-driven security adaptations, and multi-dimensional auditing to provide an unprecedented level of security and resilience.
1. System Architecture:
The ASKA system comprises several interconnected modules, as illustrated in the accompanying diagram. The core components are:
2. Secure Inter-IES Communication:
Secure communication between IES instances is achieved through a novel dual-channel architecture:
The communication architecture incorporates a hierarchical security mesh (MSM) for real-time monitoring and anomaly detection within individual IES instances and across the entire system.
3. Supporting Technologies:
The ASKA system utilizes a variety of supporting technologies, including but not limited to:
4. Claims:
This patent application claims:
Claims:
Independent Claim 1:
A secure communication system for a computing environment comprising a plurality of Modular Isolated Execution Stacks (IES), each IES having dedicated processing, memory, and communication resources, and organized into a hierarchy of Zones, each Zone associated with a Trust Root Configuration (TRC), the system comprising:
(a) secure communication channels between said IES instances, including:
(i) hardware-enforced unidirectional communication channels ensuring data flows in a single, predetermined direction, said channels implemented using at least one of: miniaturized data diodes, dedicated unidirectional network interfaces, or dedicated hardware logic circuits; and
(ii) dynamically reconfigurable, capability-augmented PCFS channels, wherein each PCFS channel utilizes a sequence of hop fields, each hop field encoding:
(1) forwarding information, including source and destination IES instance identifiers, path segments through the multi-channel network (Patent 3), and intermediate relay points;
(2) a dynamically issued capability granting specific access rights (read, write, execute) to designated memory regions or functionalities within the destination IES instance, said capability further specifying permitted address ranges, object types, and a limited lifetime, subject to revocation by a Capability Manager; and
(3) fine-grained policy information, including at least one of: rate limiting parameters, quality of service (QoS) requirements, security check specifications, data sensitivity labels, or communication context metadata, expressed using a declarative language;
(b) a hierarchical Security Mesh, comprising:
(i) a local security mesh within each IES instance, monitoring internal communication events and resource access attempts; and
(ii) a Master Security Mesh (MSM) overseeing the system, receiving security telemetry from said local security meshes, enforcing system-wide security policies, and coordinating security responses, wherein said Security Mesh is integrated with a Dynamic Trust Management System (DTMS) (Patent 4) to manage trust relationships and enforce trust-based access control policies between IES instances;
(c) a consent protocol, wherein establishing a PCFS communication channel between two IES instances requires mutual agreement, said agreement based on at least one of: communication type, data sensitivity level, trust levels of participating IES instances, compliance with predefined communication policies, or resource availability; and
(d) a decentralized policy management system, wherein each Zone can define its own inter-IES communication policies, said policies expressed in a declarative language and stored on a distributed ledger (Patent 15), and wherein a distributed consensus mechanism is used to resolve policy conflicts between Zones.
Dependent Claims:
Abstract: This invention discloses a secure and adaptive multi-channel network architecture for physically isolated execution environments, specifically designed for systems utilizing Modular Isolated Execution Stacks (IES). The architecture features dynamically configurable, physically segregated network channels, each dedicated to a specific security domain, communication purpose, or trust level, preventing cross-channel interference and data leakage. A novel aspect of this invention is the use of declarative policies to define channel configurations, firewall rules, routing policies, and access control mechanisms. These policies, expressed in a high-level language and stored on a decentralized, tamper-proof ledger, enable automated and auditable network management. The architecture incorporates an out-of-band hardware firewall system, operating independently of the primary operating system and IES instances, providing dedicated firewall instances for each network channel with hardware-accelerated policy enforcement. Furthermore, a capability-aware forwarding mechanism leverages capabilities embedded within hop fields of inter-IES communication packets (Patent 2), enabling fine-grained access control and dynamic traffic management based on trust levels, resource availability, and real-time security assessments. The inclusion of dedicated, isolated channels for legacy internet access ensures backward compatibility without compromising the security of the core network. This integrated approach creates a highly secure, adaptable, and efficient multi-channel network, enabling granular control, dynamic adaptation, and automated management while supporting diverse security requirements and legacy system integration.
Diagram:
graph LR
subgraph ASKA_System["ASKA System"]
direction LR
subgraph IES_Cluster["IES Cluster (Patent 1)"]
IES_1["IES 1"]
IES_2["IES 2"]
IES_N["... IES N"]
IES_1 --> NIC_1["Network Interface Card (NIC)"]
IES_2 --> NIC_2["Network Interface Card (NIC)"]
IES_N --> NIC_N["Network Interface Card (NIC)"]
end
subgraph Multi_Channel_Network["Multi Channel Network (Patent 3)"]
Channel_1["Secure Channel 1<br>(e.g., High Trust)"]
Channel_2["Secure Channel 2<br>(e.g., Medium Trust)"]
Channel_3["Secure Channel 3<br>(e.g., Legacy/External)"]
NIC_1 --> Channel_1
NIC_1 --> Channel_2
NIC_2 --> Channel_1
NIC_2 --> Channel_2
NIC_N --> Channel_3
Channel_1 --> Firewall["Out-of-Band Firewall"]
Channel_2 --> Firewall
Channel_3 --> Firewall
Firewall --> External_Entities
Firewall --> Legacy_Systems
end
subgraph External_Connections["External Connections"]
External_Entities["External Entities<br>(Patent 5, 22)"]
Legacy_Systems["Legacy Systems"]
end
subgraph ASKA_Hub["ASKA Hub"]
RM["Resource Manager (Patent 10)"]
DTMS["DTMS (Patent 4)"]
MSM["MSM (Patent 2)"]
DTMS --> Firewall
MSM --> Firewall
Firewall -->|Dynamic Firewall Rules| DTMS
Firewall -->|Threat Intelligence| MSM
end
end
style Firewall fill:#ccf,stroke:#888,stroke-width:2px
Description of Diagram:
This diagram illustrates Patent 3, the Adaptive Multi-Channel Network with an Out-of-Band Firewall, within the ASKA System. It demonstrates how physically segregated channels and the independent firewall enhance security.
Key Features and Interactions:
This diagram effectively visualizes the key innovations of Patent 3 and clarifies how it enables secure and flexible network communication within ASKA. It emphasizes the physical isolation of channels, the independent firewall, and the integration with other security components.
Diagram 2:
graph LR
subgraph "ASKA System"
direction LR
subgraph "IES Cluster (Patent 1)"
IES1["IES 1"]
IES2["IES 2"]
IESn["... IES N"]
IES1 --> NIC1["NIC 1"]
IES2 --> NIC2["NIC 2"]
IESn --> NICn["NIC n"]
end
subgraph "Multi-Channel Network (Patent 3)"
Channel1["Secure Channel 1<br>(e.g., High Trust)"]
Channel2["Secure Channel 2<br>(e.g., Medium Trust)"]
Channel3["Secure Channel 3<br>(e.g., Legacy/External)"]
NIC1 --> Channel1
NIC1 --> Channel2
NIC2 --> Channel1
NIC2 --> Channel2
NICn --> Channel3
Channel1 --> Firewall["Out-of-Band Firewall"]
Channel2 --> Firewall
Channel3 --> Firewall
Firewall --> ChannelManager["Channel Manager<br>(Dynamic)"]
end
subgraph "ASKA Hub"
Hub["ASKA Hub"] --> DTMS["DTMS (Patent 4)"]
Hub --> MSM["MSM (Patent 2)"]
DTMS --> ChannelManager
MSM --> ChannelManager
end
subgraph "External Systems"
External["External Systems/Zones"]
Legacy["Legacy Systems"]
Channel1 -.- External
Channel2 -.- External
Channel3 --> Legacy
end
end
style Firewall fill:#ccf,stroke:#888
style ChannelManager fill:#ccf,stroke:#888
Description for Diagram 2:
This diagram focuses on Patent 3, showcasing the Adaptive Multi-Channel Network and its integration with other ASKA components.
