ASKA Architecture: A Comprehensive Overview
ASKA Architecture: A Comprehensive Overview
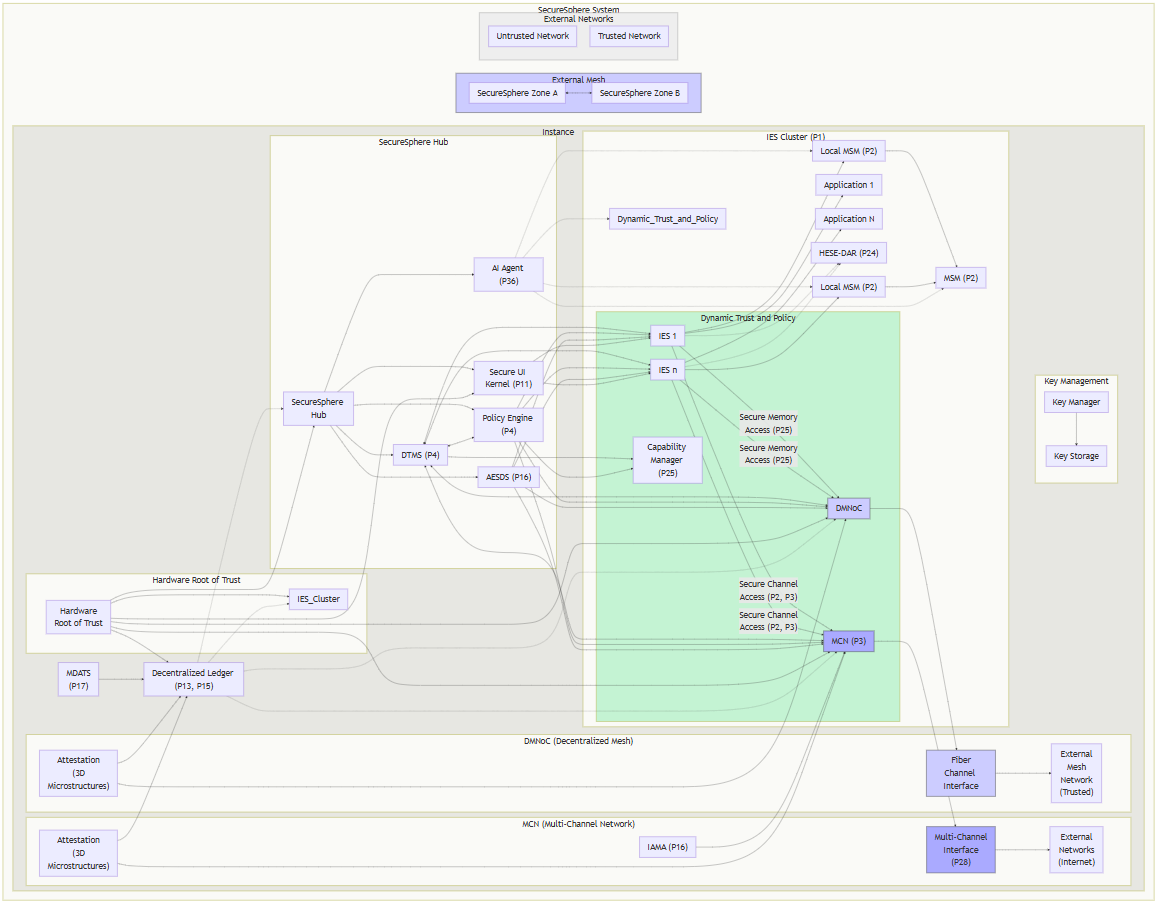
This diagram provides a comprehensive overview of the ASKA architecture, highlighting its key technologies and their interactions. The system emphasizes modularity, robust security features, and dynamic adaptability.
ASKA System
This top-level view encapsulates all components of a ASKA instance and its connections to external entities.
ASKA Instance (Local)
This section details the core components within a single ASKA instance.
IES Cluster (P1)
The foundation of ASKA’s hardware-enforced isolation. Multiple IES (Isolated Execution Stack) instances run different applications concurrently, each with dedicated hardware resources (CPU, memory, I/O, network). Key features include:
- Dynamic Partitioning: IES instances can be dynamically divided into smaller, isolated child-IES instances to optimize resource utilization and further enhance security.
