ASKA: Secure Computing Architecture
Secure Computing Architecture
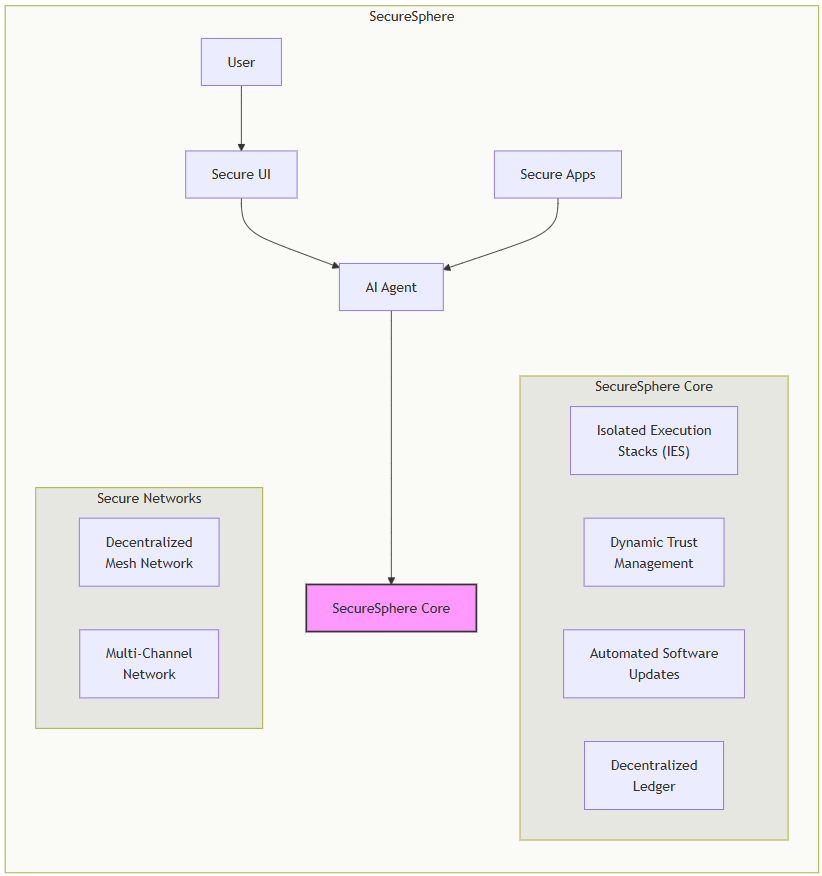
ASKA (Adaptive Secure Kernel Architecture) represents a departure from traditional computing architectures, offering a fundamentally new approach to building secure applications. At its core lies a multi-kernel design utilizing Modular Isolated Execution Stacks (IES), each providing complete hardware-enforced isolation for applications and processes. This hardware-level compartmentalization minimizes the impact of vulnerabilities, preventing lateral movement of attacks and effectively containing breaches within individual IES instances. This robust isolation is further enhanced by a sophisticated capability-based access control system, dynamically managed by the Dynamic Trust Management System (DTMS), which continuously assesses and adjusts trust levels based on real-time system behavior, user actions, and threat intelligence, thereby tailoring access permissions to each application. This unique combination of hardware isolation and dynamic trust management drastically reduces the attack surface and ensures that only authorized components and processes can access sensitive data and resources.
ASKA’s innovative security posture is further fortified by a multi-layered networking architecture. Two distinct networks operate independently: a Decentralized Mesh Network on Chip (DMNoC) for high-bandwidth, low-latency, peer-to-peer communication within and between ASKA instances, and a Multi-Channel Network (MCN) for mediating interaction with external networks, ranging from highly trusted, dedicated government networks to the potentially untrusted public internet. The DMNoC, with its mesh topology and hardware attestation using 3D microstructures, provides resilience against node failures and attacks targeting individual components. The MCN, meanwhile, uses physically segregated channels with dedicated firewalls and quantum-resistant cryptography (where appropriate) to ensure secure and authenticated external communications, integrating Isomorphic Architecture Monitoring and Adaptation (IAMA) to proactively mitigate threats from legacy systems. This multi-network approach provides unparalleled flexibility and security, allowing ASKA to handle both local and external communications with tailored security strategies for different contexts.
The foundation of ASKA’s adaptive security model rests on the powerful synergy between its multi-agent AI system and its dynamic networking capabilities. The AI Agent(s), deployed within isolated execution environments, passively monitor user interactions via the Secure UI and actively analyze system-wide data (from the DTMS, Security Meshes, and the Decentralized Ledger). This out-of-band monitoring capability provides early threat detection and supports highly-granular, real-time adjustments to security policies and resource allocation. The AI Agent swarms, using their collective intelligence to detect anomalies and coordinate automated responses (such as isolation, containment, and self-healing), significantly enhancing ASKA’s ability to react to threats in real-time. Moreover, the AI Agent’s security insights inform the Automated Evolutionary Software Development System (AESDS), which continuously generates, tests, and deploys secure software updates, creating a self-evolving and adaptive security system that constantly strengthens itself against evolving threats. The integration of the AI Agent’s functions, both for user assistance and dynamic security management, enhances user trust and reduces the system’s operational overhead.
A purpose-built, integrated application development process completes ASKA’s ecosystem. The AI Agent acts as a secure, out-of-band guide for developers, assisting with code generation, security analysis, and deployment within the ASKA environment. It provides interactive tutorials and best practices, reducing development time and improving code quality, thereby fostering a secure development environment with continuous improvement. Developers create applications within isolated IES instances, leveraging ASKA’s APIs and capabilities for communication and data access. The AI Agent’s security insights, combined with the AESDS’s continuous monitoring and updating process, ensure that applications are built securely and remain protected against evolving threats, leveraging the flexibility of the mesh and multi-channel network for application-specific configurations while maintaining a high degree of security and trust. This fully integrated secure application development process eliminates many of the vulnerabilities typically found in traditional software development workflows. The Multi-Dimensional Audit Trail System (MDATS), integrating digital logs on the Decentralized Ledger with physical 3D microstructures, ensures complete transparency and accountability.
ASKA represents a paradigm shift in secure computing, addressing numerous vulnerabilities present in traditional architectures. Through hardware-enforced isolation, dynamic trust management, multi-agent AI, secure networking, and a fully integrated development process, ASKA provides a high-assurance platform, adapting to evolving threats and technological advancements for secure and efficient application development and deployment across diverse and potentially hostile environments for decades to come. Its uniquely designed and integrated multi-layered security architecture provides unprecedented levels of assurance, robustness, and adaptability not seen in any other existing system, enhancing its value greatly and making it a highly secure and versatile platform for various uses across multiple markets.