Key Features and Enhancements:
This diagram provides a concise and informative visualization of the key innovations of Patent 3. It highlights the adaptive, secure, and multi-layered nature of the network, making it easier for a technical audience to understand the patent's value proposition. The focused approach allows for a more in-depth illustration of the network architecture and its integration within ASKA, compared to a diagram that attempts to cover all patents simultaneously. This clarity is particularly helpful for investors, partners, and technical discussions focused specifically on the adaptive multi-channel network technology.
DIagram 3:
graph LR
subgraph "ASKA System"
direction LR
subgraph "IES Cluster (Patent 1)"
IES_1["IES 1"]
IES_2["IES 2"]
IES_N["... IES N"]
IES_1 --> NIC_1["Network Interface Card (NIC)"]
IES_2 --> NIC_2["Network Interface Card (NIC)"]
IES_N --> NIC_N["Network Interface Card (NIC)"]
subgraph "NIC 1 Details"
NIC_1 --> CEPM["Capability-Enhanced Packet-Carried Forwarding State<br>(Patent 26)"]
CEPM --> HF["Hop Field Generation"]
CEPM --> PCAP["Packet Capabilities"]
end
NIC_1 --> NIC_1_Details
NIC_2 --> NIC_2_Details["NIC 2 Details"]
end
subgraph "Multi-Channel Network (Patent 3)"
subgraph "Firewall (Dynamically Configurable)"
FW["Firewall<br>(Hardware-Accelerated)"]
Channel_1 --> FW
Channel_2 --> FW
Channel_3 --> FW
subgraph "Firewall Internals"
FW_Instances["Firewall Instances<br>(per Channel)"]
Firewall_Rules["Firewall Rules<br>(Declarative,<br>TRC-based)"] --> FW_Instances
FW_Instances --> Packet_Filter["Packet Filter"]
Packet_Filter --> Forwarding_Engine["Forwarding Engine"]
Forwarding_Engine --> Channel_1_Out & Channel_2_Out & Channel_3_Out
end
FW --> Firewall_Internals
end
Channel_1["Secure Channel 1<br>(e.g., High Trust)"]
Channel_2["Secure Channel 2<br>(e.g., Medium Trust)"]
Channel_3["Secure Channel 3<br>(e.g., Legacy/External)"]
NIC_1 --> Channel_1
NIC_1 --> Channel_2
NIC_2 --> Channel_1
NIC_2 --> Channel_2
NIC_N --> Channel_3
Channel_1 --> Channel_1_Out["To External/Legacy"]
Channel_2 --> Channel_2_Out["To External/Legacy"]
Channel_3 --> Channel_3_Out["To Legacy"]
subgraph "Channel Manager (Dynamic)"
Channel_Manager["Channel Manager"] --> Channel_1 & Channel_2 & Channel_3 & FW
DTMS["DTMS (Patent 4)"] --> Channel_Manager
MSM["MSM (Patent 2)"] --> Channel_Manager
AESDS["AESDS (Patent 16)"] -.-> Channel_Manager
Channel_Manager -->|"Channel Configuration"| DLT["Decentralized<br>Ledger<br>(Patents 13, 15)"]
end
end
subgraph External_Connections["External Connections"]
External_Entities["External Entities<br>(Patent 5, 22)"]
Legacy_Systems["Legacy Systems"]
Channel_1_Out --> External_Entities
Channel_2_Out --> External_Entities
Channel_3_Out --> Legacy_Systems
end
subgraph ASKA_Hub["ASKA Hub"]
RM["Resource Manager (Patent 10)"]
DTMS --> RM
MSM --> RM
AESDS -.-> RM
RM --> Channel_Manager
end
IES_Cluster ----> Multi_Channel_Network
Multi_Channel_Network ----> External_Connections
ASKA_Hub ----> Multi_Channel_Network
end
style Channel_Manager fill:#ccf,stroke:#888,stroke-width:2px
style FW fill:#ccf,stroke:#888,stroke-width:2px
Diagram 3 Description:
ASKA System: This top-level subgraph encapsulates all components related to the Multi-Channel Network.
IES Cluster (Patent 1): Shows how IES instances connect to the network. Includes details of how the NIC generates hop fields and capabilities based on Patent 26.
Multi-Channel Network (Patent 3): This subgraph represents the core of Patent 3.
External Connections: Illustrates how Secure Channels connect to external entities and legacy systems, referencing Patents 5 and 22 for secure external communication.
ASKA Hub: Shows the components within the hub that interact with the Multi-Channel Network. Includes the Resource Manager (Patent 10), which receives input from the DTMS, MSM, and AESDS for dynamic resource allocation to network channels.
Key Improvements and Connections:
Claims:
Independent Claim 1:
A secure multi-channel network architecture for a computing system comprising a plurality of Modular Isolated Execution Stacks (IES) organized into a hierarchy of Zones, each Zone associated with a Trust Root Configuration (TRC) stored on a decentralized, tamper-proof ledger, the architecture comprising:
(a) a plurality of dynamically configurable, physically segregated network channels, each channel dedicated to a specific security domain, communication purpose, or trust level, wherein each channel's configuration is determined by declarative policies expressed in a policy language and stored on said decentralized ledger;
(b) an out-of-band hardware firewall system, operating independently of the primary operating system and IES instances, and associated with each of said network channels, wherein said firewall system comprises:
(i) dedicated, reconfigurable firewall instances for each network channel, enabling granular control over network traffic filtering, security policies, and resource allocation based on said declarative policies;
(ii) hardware-accelerated policy enforcement mechanisms for efficient processing of firewall rules and access control policies; and
(iii) secure communication interfaces with each IES instance, said interfaces employing at least one of hardware-enforced unidirectional communication channels or capability-augmented PCFS channels (Patent 2);
(c) a capability-aware forwarding mechanism that utilizes dynamically generated capabilities and policy metadata embedded within the hop fields of inter-IES communication packets (Patent 2), wherein said mechanism:
(i) dynamically routes network traffic between IES instances and network channels based on capabilities, trust levels of said IES instances, workload requirements, real-time threat assessments, and policy information encoded within said hop fields; and
(ii) enforces access control policies at the data plane level based on said capabilities and policy metadata; and
(d) a Channel Manager, residing within a central management entity and integrated with a Dynamic Trust Management System (DTMS) (Patent 4), dynamically managing said network channels, firewall rules, routing policies, and channel access control based on at least one of: trust levels of said IES instances, real-time resource utilization, system-wide governance policies, TRC configurations, or error handling feedback.
Dependent Claims:
(a) an AI-powered threat detection and analysis engine for identifying and mitigating potential network attacks; and
(b) a mechanism for dynamic updates of firewall rules and policies based on real-time threat intelligence feeds, wherein said updates are authenticated and validated before application.
Abstract:
This invention introduces a Decentralized Dynamic Trust Management System (DTMS) for the ASKA secure computing ecosystem, providing a robust and adaptive framework for secure collaboration and resource sharing within a physically segmented, multi-kernel, zoned environment. The DTMS establishes and manages trust relationships between Isolated Execution Stacks (IES) instances within and across Zones, leveraging distributed Trust Root Configurations (TRCs) stored on a tamper-proof decentralized ledger. The DTMS utilizes cryptographic identity verification, dynamic trust metrics, a distributed consensus-based validation mechanism, and declarative trust policies for fine-grained control. A Decentralized Zone Management System (DZMS) governs zone membership, inter-zone trust, and secure TRC distribution and consistency, utilizing a beaconing mechanism for efficient dissemination of TRC updates. Furthermore, a novel policy negotiation mechanism, enables zones to dynamically establish and agree upon shared trust policies, enhancing collaboration and adaptability. This integrated approach provides a secure, transparent, and resilient trust management system for dynamic and evolving workloads, mitigating the risks associated with centralized trust authorities and promoting flexible, zone-specific security configurations.