- Hierarchical Zones: Hierarchical zones within each IES, governed by mini-TRCs (Trust Root Configurations) stored on tamper-evident media (P13/P15), provide granular trust and policy management.
- Secure Resource Borrowing (SRBM - P9): Enables efficient resource utilization while maintaining isolation.
- Secure Communication: Inter-IES communication utilizes secure channels (P2, P3) and capability-aware forwarding (P26). Local Security Meshes (LSMs - P2) monitor each IES instance and report to the Master Security Mesh (MSM - P2).
- Data at Rest Encryption: The Hardware-Enforced Secure Encrypted Enclave for Data at Rest (HESE-DAR - P24) provides hardware-level encryption for data at rest.
- Connections: The IES Cluster connects to the DMNoC (Decentralized Mesh NoC), the MCN (Multi-Channel Network), the ASKA Hub, and the AI Agent.
DMNoC (Decentralized Mesh NoC)
A secure, high-bandwidth mesh network for inter-IES communication and connections to trusted external ASKA instances. Key features include:
- Decentralized Mesh Topology: Provides redundancy and fault tolerance.
- Hardware Attestation (3D Microstructures - P14): Ensures the integrity of DMNoC components.
- Fiber Channel Interface: Provides high-bandwidth connectivity to external networks.
- Integration: The DMNoC integrates with the IES Cluster, DTMS, Policy Engine, and AI Agent.
MCN (Multi-Channel Network)
Provides secure communication channels for connecting to external networks (Internet, trusted networks). Key features include:
- Multi-Channel Architecture (P3): Physically segregated channels with dedicated firewalls prevent cross-channel interference.
- Quantum-Resistant Communication (P5): Employs QKD, DKM, and PQC to secure communication against quantum computer attacks.
- Dynamic Routing (P3): Adapts to real-time security assessments and trust levels.
- IAMA (P16): Analyzes connected legacy systems to proactively identify and mitigate vulnerabilities.
- Integration: The MCN integrates with the IES Cluster, DTMS, Policy Engine, AI Agent, and IAMA.
ASKA Hub
The central management and control component for the local instance. It orchestrates and manages all other components, enforcing policies, and managing resources. It encompasses:
- Dynamic Trust Management System (DTMS - P4): Manages trust relationships and access control based on dynamic metrics.
- Policy Engine (P4): Enforces security policies.
- AI Agent (P36): Monitors, analyzes, and adapts security measures.
- Automated Evolutionary Software Development System (AESDS - P16): Continuously updates and improves ASKA software.
- Secure UI Kernel (P11): Provides a secure user interface.
- Key Management: Manages cryptographic keys for secure communication.
Dynamic Trust and Policy
This subgraph represents the core of ASKA’s dynamic security, encompassing:
- Bidirectional Communication: DTMS, Policy Engine, and Capability Manager (P25) communicate bidirectionally, dynamically adjusting trust levels and capabilities.
- Policy Influence: Dotted lines show how trust levels and policies influence the IES Cluster, DMNoC, and MCN.