Diagram 1:
graph TD
subgraph ASKA_System["ASKA System"]
subgraph IES_Cluster["IES Cluster (Patent 1)"]
IES_1["IES 1"]
IES_2["IES 2"]
IES_N["... IES N"]
end
subgraph DTMS["Dynamic Trust Management System (DTMS) Patent 4"]
TI["Trust Inference Engine"]
TPM["Trust Policy Manager"]
Trust_Level["Trust Level Database"]
PEP["Policy Enforcement Point"]
TI --> Trust_Level
TPM --> Trust_Level
Trust_Level --> PEP
subgraph Trust_Inputs
Metrics_1["IES Metrics (Patent 9/10)"] --> TI
Metrics_2["MSM Security Metrics (Patent 2)"] --> TI
Gov_AI["Governance AI (Patent 15)"] --> TI
Ext_TI["External Trust Indicators"] --> TI
end
end
IES_1 -.- Metrics_1 --> DTMS
IES_2 -.- Metrics_1 --> DTMS
MSM["Master Security Mesh (Patent 2)"] -.- Metrics_2 --> DTMS
subgraph Consumers["Trust Consumers"]
RA["Resource Allocator (Patent 10)"]
Firewall["Firewall (Patent 3)"]
SIZCF["SIZCF (Patent 22)"]
AESDS["AESDS (Patent 16)"]
HESE_DAR["HESE-DAR (Patent 24)"]
UI_Kernel["UI Kernel (Patent 11)"]
end
PEP -->|Access Control Decisions| Consumers
subgraph ASKA_Hub
Hub["Hub"] -->|Policy Configuration| TPM
end
end
style DTMS fill:#ccf,stroke:#888,stroke-width:2px
Description of Diagram 1:
This diagram illustrates Patent 4, the Dynamic Trust Management System (DTMS), and its integration within the ASKA System. It showcases how the DTMS manages trust relationships and enforces policies, influencing various security-sensitive components.
Key Features and Interactions:
This detailed diagram provides a comprehensive overview of Patent 4 and its role in managing trust and enforcing security policies within the ASKA System. It effectively communicates the dynamic, adaptive, and integrated nature of the DTMS, illustrating its importance for ASKA's robust security posture.
Claims:
a. a Dynamic Trust Management System (DTMS) comprising: i. a Trust Inference Engine analyzing trust evidence, including at least one of: real-time security assessments from a hierarchical security mesh (Patent 2), policy updates, operational behavior of IES instances, externally sourced trust indicators, or trust policies defined in the relevant TRCs; ii. a Trust Policy Manager managing declarative trust policies, expressed in a policy language, for controlling trust establishment and verification between IES instances; iii. a Trust Level Database storing and dynamically updating trust levels for each IES instance based on outputs from the Trust Inference Engine and Trust Policy Manager; and iv. a Policy Enforcement Point (PEP) enforcing access control decisions based on trust levels, capabilities (Patent 2), and policies defined in said TRCs, integrated with a secure communication agent (Patent 2) and resource management modules (Patent 9, Patent 10); and
b. a Decentralized Zone Management System (DZMS), integrated with said DTMS and said ledger, for: i. managing Zone membership, recording changes on said decentralized ledger, and utilizing a distributed consensus protocol for consistency and availability of membership updates; ii. establishing and managing trust relationships between Zones by storing, synchronizing, and verifying the authenticity and integrity of TRCs across a distributed network of ASKA Hubs, utilizing a secure communication protocol and a distributed consensus algorithm; iii. facilitating dynamic policy negotiation between Zones, enabling Zones to propose, exchange, and agree upon shared trust policies expressed using said policy language, using a distributed consensus protocol to achieve agreement and recording negotiated policies on said decentralized ledger; and iv. securely distributing TRC updates to relevant ASKA components, utilizing a beaconing mechanism across secure communication channels (Patent 3), including at least one of: unidirectional or capability-augmented PCFS channels (Patent 2), and cryptographic verification of said TRC updates.
a. a digitally signed set of public keys representing trust roots for said Zone; b. a set of rules, expressed using a declarative language, governing trust establishment and verification within said Zone; and c. policy information, expressed using a declarative language, specifying permitted interactions and data flows between IES instances within and across Zones.
Abstract: This invention discloses a quantum-resistant secure communication system for physically isolated execution environments (e.g., Modular Isolated Execution Stacks - Patent 1), integrating path-aware key distribution, dynamic QKD endpoint discovery, and SIBRA bandwidth reservation. The system utilizes Quantum Key Distribution (QKD) to generate and distribute cryptographic keys that are provably secure against attacks from quantum computers, with a distributed key management system (DKM) ensuring resilience and preventing single points of failure. Furthermore, the DKM integrates with SCION's path servers and beaconing process, enabling secure and efficient distribution of keys only along authenticated SCION paths (Patent 2, Patent 3) and dynamic discovery of available QKD endpoints. The system incorporates post-quantum cryptographic algorithms for additional long-term security and utilizes SIBRA (Patent 11) to reserve bandwidth for QKD key exchange and other quantum-resistant communication, ensuring quality of service (QoS) and resilience against denial-of-service attacks. This comprehensive approach provides a robust, adaptable, and future-proof secure communication system for diverse computing environments.
Diagram:
graph TD
subgraph IES_A["IES Instance A"]
App_A["Application A"] --> Data["Data"]
Data --> Encryptor_A["Encryptor (PQC)"]
end
subgraph IES_B["IES Instance B"]
Decryptor_B["Decryptor (PQC)"] --> Data_B["Data"]
Data_B --> App_B["Application B"]
end
subgraph QKD_System["QKD System"]
QKD_A["QKD Module A"] --|Quantum Channel (Secure Key Exchange)| --> QKD_B["QKD Module B"]
QKD_A --> DKM["Distributed Key Manager"]
QKD_B --> DKM
end
subgraph ASKA_Network["ASKA Network (Patent 3)"]
Channel["Secure Channel"]
Encryptor_A --> Channel --> Decryptor_B
end
DKM --|Secure Key|--> Encryptor_A
DKM --|Secure Key|--> Decryptor_B
style DKM fill:#ccf,stroke:#888,stroke-width:2px
Description for Diagram:
This diagram illustrates the key components and interactions of the Quantum-Resistant Secure Communication system described in Patent 5.
Key Features and Interactions:
This diagram provides a clear visualization of how Patent 5 achieves quantum-resistant secure communication within ASKA. It highlights the key technologies employed (QKD, DKM, PQC) and their integration with the ASKA network architecture. This visualization clarifies the system's robust security posture and its readiness for future threats.
Claims:
a. a Quantum Key Distribution (QKD) mechanism for generating and distributing cryptographic keys;
b. a distributed Key Management System (DKM) for storing, managing, and distributing said keys, wherein said DKM integrates with a SCION-based path service (Patent 22) to distribute keys only along authenticated SCION paths;
c. a QKD Endpoint Discovery mechanism that utilizes a beaconing process (Patent 2, Patent 3) to disseminate information about available QKD endpoints, enabling dynamic discovery and selection of quantum-secure communication channels; and
d. a bandwidth reservation mechanism, integrated with SIBRA (Patent 11), that reserves bandwidth for QKD key exchange and other quantum-resistant communication.
a) stores cryptographic keys in multiple physically isolated locations, utilizing at least one of: secure storage elements (Patent 24), or a decentralized ledger (Patent 15); and
b) employs a secure multi-party computation (Patent 19) protocol for managing and accessing said keys.
Abstract: This invention discloses a zero-knowledge execution environment (ZKEE) for secure computing, enhanced with decentralized verification and zone-based trust, designed to protect sensitive data during processing. The ZKEE leverages zero-knowledge proofs, allowing computations to be performed on encrypted data without revealing the underlying information to the executing system. A novel decentralized verification mechanism, distributes the verification process across multiple trusted entities within a ASKA Zone (Patent 18), utilizing a distributed consensus protocol to enhance trust and protect against malicious verification. Hardware-enforced data integrity mechanisms, including memory integrity checks and cryptographic verification, guarantee the integrity of data and computations throughout the execution process. Integration with ASKA's Trust Root Configurations (TRCs) and Dynamic Trust Management System (DTMS) (Patent 4) provides a robust security framework, while support for secure input and output channels enables confidential data transfer. This combined approach provides a robust, secure, and privacy-preserving solution for computation on sensitive data in untrusted or potentially compromised environments.
Diagram:
graph TD
subgraph ZKEE["Zero Knowledge Execution Environment (Patent 6)"]
direction LR
Input["Encrypted Input Data"] --> ZK_Computation_Module["ZK Computation Module"]
ZK_Computation_Module --> Output["Encrypted Output Data"]
subgraph Hardware_Enforcement["Hardware Enforcement"]
Memory_Integrity["Memory Integrity Checks"]
Crypto_Verification["Cryptographic Verification (e.g., Hashing)"]
end
ZK_Computation_Module -.- Memory_Integrity
ZK_Computation_Module -.- Crypto_Verification
subgraph ZK_Proof_System["ZK Proof System"]
Prover["Prover"] --> Verifier["Verifier"]
end
ZK_Computation_Module -.- Prover
Verifier --> Output
end
IES["IES Instance (Patent 1)"] --> Input
Output --> IES
style ZK_Computation_Module fill:#ccf,stroke:#888,stroke-width:2px
Description for Diagram:
This diagram illustrates the key components and interactions within the Zero-Knowledge Execution Environment (ZKEE) as described in Patent 6.
Key Features and Interactions:
This diagram visually represents the core principles of Patent 6, showcasing how the ZKEE protects data privacy and integrity during computation. It clarifies the interactions between its components and emphasizes the role of hardware enforcement and zero-knowledge proofs in achieving its security goals. It also clearly shows the ZKEE's integration within the broader ASKA architecture.
Claims:
a. a zero-knowledge computation module for performing computations on encrypted data within a physically isolated execution environment; b. a decentralized verification system, wherein the verification process for zero-knowledge proofs generated by said computation module is distributed across multiple trusted entities within a Zone, utilizing a distributed consensus protocol to achieve agreement on proof validity and protect against malicious verification; and c. hardware-enforced data integrity mechanisms, including memory integrity checks and cryptographic verification using hardware-based cryptographic modules, ensuring the integrity of data and computations throughout the execution process within said isolated environment.
Key Changes and Rationale:
Abstract: This invention discloses a robust and adaptive anomaly detection and recovery system for secure computing environments, enhanced with secure reporting, zonal response policies, and timing side-channel detection. The system employs hardware-based anomaly detection mechanisms that continuously monitor system behavior, resource utilization, and communication patterns, including the timing of sensitive operations, to identify deviations from expected behavior and potential timing side-channel attacks. A secure reporting mechanism ensures authenticated and tamper-proof transmission of anomaly reports. Hardware-enforced isolation physically disconnects affected components upon anomaly detection, preventing the spread of threats. Automated self-healing procedures, guided by zone-specific policies and managed by a distributed recovery controller, restore system integrity while minimizing downtime. This integrated approach provides a comprehensive and resilient security solution for dynamic and potentially hostile computing environments.
Diagram:
graph LR
subgraph IES_Instance["IES Instance (Patent 1)"]
App["Application"] --> HW_Monitor["Hardware Monitor<br>(Performance, Resources,<br>Behavior, Network)"]
HW_Monitor --> Anomaly_Detector["Anomaly Detector<br>(AI/ML, Patent 10)"]
Local_MSM["Local MSM (Patent 2)"] -.-> Anomaly_Detector
Anomaly_Detector -- Anomaly Detected --> Isolator["Isolator<br>(Hardware-Enforced)"]
Isolator --> Secure_OS["Secure OS (Patent 1)"]
Isolator --> Self_Healer["Self-Healer"]
Self_Healer --> Reset["Reset Component/Chiplet (Patent 12)"]
Self_Healer --> Resource_Reallocation["Resource Reallocation (Patent 10)"]
Self_Healer --> Redeploy["Redeploy Application/Chiplet<br>(Patent 16 - AESDS)"]
Self_Healer --> Verify["Verify System Health"]
Verify -- Healthy --> Secure_OS
Verify -- Unhealthy --> Alert["Alert & Escalate<br>(to ASKA Hub - Patent 2,3)"]
subgraph Chiplet_System["Chiplet System (Patent 12 - Optional)"]
Chiplet["Chiplet"] --> HW_Monitor
Chiplet -.-> Isolator
Chiplet -.-> Self_Healer
end
end
style Anomaly_Detector fill:#ccf,stroke:#888,stroke-width:2px
style Isolator fill:#ccf,stroke:#888,stroke-width:2px
style Self_Healer fill:#ccf,stroke:#888,stroke-width:2px
Description of Diagram:
This diagram illustrates the Hardware-Enforced Anomaly Detection, Isolation, and Self-Healing system within a ASKA IES instance, now including explicit integration with other patents and a clearer depiction of the self-healing process.
Key Features of this Diagram:
This diagram provides a comprehensive and informative visualization of Patent 7, emphasizing its key features, adaptive nature, and tight integration with other ASKA components. It clarifies how the system automatically responds to anomalies and takes corrective actions, enhancing the resilience and security of the overall system.
Claims:
a. hardware-based anomaly detection mechanisms continuously monitoring system behavior, resource utilization, and communication patterns within and between said IES instances, further comprising monitoring the timing of sensitive operations to detect potential timing side-channel attacks; b. a hardware-enforced isolation mechanism for physically isolating affected components upon detection of an anomaly; c. an automated self-healing mechanism for restoring system integrity, guided by zone-specific recovery policies defined in the associated TRCs and managed by a distributed recovery controller; and d. a secure reporting mechanism for transmitting authenticated anomaly reports to designated authorities within a Zone.
Abstract: This invention discloses a system for enhancing memory security within secure execution environments, utilizing a multi-faceted approach combining hardware-based memory obfuscation, segmentation, verification, and capability-based access control. Memory obfuscation techniques, such as address scrambling and randomization, updated dynamically at a frequency comparable to the processor clock, protect against memory probing and reverse engineering attacks, including those exploiting timing side channels. Hardware-enforced memory segmentation isolates critical memory regions, preventing unauthorized access and data leakage. Real-time memory verification mechanisms continuously monitor memory integrity, detecting and responding to any corruption or unauthorized modifications. Furthermore, integration with a capability-based access control system provides fine-grained control over access to obfuscated memory regions, specifying permitted actions (read, write, execute) and address ranges for each capability. This combined approach, augmented with an ORAM-like design for masking memory access patterns, provides robust protection against a wide range of memory-based attacks.
Diagram:
graph LR
subgraph IES_Instance["IES Instance (Patent 1)"]
CPU["CPU"] --> MMU["Memory Management Unit (MMU)"]
MMU --> Memory["Physical Memory"]
subgraph Memory_Protection["Hardware Based Memory Protection (Patent 8)"]
Obfuscator["Memory Obfuscator"]
Segmenter["Memory Segmenter"]
Verifier["Memory Verifier"]
Obfuscator -->|Scrambled Addresses, Randomized Data| Memory
Segmenter -->|Secure Segmentation, Access Control| Memory
Verifier -->|Integrity Checks, Anomaly Detection| Memory
end
MMU -.- Obfuscator
MMU -.- Segmenter
MMU -.- Verifier
subgraph Software["Software"]
OS["Operating System"]
Application["Application"]
OS --> Application
end
Application -.-|Memory Access Requests| MMU
end
style Memory_Protection fill:#ccf,stroke:#888,stroke-width:2px
Description of Diagram:
This diagram illustrates the hardware-based memory protection mechanisms described in Patent 8, integrated within an IES instance.
Key Features and Interactions:
This diagram clearly visualizes how Patent 8's hardware-based memory protection mechanisms operate within an IES instance. It clarifies the functions of each component and highlights their combined effect in creating a robust defense against a wide range of memory-based attacks.