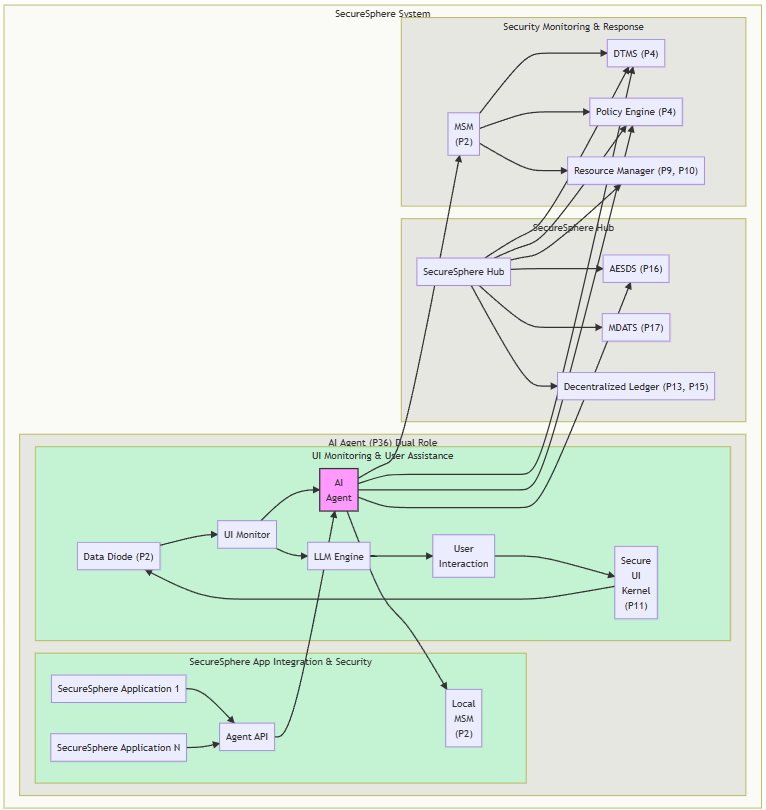
AI Agent (P36)
A crucial component responsible for:
- System-wide Monitoring: Monitors all aspects of system behavior and network communication.
- Anomaly Detection: Employs AI/ML for detecting anomalies.
- Adaptive Security: Coordinates security responses and dynamically adjusts security measures.
- Policy Influence: Provides recommendations and influences policy updates.
AESDS (P16)
The AI-driven system responsible for:
- Continuous Software Updates: Continuously monitors, updates, and improves ASKA’s software.
- Proactive Security Patching: Proactively generates and deploys security patches and updates.
- Integration: Manages updates across all ASKA components.
Secure UI Kernel (P11)
Provides a secure and isolated user interface environment with:
- Zonal Isolation: Isolates UI from the underlying system.
- Hardware-Enforced Control-Flow Integrity (CFI): Prevents code injection attacks.
- Declarative Policy-Based Rendering: Controls UI rendering based on policies.
Hardware Root of Trust (HRoT)
The foundation of ASKA’s trust, providing:
- Attestation: Verifies the integrity of system components.
- Key Generation: Generates cryptographic keys.
- Validation Services: Provides validation services to all modules.
- Tamper-Proof Auditing: Creates tamper-proof auditable records via MDATS (P17) and 3D Microstructures (P14) utilizing the Decentralized Ledger (P13, P15).
External Connections
External Mesh Network (Trusted)
ASKA instances connect and exchange information securely, leveraging the DMNoC’s high-bandwidth capabilities.
External Networks
ASKA connects to various external networks (Internet, trusted networks) via the MCN, with IAMA (P16) monitoring and managing this interface.
Key Features and Technologies
This section summarizes the core technologies underpinning ASKA’s security and functionality:
- Hardware-Rooted Trust (P1, P13, P33): Secure Boot, attestation, and 3D microstructures for tamper evidence.
- Isolated Execution Stacks (P1): Hardware-enforced isolation with dynamic partitioning and hierarchical zones for granular security.
- Dynamic Trust Management (P4): Dynamic trust metrics, decentralized zone management, and policy negotiation for adaptive security.
- Secure Communication Channels (P2, P3): Data diodes for unidirectional flows, multi-channel network with quantum-resistant options (P5).
- AI-Driven Security (P2, P7, P36): Proactive threat detection, automated responses, and adaptive security policies.
- Capability-Based Access Control (P25, P26): Fine-grained access control at the data plane level.
- Data Encryption (P5, P24): HESE-DAR for data at rest, and quantum-resistant encryption for data in transit.
- Auditing and Accountability (P13, P15, P17): Decentralized ledger, MDATS, and 3D microstructures for comprehensive auditing.
ASKA represents a paradigm shift in secure computing, offering a robust, adaptable, and trustworthy platform for high-assurance operations in diverse environments. The modularity, dynamic adaptability, and multi-layered defense mechanisms address the limitations of traditional systems, creating a highly resilient and future-proof solution, especially in the context of evolving threats and the increasing importance of secure, decentralized computing.
[Continue reading for detailed AI Agent integration documentation…]