Claims:
a. a hardware-based memory obfuscation mechanism that dynamically scrambles memory addresses and randomizes data stored in memory, wherein the obfuscation parameters are updated at a frequency comparable to the processor clock to protect against timing-based attacks; b. a hardware-enforced memory segmentation mechanism that isolates critical memory regions and enforces access control policies at the hardware level; c. a real-time memory verification mechanism that continuously monitors memory integrity and detects memory corruption or unauthorized modifications; and d. a capability-based access control mechanism, integrated with said memory obfuscation and segmentation mechanisms, for managing access to obfuscated memory regions, wherein each capability grants specific access rights (read, write, execute) and address ranges to designated memory segments.
Abstract:
This invention presents a system for secure resource borrowing and granular I/O management within a secure, zoned computing environment utilizing Modular Isolated Execution Stacks (IES). The system enhances resource utilization, security, and resilience by enabling IES instances to securely lend and borrow idle resources (e.g., processing power, memory, storage) while maintaining strict hardware-enforced isolation and adhering to trust policies defined in Trust Root Configurations (TRCs). A hardware-enforced Secure Resource Borrowing Mechanism (SRBM), employing a PCFS-like mechanism with hop fields for efficient communication of requests and allocations, manages resource access. Granular I/O management is achieved through a hardware-based Isolated I/O Gateway (IIG) incorporating a hardware I/O Switch Fabric and a Zero Trust I/O Handoff Protocol (ZTIOH) utilizing dynamically generated, cryptographically authenticated tokens and unique, verifiable IES identifiers for access control, strengthened with capability-based access rights. A Multipath Communication Manager (MCM) establishes and manages multiple secure communication paths for resource borrowing and I/O operations, optimizing for load balancing, bandwidth aggregation, and fault tolerance while integrating with the DTMS and capability system for enhanced security. Declarative policies, integrated with the DTMS and TRCs, provide flexible control over resource access, enhancing security and adaptability in dynamic computing environments. A Multi-Layered Virtual Console (MLVC) provides secure user interaction with multiple isolated IES environments, and contextual Input/Output Redirection Protocols route signals to the correct IES instance based on the active environment and TRC policies. A secure Resource Return Protocol verifies the state of returned resources and utilizes secure communication channels for resource release notifications.
Diagram:
graph LR
subgraph IES_A["IES Instance A (Borrower)"]
App_A["Application A"] --> LRM_A["Local Resource Manager"]
LRM_A --> SRBM["Secure Resource Borrowing Mechanism"]
end
subgraph IES_B["IES Instance B (Lender)"]
LRM_B["Local Resource Manager"] --> Resource_Pool_B["Available Resources"]
Resource_Pool_B --> SRBM
end
SRBM -- Borrowed Resources --> LRM_A
LRM_A --> App_A
subgraph Shared_Peripherals["Shared Peripherals"]
Peripheral_1["Peripheral 1"]
Peripheral_N["... Peripheral N"]
end
subgraph IIG["Isolated I/O Gateway (IIG)"]
IOSF["I/O Switch Fabric"] --> Peripheral_1
IOSF --> Peripheral_N
ZTIOH["Zero Trust I/O<br>Handoff Protocol"] --> IOSF
LRM_A -- I/O Request --> ZTIOH
LRM_A -.-> Token_Manager["Dynamic Token Manager"] --> ZTIOH
MSM["Master Security Mesh (Patent 2)"] --> Token_Manager["Authorization Policies"]
end
LRM_A ----> IIG
style SRBM fill:#ccf,stroke:#888,stroke-width:2px
style IIG fill:#aaf,stroke:#444
Description for Diagram:
This diagram illustrates the components and processes involved in Secure Resource Borrowing and Granular I/O Management as described in Patent 9.
Key Features Highlighted:
This diagram provides a detailed and comprehensive view of Patent 9's functionalities, clarifying the secure resource borrowing mechanism and granular I/O management within ASKA. It effectively communicates how the system optimizes resource utilization without compromising security and isolation.
Claims:
a. a hardware-enforced Secure Resource Borrowing Mechanism (SRBM) enabling an IES instance to securely borrow idle resources from another IES instance, utilizing a PCFS-like mechanism with hop fields carrying resource requests and allocation information, maintaining strict hardware-level isolation, and adhering to trust policies defined in said TRCs;
b. a Granular I/O Management system, comprising:
i. an Isolated I/O Gateway (IIG) with a hardware-based I/O Switch Fabric, providing secure, time-bound access to shared I/O devices for each IES instance, using unique, cryptographically verifiable identifiers to control and authenticate access; and
ii. a Zero Trust I/O Handoff Protocol (ZTIOH) that secures I/O access through dynamically generated, cryptographically authenticated tokens and capability-based access control (Patent 2), wherein said tokens are verified by the IIG using a secure, side-channel resistant comparison process; and
c. a Multipath Communication Manager (MCM) establishing and managing multiple secure communication paths between IES instances for resource borrowing and I/O operations, utilizing capabilities (Patent 2) and optimizing for at least one of: load balancing, bandwidth aggregation, or fault tolerance, wherein said MCM dynamically adjusts path selection and traffic distribution based on real-time network conditions, security assessments, and resource availability.
a. verifies the trust levels of both the borrowing and lending IES instances using a Dynamic Trust Management System (DTMS) (Patent 4);
b. permits resource borrowing only between IES instances with sufficient trust levels according to the policies defined in the relevant TRCs; and c. utilizes a PCFS-like mechanism for efficient communication of resource requests and allocations, wherein requests and allocations are encoded within hop fields.
a. continuously monitors the availability of resources and trust levels across all IES instances, retrieving real-time resource usage information and TRC-based trust policies from the DTMS (Patent 4); and
b. facilitates secure resource borrowing based on real-time workload demands, available resources, and trust policies, communicating with IES instances using authenticated control messages.
a. enforces strict time-bound access to shared I/O devices, wherein access permissions are dynamically adjusted based on trust levels, resource availability, and real-time security assessments; and
b. utilizes unique, cryptographically verifiable identifiers associated with said IES instances to control and authenticate access to shared I/O devices, enhancing isolation and preventing unauthorized access.
a. a Multi-Layered Virtual Console (MLVC) that enables secure user interaction with multiple isolated IES environments via a unified display; and b. contextual Input and Output Redirection Protocols that dynamically route user input and output signals to the correct IES instance based on the active environment and trust policies defined in said TRCs.
a. verifies the state of returned resources after a borrowing period ends, including hardware-based integrity checks; and b. utilizes secure communication channels (Patent 2) for transmitting resource release notifications.
a. discovers and selects multiple communication paths between IES instances based on path availability, performance metrics (latency, bandwidth), trust levels of intermediate nodes and zones, resource availability, and declarative resource borrowing policies; b. distributes resource borrowing and I/O traffic across said multiple paths using multipath routing protocols; and c. dynamically adjusts path selection and traffic distribution based on real-time network conditions, security assessments, and resource availability.
Abstract:
This invention discloses an AI-powered system for predictive resource allocation and adaptive scaling of Modular Isolated Execution Stacks (IES) within a secure, zoned computing environment, enhancing performance, security, and resilience. The system utilizes an AI-based Predictive Resource Allocation Engine, analyzing real-time workload characteristics, security conditions, historical data, and trust policies, to dynamically allocate resources to IES instances. A Dynamic Scaling Mechanism autonomously provisions or de-provisions IES instances based on real-time demands and security policies, while maintaining hardware-enforced isolation. Furthermore, the system leverages multipath communication for optimized resource allocation and failover, dynamically adjusting resource distribution based on path availability and performance. A novel declarative policy framework enables flexible and expressive resource management, while a secure resource sharing protocol supports efficient and controlled sharing of idle resources between IES instances, utilizing dynamically generated capabilities and adhering to zone-specific trust policies. This integrated approach provides a robust, adaptable, and secure resource management solution for dynamic and evolving workloads.
Diagram:
graph LR
subgraph "AI-Powered Resource Management"
AI_Engine["AI-Based<br>Predictive<br>Engine"] --> |Dynamic Resource<br>Allocation| IES_Cluster["IES Instances"]
AI_Engine --> |Adaptive<br>Scaling| IES_Provisioning["IES<br>Provisioning/De-Provisioning"]
end
IES_Cluster -.- |Real-Time<br>Monitoring Data| AI_Engine
IES_Instance_1["IES Instance 1<br>(CPU, Memory, I/O)"] --> IES_Cluster
IES_Instance_2["IES Instance 2<br>(CPU, Memory, I/O)"] --> IES_Cluster
IES_Instance_3["..."] --> IES_Cluster
subgraph "Governance & Policy"
Security_Policies["Security<br>Policies"] & Compliance["Compliance<br>Requirements"] --> Governance_Framework["Governance<br>Framework"]
end
Governance_Framework -.- |Policy<br>Guidance| AI_Engine
Diagram Description:
Claims:
a. an AI-based Predictive Resource Allocation Engine that analyzes real-time workload characteristics, security conditions, historical data, and trust policies defined in the relevant TRCs to dynamically allocate resources to individual IES instances, wherein said Engine monitors the status of multiple communication paths (Patent 2, Patent 3) and dynamically adjusts resource allocation based on path availability, security posture and performance metrics; b. a Dynamic Scaling Mechanism that autonomously and securely provisions or de-provisions IES instances based on real-time workload demands, available resources, security conditions, and trust policies, while maintaining hardware-enforced isolation between IES instances, utilizing a declarative policy language for expressing scaling policies; and c. a Trust-Aware Resource Optimization module that dynamically adjusts resource allocation and scaling decisions based on trust levels, resource availability, real-time security assessments, performance requirements and predefined security policies, derived from a Dynamic Trust Management System (DTMS) (Patent 4), and trust policies defined in said TRCs.
Diagram:
graph LR
subgraph "ASKA System"
subgraph "Modular IES (Patent 1)"
IES_1["IES Instance 1<br>(Dedicated Resources)"]
IES_2["IES Instance 2<br>(Dedicated Resources)"]
IES_N["... IES Instance N"]
Resource_Manager["Resource Manager<br>(Patent 9, 10)"]
IES_1 --> Resource_Manager
IES_2 --> Resource_Manager
IES_N --> Resource_Manager
end
subgraph "Secure UI Kernel (Patent 11)"
UI_Kernel["Secure UI Kernel<br>(Hardware Isolation)"]
Multi_Region_Buffer["Multi-Region Display Buffer<br>(Trust Levels)"]
Trust_Level_Mgmt["Trust Level Management Module<br>(Dynamic Adjustment)"]
Input_Redirection["Context-Aware Input Redirection<br>(Secure Routing)"]
UI_Rendering["Hardware-Accelerated UI Rendering<br>(Dedicated Hardware)"]
Display_Validation["Hardware-Enforced Display Validation<br>(Checksums, Signatures)"]
UI_Kernel --> Multi_Region_Buffer
UI_Kernel --> Trust_Level_Mgmt
UI_Kernel --> Input_Redirection
Multi_Region_Buffer --> UI_Rendering
UI_Rendering --> Display_Validation
Input_Redirection --> IES_1
Input_Redirection --> IES_2
Input_Redirection --> IES_N
end
subgraph "Modular Chiplet Architecture (Patent 12)"
Chiplet_Orchestration["Chiplet Orchestration Module<br>(Resource Allocation, Workload Distribution)"]
Secure_Chiplet_Interface["Secure Chiplet Interface<br>(Hardware-Enforced, Authentication)"]
Chiplet_Crypto["Chiplet 1<br>(Cryptographic Operations)"]
Chiplet_AI["Chiplet 2<br>(AI Acceleration)"]
Chiplet_IO["Chiplet N<br>(Specialized I/O)"]
Blockchain_Provenance["Blockchain-Based Provenance Tracking<br>(Tamper-Proof Record)"]
Chiplet_Orchestration --> Secure_Chiplet_Interface
Secure_Chiplet_Interface --> IES_1
Secure_Chiplet_Interface --> IES_2
Secure_Chiplet_Interface --> IES_N
Chiplet_Orchestration --> Chiplet_Crypto
Chiplet_Orchestration --> Chiplet_AI
Chiplet_Orchestration --> Chiplet_IO
Blockchain_Provenance --> Chiplet_Orchestration
end
subgraph "Secure Communication"
Secure_Comm_Bus["Hardware-Enforced<br>Communication Bus<br>(Unidirectional Data Flow)"]
IES_1 --> Secure_Comm_Bus
IES_2 --> Secure_Comm_Bus
IES_N --> Secure_Comm_Bus
Secure_Comm_Bus --> UI_Kernel
end
end
style Secure_Comm_Bus fill:#ccf,stroke:#888,stroke-width:2px
style Secure_Chiplet_Interface fill:#ccf,stroke:#888,stroke-width:2px
Diagram Description:
This detailed diagram illustrates the intricate integration of Patent 11 (Secure UI Kernel) and Patent 12 (Modular Chiplet Architecture) within the ASKA system's architecture based on Patent 1 (Modular IES).
1. Modular IES (Patent 1): This section depicts multiple independent IES instances, each with dedicated hardware resources. A Resource Manager is included, highlighting the dynamic resource allocation and management capabilities, drawing from Patents 9 and 10. This section emphasizes the foundational isolated execution environments.
2. Secure UI Kernel (Patent 11): This section details the inner workings of the Secure UI Kernel, including: * Hardware Isolation: Emphasizing the complete separation of the UI kernel from the main processing environments. * Multi-Region Display Buffer: Each region has a dynamically adjustable trust level, enabling secure rendering of critical UI elements. * Trust Level Management Module: Adapts trust levels based on real-time security assessments, system events, and the origin of UI components. * Context-Aware Input Redirection: Securely routes user input to the correct IES instance. * Hardware-Accelerated UI Rendering: Leverages dedicated hardware for enhanced performance. * Hardware-Enforced Display Validation: Uses techniques like checksums and digital signatures to validate the integrity of rendered information.
3. Modular Chiplet Architecture (Patent 12): This section details the dynamic chiplet integration and management: * Chiplet Orchestration Module: This central module is responsible for detecting the insertion and removal of chiplets, managing resource allocation, workload distribution, and communication paths. * Secure Chiplet Interface: A hardware-enforced interface that uses a robust authentication mechanism to prevent unauthorized access. * Chiplets (Crypto, AI, IO): Illustrates diverse chiplets with specialized functions, enhancing system capabilities. * Blockchain-Based Provenance Tracking: Ensures the authenticity and origin of each chiplet are recorded on a blockchain, preventing counterfeit components.
4. Secure Communication: This section emphasizes the secure communication infrastructure. * Hardware-Enforced Communication Bus: Provides a secure, unidirectional communication path between the IES instances and the UI Kernel. This prevents unauthorized reverse communication.
Patent References:
Abstract:
This invention introduces a secure user interface (UI) system for multi-kernel computing architectures, specifically designed for environments utilizing Modular Isolated Execution Stacks (IES). The system features a dedicated UI Kernel that operates in complete hardware isolation from the primary execution environments, ensuring that user interactions do not compromise the underlying system. A key innovation is the treatment of the UI Kernel as a separate ASKA Zone, with its own Trust Root Configuration (TRC) and access control policies, enhancing isolation and preventing interference from potentially compromised IES instances. The UI system employs a multi-region display buffer, with each region assigned a distinct, dynamically adjustable trust level, governed by declarative policies. Hardware-based validation mechanisms, including checksums and digital signatures, ensure the integrity of content rendered in each region. Furthermore, the UI Kernel incorporates hardware-enforced control-flow integrity (CFI) to protect against control-flow hijacking attacks, and critical UI Kernel services are implemented in hardware to minimize the trusted computing base (TCB). A secure, unidirectional communication bus connects the IES instances to the UI Kernel, enforcing data flow control and preventing reverse communication attacks. This comprehensive approach provides a robust and secure UI system resistant to various attack vectors, including control-flow hijacking and display-related attacks, while supporting dynamic trust management and policy-based rendering.
Diagram:
graph LR
subgraph "Secure UI Kernel (Patent 11)"
subgraph "Hardware Isolation Layer"
Dedicated_CPU["Dedicated CPU<br>(Physically Isolated)"]
Dedicated_Memory["Dedicated Memory<br>(Hardware-Enforced Segmentation)"]
Secure_Bus_Interface["Secure Bus Interface<br>(Hardware-Enforced Access Control)"]
end
subgraph "UI Kernel Core"
UI_Kernel_Core["UI Kernel Core<br>(Secure OS, Drivers)"]
Trust_Level_Manager["Trust Level Manager<br>(Dynamic Policy Enforcement)"]
Input_Redirection_Module["Input Redirection Module<br>(Context-Aware Routing)"]
Display_Buffer_Manager["Display Buffer Manager<br>(Multi-Region Allocation)"]
UI_Rendering_Engine["UI Rendering Engine<br>(Hardware Acceleration)"]
Security_Monitor["Security Monitor<br>(Anomaly Detection, Integrity Checks)"]
UI_Kernel_Core --> Trust_Level_Manager
UI_Kernel_Core --> Input_Redirection_Module
UI_Kernel_Core --> Display_Buffer_Manager
UI_Kernel_Core --> UI_Rendering_Engine
UI_Kernel_Core --> Security_Monitor
end
subgraph "Multi-Region Display Buffer"
High_Trust_Region["High-Trust Region<br>(Critical System Alerts, Authentication)"]
Medium_Trust_Region["Medium-Trust Region<br>(Application Data, User Inputs)"]
Low_Trust_Region["Low-Trust Region<br>(Background Processes, Non-Critical Info)"]
Display_Validation_Module["Display Validation Module<br>(Checksums, Digital Signatures)"]
High_Trust_Region --> Display_Validation_Module
Medium_Trust_Region --> Display_Validation_Module
Low_Trust_Region --> Display_Validation_Module
Display_Buffer_Manager --> High_Trust_Region
Display_Buffer_Manager --> Medium_Trust_Region
Display_Buffer_Manager --> Low_Trust_Region
end
subgraph "External Interfaces"
Secure_Comm_Bus["Secure Communication Bus<br>(Unidirectional Data Flow)"]
External_Input["External Input Devices<br>(Keyboard, Mouse, Touch)"]
External_Display["External Display"]
UI_Kernel_Core --> Secure_Comm_Bus
Input_Redirection_Module --> External_Input
UI_Rendering_Engine --> External_Display
end
end
style Secure_Comm_Bus fill:#ccf,stroke:#888,stroke-width:2px
Diagram Description:
This diagram delves into the internal architecture of the Secure UI Kernel (Patent 11), illustrating its key components and their interactions. The diagram emphasizes the hardware isolation, multi-region display buffer, and dynamic trust management mechanisms.
1. Hardware Isolation Layer: This layer ensures complete physical and logical isolation of the UI kernel. * Dedicated CPU (Physically Isolated): A dedicated CPU prevents interference from other processes. * Dedicated Memory (Hardware-Enforced Segmentation): Physically isolated memory prevents unauthorized access. * Secure Bus Interface (Hardware-Enforced Access Control): Controls access to the system bus to prevent unauthorized communication.
2. UI Kernel Core: This is the central processing unit of the secure UI kernel. * UI Kernel Core (Secure OS, Drivers): A specialized operating system and drivers for secure UI management. * Trust Level Manager (Dynamic Policy Enforcement): Dynamically adjusts trust levels for different regions of the display buffer. * Input Redirection Module (Context-Aware Routing): Securely routes user input to the appropriate IES instance based on context. * Display Buffer Manager (Multi-Region Allocation): Manages the allocation of memory within the multi-region display buffer. * UI Rendering Engine (Hardware Acceleration): Utilizes dedicated hardware for high-performance UI rendering. * Security Monitor (Anomaly Detection, Integrity Checks): Continuously monitors the UI kernel for anomalies and ensures data integrity.
3. Multi-Region Display Buffer: This section highlights the key feature of the secure UI system. Each region has a defined trust level that determines the type of information it can display and the access privileges it has. * High-Trust Region (Critical System Alerts, Authentication): Displays highly sensitive information. * Medium-Trust Region (Application Data, User Inputs): Displays less sensitive data. * Low-Trust Region (Background Processes, Non-Critical Info): Displays non-sensitive information. * Display Validation Module (Checksums, Digital Signatures): Ensures the integrity of information displayed in each region.
4. External Interfaces: These components handle communication with external systems and devices. * Secure Communication Bus (Unidirectional Data Flow): Provides a secure unidirectional communication path to the main ASKA system, preventing any potential reverse attacks. * External Input Devices (Keyboard, Mouse, Touch): Handles user input. * External Display: Connects to the physical display.
Patent References: This diagram is specifically designed to detail the internal workings of Patent 11, focusing on the claims related to hardware isolation, the multi-region display buffer, and the dynamic trust management. The diagram’s structure and component call-outs reflect the key aspects of this patent.
This detailed diagram illustrates the internal design of the Secure UI Kernel, clarifying its security features and mechanisms. The diagram’s components and their connections help to understand how hardware isolation, multi-region buffer, and dynamic trust level management work together to provide a secure user experience. The layered approach and clear separation of concerns highlighted in the diagram contribute to the system's resilience and security.
Claims:
(a) a dedicated UI Kernel operating in complete hardware isolation from said IES instances, said UI Kernel comprising: (i) a dedicated CPU and physically isolated memory with hardware-enforced segmentation, preventing unauthorized access from other components; (ii) a secure, hardware-enforced communication bus connecting said IES instances to said UI Kernel, enforcing unidirectional data flow from said IES instances to said UI Kernel; (iii) a multi-region display buffer, each region assigned a dynamically adjustable trust level based on the origin and sensitivity of displayed information, governed by declarative policies expressed in a policy language; (iv) a hardware-based Display Validation Module ensuring the integrity and authenticity of content rendered within each region of said display buffer, utilizing checksums, digital signatures, or a combination thereof; and (v) a hardware-enforced control-flow integrity (CFI) mechanism protecting the UI Kernel's execution flow from unauthorized modification or hijacking, said CFI mechanism integrated with access control policies based on program execution states.
(b) a Trust Root Configuration (TRC) specifically for said UI Kernel, said TRC stored on said decentralized ledger, defining a set of trust roots, trust policies, and access control rules for the UI Kernel and its associated Zone;
(c) a Policy Engine within said UI Kernel interpreting and enforcing said declarative policies, dynamically adjusting trust levels of display regions based on the origin of UI components, and controlling access to UI resources based on trust levels, capabilities (Patent 2), and TRC policies; and
(d) a Secure UI Integration Module facilitating secure communication between the UI Kernel and the ASKA Hub, leveraging the Secure Inter-Zone Collaboration Framework (SIZCF - Patent 22) for inter-zone communication and coordinating policy updates, wherein said module supports remote attestation of the UI Kernel using hardware-rooted trust mechanisms.
Dependent Claims:
Abstract:
This invention discloses a secure and adaptive chiplet architecture for dynamic application execution within secure computing environments, such as those utilizing Modular Isolated Execution Stacks (IES). The architecture integrates hot-swappable chiplets, each dedicated to specific computational tasks, with a secure, hardware-enforced interface enabling dynamic and authenticated integration and removal during runtime. A Chiplet Orchestration Module, leveraging AI-driven workload analysis and dynamic resource allocation, manages chiplet integration, resource assignment, and workload distribution. Furthermore, a capability-based access control system governs access to chiplet functionalities, enabling dynamic control over chiplet features based on trust levels, security policies, and resource availability. Integration with SIBRA (Patent 11) provides bandwidth reservation and QoS guarantees for individual chiplets, enhancing performance and preventing resource contention. A hardware-enforced isolation mechanism, combined with a Security Monitor, ensures secure chiplet operation and protects against unauthorized access or interference. This modular architecture provides enhanced flexibility, performance, and security for evolving workloads and emerging applications in dynamic and potentially hostile environments.
Diagram
graph LR
subgraph "Modular Chiplet Architecture (Patent 12)"
subgraph "Chiplet Orchestration Module"
Workload_Analyzer["Workload Analyzer<br>(AI-driven, Real-time Analysis)"]
Resource_Allocator["Resource Allocator<br>(Dynamic Resource Assignment)"]
Chiplet_Selector["Chiplet Selector<br>(Optimal Chiplet Selection)"]
Power_Manager["Power Manager<br>(Energy-Aware Chiplet Control)"]
Security_Monitor["Security Monitor<br>(Anomaly Detection, Integrity Checks)"]
Blockchain_Manager["Blockchain Manager<br>(Provenance Tracking, Authentication)"]
Workload_Analyzer --> Resource_Allocator
Workload_Analyzer --> Chiplet_Selector
Resource_Allocator --> Chiplet_Selector
Chiplet_Selector --> Secure_Interface
Power_Manager --> Chiplet_1
Power_Manager --> Chiplet_2
Power_Manager --> Chiplet_N
Security_Monitor --> Chiplet_Orchestration
Blockchain_Manager --> Chiplet_Orchestration
end
subgraph "Secure Chiplet Interface"
Secure_Interface["Secure Chiplet Interface<br>(Hardware-Enforced, Authentication)"]
Secure_Comm_Channels["Secure Communication Channels<br>(Dedicated, Isolated)"]
Authentication_Module["Authentication Module<br>(Digital Signatures, Encryption)"]
Secure_Interface --> Secure_Comm_Channels
Secure_Interface --> Authentication_Module
Secure_Interface --> IES_1
Secure_Interface --> IES_2
Secure_Interface --> IES_N
end
subgraph "Chiplets"
Chiplet_1["Chiplet 1<br>(e.g., Cryptographic Accelerator)"]
Chiplet_2["Chiplet 2<br>(e.g., AI Accelerator)"]
Chiplet_N["Chiplet N<br>(e.g., Specialized I/O)"]
end
subgraph "Secure Programming Framework"
DSL_Compiler["DSL Compiler<br>(Domain-Specific Languages)"]
SDK_Integration["SDK Integration<br>(Pre-built Functions, Libraries)"]
Secure_Debugging["Secure Debugging Tools<br>(Protected Access, Monitoring)"]
end
end
IES_1["IES Instance 1"]
IES_2["IES Instance 2"]
IES_N["... IES Instance N"]
style Secure_Interface fill:#ccf,stroke:#888,stroke-width:2px
style Secure_Comm_Channels fill:#ccf,stroke:#888,stroke-width:2px
Diagram Description:
This diagram details the internal architecture of the Modular Chiplet Architecture (Patent 12), emphasizing its key components and their interactions.
1. Chiplet Orchestration Module: This module manages the overall operation of the chiplet system.
* **Workload Analyzer (AI-driven, Real-time Analysis):** Analyzes workload characteristics to determine the optimal chiplet configuration.
* **Resource Allocator (Dynamic Resource Assignment):** Dynamically allocates system resources (CPU, memory, bandwidth) to chiplets based on workload demands.
* **Chiplet Selector (Optimal Chiplet Selection):** Selects the most appropriate chiplets based on workload analysis and resource availability.
* **Power Manager (Energy-Aware Chiplet Control):** Manages the power state of chiplets to optimize energy consumption.
* **Security Monitor (Anomaly Detection, Integrity Checks):** Continuously monitors the chiplet system for anomalies and ensures data integrity.
* **Blockchain Manager (Provenance Tracking, Authentication):** Manages the blockchain-based provenance tracking, authenticating the chiplets and verifying their integrity.
2. Secure Chiplet Interface: This interface ensures secure communication and access control for chiplets.
* **Secure Chiplet Interface (Hardware-Enforced, Authentication):** A hardware-enforced interface to prevent unauthorized access.
* **Secure Communication Channels (Dedicated, Isolated):** Dedicated, isolated communication channels for each chiplet.
* **Authentication Module (Digital Signatures, Encryption):** Uses digital signatures and encryption to verify chiplet authenticity and protect data in transit.
3. Chiplets: This section shows different types of chiplets with specialized functionalities.
* **Chiplet 1 (e.g., Cryptographic Accelerator):** A chiplet specialized for cryptographic operations.
* **Chiplet 2 (e.g., AI Accelerator):** A chiplet optimized for AI-related computations.
* **Chiplet N (e.g., Specialized I/O):** A chiplet for specialized input/output operations.
4. Secure Programming Framework: This framework simplifies chiplet development and integration.
* **DSL Compiler (Domain-Specific Languages):** Compiles code written in domain-specific languages for each chiplet type.
* **SDK Integration (Pre-built Functions, Libraries):** Provides pre-built functions and libraries to streamline the integration process.
* **Secure Debugging Tools (Protected Access, Monitoring):** Provides tools for debugging chiplets without compromising system security.
5. IES Instances: The diagram shows how multiple IES instances (Patent 1) can utilize the chiplet module.
Patent References: This diagram is a detailed illustration of Patent 12, specifically highlighting the modularity, secure interfaces, and dynamic management of the chiplet architecture. The components and their interactions reflect the claims made within the patent document. The use of blockchain for provenance adds an extra layer of security, protecting the system from malicious chiplets.
This detailed diagram clarifies the internal structure and operation of the Modular Chiplet Architecture (Patent 12). It illustrates the dynamic resource management, secure communication, and robust security features that enable secure and efficient execution of specialized functions. The modular design and ability to hot-swap chiplets make the system highly adaptable to changing needs and workloads. The integration with the IES architecture is clearly represented, highlighting the synergy between the two.
Claims:
(a) a plurality of hot-swappable chiplets, each chiplet dedicated to a specific computational task and having a secure cryptographic identifier, wherein said identifier is recorded on said decentralized ledger to ensure authenticity and provenance; (b) a secure, hardware-enforced interface enabling authenticated connection and disconnection of chiplets to/from an IES during runtime, utilizing at least one of: a challenge-response protocol, digital signatures, or other cryptographic authentication mechanisms to verify chiplet integrity and authenticity; (c) a Chiplet Orchestration Module that dynamically manages: (i) integration and removal of said chiplets; (ii) allocation of resources to said chiplets and IES instances based on workload demands, security policies defined in said TRCs, and real-time resource availability; (iii) distribution of workloads across said chiplets and IES instances; and (iv) secure communication between chiplets, utilizing dedicated channels and protocols, including hardware-enforced unidirectional channels (Patent 2) or capability-augmented PCFS channels (Patent 2), ensuring data integrity and confidentiality during inter-chiplet communication; (d) a capability-based access control system that manages access to chiplet functionalities based on dynamically issued and managed capabilities, wherein each capability grants specific access rights (read, write, execute) and address ranges to designated memory regions or functionalities within a chiplet, dynamically enabling or disabling chiplet features based on trust levels derived from a Dynamic Trust Management System (DTMS) (Patent 4), security policies defined in said TRCs, and resource availability; and (e) a hardware-enforced isolation mechanism, integrated with a Security Monitor, that isolates chiplet operations within a secure execution environment, preventing unauthorized access or interference between chiplets, or between chiplets and other system components, wherein said isolation mechanism utilizes at least one of: physically separate memory regions, dedicated communication channels, hardware-based access control lists (ACLs), or a combination thereof, and wherein said Security Monitor dynamically manages access control policies, resource allocation, and isolation boundaries based on policy updates from the DTMS and real-time threat assessments.